Abstract
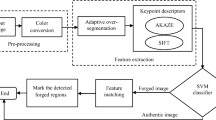
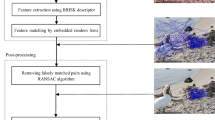
Due to the advancements in digital image processing and multimedia devices, the digital image can be easily tampered and presented as evidence in judicial courts, print media, social media, and for insurance claims. The most commonly used image tampering technique is the copy-move forgery (CMF) technique, where the region from the original image is copied and pasted in some other part of the same image to manipulate the original image content. The CMFD techniques may not provide robust performance after various post-processing attacks and multiple forged regions within the images. This article introduces a robust CMF detection technique to mitigate the aforementioned problems. The proposed CMF detection technique utilizes a fusion of speeded up robust features (SURF) and binary robust invariant scalable keypoints (BRISK) descriptors for CMF detection. The SURF features are robust against different post-processing attacks such as rotation, blurring, and additive noise. However, the BRISK features are considered as robust in the detection of the scale-invariant forged regions as well as poorly localized keypoints of the objects within the forged image. The fused features are matched using hamming distance and second nearest neighbor. The matched features grouped into clusters by applying density-based spatial clustering of applications with noise clustering algorithm. The random sample consensus technique is applied to the clusters to remove the remaining false matches. After some post-processing, the forged regions are detected and localized. The performance of the proposed CMFD technique is assessed using three standard datasets (i.e., CoMoFoD, MICC-F220, and MICC-F2000). The proposed technique surpasses the state-of-the-art techniques used for CMF detection in terms of true and false detection rates.






















Similar content being viewed by others
Availability of Data and Material
Please contact the authors for data requests.
References
Kessler, G.C.: An overview of steganography for the computer forensics examiner. Forensic Sci. Commun. 6(3), 1–27 (2004)
Nilizadeh, A.; Nilchi, A.R.N.: A novel steganography method based on matrix pattern and LSB algorithms in RGB images. In: 2016 1st Conference on Swarm Intelligence and Evolutionary Computation (CSIEC), Bam, Iran 2016, pp. 154–159. IEEE (2016)
Nilizadeh, A.; Mazurczyk, W.; Zou, C.; Leavens, G.T.: Information hiding in RGB images using an improved matrix pattern approach. In: 2017 IEEE Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), Honolulu, HI, USA 2017, pp. 1407–1415. IEEE (2017)
Rehman, A.; Saba, T.; Mahmood, T.; Mehmood, Z.; Shah, M.; Anjum, A.: Data hiding technique in steganography for information security using number theory. J. Inf. Sci. (2018). https://doi.org/10.1177/0165551518816303
Cox, I.J.; Miller, M.L.; Bloom, J.A.; Honsinger, C.: Digital Watermarking, vol. 53. Springer, Berlin (2002)
Nikolaidis, N.; Pitas, I.: Digital image watermarking: an overview. In: Proceedings IEEE International Conference on Multimedia Computing and Systems, Florence, Italy 1999, pp. 1–6. IEEE (1999)
Belk, R.W.: Extended self in a digital world. J. Consum. Res. 40(3), 477–500 (2013). https://doi.org/10.1086/671052
Qureshi, M.A.: A bibliography of pixel-based blind image forgery detection techniques. Sig. Process. Image Commun. 39, 46–74 (2015)
Asghar, K.; Habib, Z.; Hussain, M.: Copy-move and splicing image forgery detection and localization. Aust. J. Forensic Sci. 49, 281–307 (2017)
Tralic, D.; Zupancic, I.; Grgic, S.; Grgic, M.: CoMoFoD—new database for copy-move forgery detection. In: ELMAR, 2013 55th international symposium, Zadar, Croatia 2013, pp. 49–54. IEEE (2013)
Christlein, V.; Riess, C.; Jordan, J.; Riess, C.; Angelopoulou, E.: An evaluation of popular copy-move forgery detection approaches. Inf. Forensics Secur. IEEE Trans. 7, 1841–1854 (2012)
Muhammad, G.; Al-Hammadi, M.H.; Hussain, M.; Bebis, G.: Image forgery detection using steerable pyramid transform and local binary pattern. Mach. Vis. Appl. 25, 985–995 (2014)
Hayat, K.; Qazia, T.: Forgery detection in digital images via discrete wavelet and discrete cosine transforms. Comput. Electr. Eng. 62, 448–458 (2017)
Bay, H.; Ess, A.; Tuytelaars, T.; Gool, L.: Speeded-up robust features (SURF). Comput. Vis. Image Underst. 110(3), 346–359 (2008)
Bo, X.; Junwen, W.; Guangjie, L.; Yuewei, D.: Image copy-move forgery detection based on SURF. In: 2010 International Conference on Multimedia Information Networking and Security, Nanjing, Jiangsu, China 2010, pp. 889–892. IEEE (2010)
Pandey, R.C.; Singh, S.K.; Shukla, K.; Agrawal, R.: Fast and robust passive copy-move forgery detection using SURF and SIFT image features. In: 2014 9th International conference on industrial and information systems (ICIIS), Gwalior, India 2014, pp. 1–6. IEEE (2014)
Leutenegger, S.; Chli, M.; Siegwart, R.Y.: BRISK: Binary robust invariant scalable keypoints. In: IEEE International Conference on Computer Vision (ICCV), 2011, pp. 2548–2555. IEEE (2011)
Silva, E.; Carvalho, T.; Ferreira, A.; Rocha, A.: Going deeper into copy-move forgery detection: exploring image telltales via multi-scale analysis and voting processes. J. Vis. Commun. Image Represent. 29(5), 16–32 (2015). https://doi.org/10.1016/j.jvcir.2015.01.016
Mahmood, T.; Mehmood, Z.; Shah, M.; Khan, Z.: An efficient forensic technique for exposing region duplication forgery in digital images. Appl. Intell. 48(7), 1791–1801 (2018). https://doi.org/10.1007/s10489-017-1038-5
Mahmood, T.; Mehmood, Z.; Shah, M.; Saba, T.: A robust technique for copy-move forgery detection and localization in digital images via stationary wavelet and discrete cosine transform. J. Vis. Commun. Image Represent. 53(5), 202–214 (2018). https://doi.org/10.1016/j.jvcir.2018.03.015
Mahmood, T.; Irtaza, A.; Mehmood, Z.; Mahmood, M.T.: Copy–move forgery detection through stationary wavelets and local binary pattern variance for forensic analysis in digital images. Forensic Sci. Int. 279(10), 8–21 (2017). https://doi.org/10.1016/j.forsciint.2017.07.037
Mahmood, T.; Nawaz, T.; Mehmood, Z.; Khan, Z.; Shah, M.; Ashraf, R.: Forensic analysis of copy-move forgery in digital images using the stationary wavelets. In: 2016 6th International Conference on Innovative Computing Technology (INTECH), Dublin, Ireland 2016, pp. 578–583. IEEE (2016)
Mahmood, T.; Nawaz, T.; Ashraf, R.; Shah, M.; Khan, Z.; Irtaza, A.; Mehmood, Z.: A survey on block based copy move image forgery detection techniques. In: 2015 International Conference on Emerging Technologies (ICET), Peshawar, Pakistan 2015, pp. 1–6. IEEE (2015)
Fridrich, A.J.; Soukal, B.D.; Lukáš, A.J.: Detection of copy-move forgery in digital images. In: in Proceedings of Digital Forensic Research Workshop 2003. Citeseer (2003)
Lin, H.-J.; Wang, C.-W.; Kao, Y.-T.: Fast copy-move forgery detection. WSEAS Trans. Signal Process. 5(5), 188–197 (2009)
Ardizzone, E.; Bruno, A.; Mazzola, G.: Copy–move forgery detection by matching triangles of keypoints. IEEE Trans. Inf. Forensics Secur. 10(10), 2084–2094 (2015). https://doi.org/10.1109/TIFS.2015.2445742
Alkawaz, M.H.; Sulong, G.; Saba, T.; Rehman, A.: Detection of copy-move image forgery based on discrete cosine transform. Neural Comput. Appl. 30(1), 183–192 (2018). https://doi.org/10.1007/s00521-016-2663-3
Li, J.; Li, X.; Yang, B.; Sun, X.: Segmentation-based image copy-move forgery detection scheme. IEEE Trans. Inf. Forensics Secur. 10(3), 507–518 (2014). https://doi.org/10.1109/TIFS.2014.2381872
Warbhe, A.D.; Dharaskar, R.; Thakare, V.: A survey on keypoint based copy-paste forgery detection techniques. Procedia Comput. Sci. 78, 61–67 (2016). https://doi.org/10.1016/j.procs.2016.02.011
Farid, H.: Image forgery detection. IEEE Signal Process. Magazine 26(2), 16–25 (2009). https://doi.org/10.1109/MSP.2008.931079
Manu, V.; Mehtre, B.M.: Copy-move tampering detection using affine transformation property preservation on clustered keypoints. Signal Image Video Process. 12(3), 549–556 (2018). https://doi.org/10.1007/s11760-017-1191-7
Bi, X.; Pun, C.-M.; Yuan, X.-C.: Multi-level dense descriptor and hierarchical feature matching for copy–move forgery detection. Inf. Sci. 345, 226–242 (2016). https://doi.org/10.1016/j.ins.2016.01.061
Yuan, Y.; Zhang, Y.; Chen, S.; Wang, H.: Robust region duplication detection on log-polar domain using band limitation. Arab. J. Sci. Eng. 42(2), 559–565 (2017). https://doi.org/10.1007/s13369-016-2268-2
Zandi, M.; Mahmoudi-Aznaveh, A.; Talebpour, A.: Iterative copy-move forgery detection based on a new interest point detector. IEEE Trans. Inf. Forensics Secur. 11(11), 2499–2512 (2016). https://doi.org/10.1109/TIFS.2016.2585118
Yang, F.; Li, J.; Lu, W.; Weng, J.: Copy-move forgery detection based on hybrid features. Eng. Appl. Artif. Intell. 59(3), 73–83 (2017). https://doi.org/10.1016/j.engappai.2016.12.022
Pandey, R.C.; Agrawal, R.; Singh, S.K.; Shukla, K.K.: Passive copy move forgery detection using SURF, HOG and SIFT features. In: Proceedings of the 3rd International Conference on Frontiers of Intelligent Computing: Theory and Applications (FICTA) 2014 2015, pp. 659–666. Springer (2015)
Yu, L.; Han, Q.; Niu, X.: Feature point-based copy-move forgery detection: covering the non-textured areas. Multimed. Tools Appl. 75(2), 1159–1176 (2016). https://doi.org/10.1007/s11042-014-2362-y
Bin, Y.; Xingming, S.; Xianyi, C.; Zhang, J.; Xu, L.: An efficient forensic method for copy–move forgery detection based on DWT-FWHT. Radioengineering 22(4), 1098–1105 (2013)
Mikolajczyk, K.; Schmid, C.: A performance evaluation of local descriptors. IEEE Trans. Pattern Anal. Mach. Intell. 27(10), 1615–1630 (2005). https://doi.org/10.1109/TPAMI.2005.188
Juan, L.; Gwun, O.: A comparison of sift, pca-sift and surf. Int. J. Image Process. (IJIP) 3(4), 143–152 (2009)
Fahim, A.; Saake, G.; Salem, A.; Torkey, F.; Ramadan, M.: Improved DBSCAN for spatial databases with noise and different densities. Comput. Sci. Telecommun. 3, 53–60 (2009)
Ester, M.; Kriegel, H.-P.; Sander, J.; Xu, X.: A density-based algorithm for discovering clusters in large spatial databases with noise. In: Kdd 1996, vol. 34, pp. 226–231 (1996)
Fischler, M.A.; Bolles, R.C.: Random sample consensus: a paradigm for model fitting with applications to image analysis and automated cartography. Commun. ACM 24(6), 381–395 (1981). https://doi.org/10.1145/358669.358692
Amerini, I.; Ballan, L.; Caldelli, R.; Del Bimbo, A.; Serra, G.: A sift-based forensic method for copy–move attack detection and transformation recovery. IEEE Trans. Inf. Forensics Secur. 6(3), 1099–1110 (2011). https://doi.org/10.1109/TIFS.2011.2129512
Cozzolino, D.; Poggi, G.; Verdoliva, L.: Efficient dense-field copy–move forgery detection. IEEE Trans. Inf. Forensics Secur. 10(11), 2284–2297 (2015). https://doi.org/10.1109/TIFS.2015.2455334
Thampi, S.M.; Gelbukh, A.; Mukhopadhyay, J.: Advances in Signal Processing and Intelligent Recognition Systems. Springer, Berlin (2014)
Chen, C.-C.; Lu, W.-Y.; Chou, C.-H.: Rotational copy-move forgery detection using SIFT and region growing strategies. Multimed. Tools Appl. (2019). https://doi.org/10.1007/s11042-019-7165-8
Abdel-Basset, M.; Manogaran, G.; Fakhry, A.E.; El-Henawy, I.: 2-Levels of clustering strategy to detect and locate copy-move forgery in digital images. Multimed. Tools Appl. 1, 1–19 (2018). https://doi.org/10.1007/s11042-018-6266-0
Soni, B.; Das, P.K.; Thounaojam, D.M.: Geometric transformation invariant block based copy-move forgery detection using fast and efficient hybrid local features. J. Inf. Secur. Appl. 45, 44–51 (2019). https://doi.org/10.1016/j.jisa.2019.01.007
Yang, B.; Sun, X.; Guo, H.; Xia, Z.; Chen, X.: A copy-move forgery detection method based on CMFD-SIFT. Multimed. Tools Appl. 77(1), 837–855 (2018). https://doi.org/10.1007/s11042-016-4289-y
Popescu, A.C.; Farid, H.: Exposing digital forgeries by detecting traces of resampling. IEEE Trans. Signal Process. 53(2), 758–767 (2005). https://doi.org/10.1109/TSP.2004.839932
Soni, B.; Das, P.K.; Thounaojam, D.M.: Improved block-based technique using SURF and FAST keypoints matching for copy-move attack detection. In: 2018 5th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India 2018, pp. 197–202. IEEE (2018)
Li, J.; Li, X.; Yang, B.; Sun, X.: Segmentation-based image copy-move forgery detection scheme. IEEE Trans. Inf. Forensics Secur. 10(3), 507–518 (2015). https://doi.org/10.1109/TIFS.2014.2381872
Zhong, J.; Gan, Y.; Young, J.; Huang, L.; Lin, P.: A new block-based method for copy move forgery detection under image geometric transforms. Multimed. Tools Appl. 76(13), 14887–14903 (2017). https://doi.org/10.1007/s11042-016-4201-9
Amerini, I.; Ballan, L.; Caldelli, R.; Del Bimbo, A.; Del Tongo, L.; Serra, G.: Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Sig. Process. Image Commun. 28(6), 659–669 (2013). https://doi.org/10.1016/j.image.2013.03.006
Soni, B.; Das, P.K.; Thounaojam, D.M.: multiCMFD: fast and efficient system for multiple copy-move forgeries detection in image. In: Proceedings of the 2018 International Conference on Image and Graphics Processing 2018, pp. 53–58. ACM (2018)
Muzaffer, G.; Ulutas, G.: A fast and effective digital image copy move forgery detection with binarized SIFT. In: 2017 40th International Conference on Telecommunications and Signal Processing (TSP), Barcelona, Spain 2017, pp. 595–598. IEEE (2017)
Author information
Authors and Affiliations
Contributions
MB, HAH, ZM, TS, MR have authors contributed equally to this work.
Corresponding author
Ethics declarations
Conflict of interest
All the authors declare no conflict of interest.
Rights and permissions
About this article
Cite this article
Bilal, M., Habib, H.A., Mehmood, Z. et al. Single and Multiple Copy–Move Forgery Detection and Localization in Digital Images Based on the Sparsely Encoded Distinctive Features and DBSCAN Clustering. Arab J Sci Eng 45, 2975–2992 (2020). https://doi.org/10.1007/s13369-019-04238-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-019-04238-2