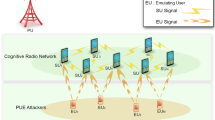
Abstract
Cognitive radio networks (CRNs) are being envisioned to drive the next generation Ad hoc wireless networks due to their ability to provide communications resilience in continuously changing environments through the use of dynamic spectrum access. Conventionally CRNs are dependent upon the information gathered by other secondary users to ensure the accuracy of spectrum sensing making them vulnerable to security attacks leading to the need of security mechanisms like cryptography and trust. However, a typical cryptography based solution is not a viable security solution for CRNs owing to their limited resources. Effectiveness of trust based approaches has always been, in question, due to credibility of secondary trust resources. Game theory with its ability to optimize in an environment of conflicting interests can be quite a suitable tool to manage an ad hoc network in the presence of autonomous selfish/malevolent/malicious and attacker nodes. The literature contains several theoretical proposals for augmenting game theory in the ad hoc networks without explicit/detailed implementation. This paper implements a game theory based solution in MATLAB-2015 to secure the CRN environment and compares the obtained results with the traditional approaches of trust and cryptography. The simulation result indicates that as the time progresses the game theory performs much better with higher throughput, lower jitter and better identification of selfish/malicious nodes.
Graphical Abstract












Similar content being viewed by others
References
Mitola III, J. (2000). Cognitive radio: An integrated agent architecture for software defined radio. Ph.D. Thesis, Royal Institute of Technology (KTH), Sweden.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Akyildiz, I. F., et al. (2006). NeXt generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks, 50, 2127–2159.
Wei, Z., Mallik, R. K. & Khaled, L. (2008). Cooperative spectrum sensing optimization in cognitive radio networks. In IEEE international conference on communications (pp. 3411–3415. Beijing.
Yang, G., Wang, J., Luo, J., Wen, O. Y., Li, H., Li, Q., et al. (2016). Cooperative spectrum sensing in heterogeneous cognitive radio networks based on normalized energy detection. IEEE TVT, 65(3), 1452–1463.
Liu, Y., Zhong, Z., Wang, G., & Hu, D. (2015). Cyclostationary detection based spectrum sensing for cognitive radio networks. Journal of Communications, 10(1), 74–79.
Clancy, T. C. and Nathan Goergen,” Security in Cognitive Radio Networks: Threats and Mitigation” published in 3rd International Conference on Cognitive Radio Oriented Wireless Networks and Communications (CrownCom 2008).
Attar, H., Tang, A., Vasilikos, A. V., Yu, F. R., & Leung, V. C. M. (2013). Security challenges in cognitive radio networks: Solutions and future research directions. Proceedings of the IEEE, 100(12), 3172–3186.
Tang, H., Wei, Z., Yu, F. R., & Mason, P. (2014). Security enhancements for spectrum sensing and data transmission in cognitive radio mobile ad hoc networks (CR-MANETs). In NATO IST symposium on cognitive radio and future networks, Amsterdam, Netherlands.
Wei, Y., Leung, H., Wenqing, C., Siyue, C., & Bokan, C. (2012). Participation in repeated cooperative spectrum sensing: A game theoritic perspective. IEEE Transactions on Wireless Communications, 11(3), 1000–1011.
Wang, Y., Yu, F. R., Tang, H., & Huang, M. (2013). A mean field game theoretic approach for security enhancements in mobile ad hoc networks. In IEEE transaction on wireless communication.
Wang, B., Wu, Y., Liu, K. J. R., & Clancy, T. C. (2011). An anti-jamming stochastic game for cognitive radio networks. IEEE Journal on Selected Areas in Communications, 29(4), 877–889.
Saad, W., Han, Z., Debbah, M., Hjorungnes, A., & Basar, T. (2009). Coalitional games for distributed collaborative spectrum sensing in cognitive radio networks. In Proceedings of the IEEE INFOCOM.
Srivastava, V., Neel, J., Mackenzie, A. B., Menon, R., Dasilva, L. A., Hicks, J. E., et al. (2005). Using game theory to analyze wireless ad hoc networks. IEEE Communications Surveys and Tutorials, 7(4), 46–56.
Wang, B., Liu, K. J., & Clancy, T. C. (2010). Evolutionary cooperative spectrum sensing game: How to collaborate. IEEE Transactions on Communication, 58(3), 890–900.
Wei, Y., & Liu, K. J. R. (2007). Game theoretic analysis of cooperation stimulation and security in autonomous mobile ad hoc networks. IEEE Transaction on Mobile Computing, 6(5), 507–521.
Yan, C., & Liu, K. J. R. (2011). Indirect reciprocity game modelling for cooperation stimulation in cognitive radio network. IEEE Transaction on Communications, 59(1), 159–168.
Afghah, F., Costa, M., Razi, A., Abedi, A., & Ephremides, A. (2013). A reputation-based stackelberg game approach for spectrum sharing with cognitive cooperation. In IEEE CDC.
Mehta, S., Kwak, K. S. (2009). Game theory and cognitive radio based wireless networks. In A. Håkansson, & N. T. Nguyen, R. L. Hartung, R. J. Howlett, L. C. Jain (Eds.), Agent and multi-agent systems: Technologies and applications. KES-AMSTA 2009. Lecture notes in computer SCIENCE (vol. 5559). New York: Springer.
Hao, D., Ren, Y., Sakurai, K. (2011). A game theory-Based surveillance mechanism against suspicious insiders in MANETs. In L. Chen, M. Yung (Eds.), Trusted systems. INTRUST 2010. Lecture notes in computer science (vol. 6802). Springer.
Rafsanjani, M. K., Aliahmadipour, L., & Javidi, M. M. (2010). An optimal method for detecting internal and external intrusion in MANET. Communications in Computer and Information Science, 120, 71–82.
Li, Z., & Shen, H. (2012). Game-theoretic analysis of cooperation incentive strategies in mobile ad hoc networks. In IEEE Transactions on Mobile Computing, 11, 8.
Bennaceur, J., & Idoudi, H., & Saidane, L. (2017). Game-based secure sensing for the CRN. https://doi.org/10.1109/iwcmc.2017.7986604.
Avinash, K. D., Skeath, S., & David, H. R. (2010). Games of strategy (3rd ed.). New York: W.W. Norton & Company.
Paterson, K. G., & Price, G. (2003). A comparison between traditional public key infrastructures and identity-based cryptography. In Information security technical report, 8(3), 57–72. Amsterdam: Elsevier Ltd.
Chen, R., Park, J.-M., & Reed, J. (2008). Defense against primary user emulation attacks in cognitive radio networks. IEEE Journal on Selected Areas in Communications, 26, 25–37.
Yu, F. R., & Tang, H. (2010). Distributed node selection for threshold key management with intrusion detection in mobile ad hoc networks. New York: Springer.
Liu, Y., Ning, P., & Dai, H. (2010). Authenticating primary users’ signals in cognitive radio networks via integrated cryptographic and wireless link signatures. In 2010 IEEE symposium on security and privacy (pp. 286–301).
Liu, F., Wang, X., & Tang, H. (2011). Robust physical layer authentication using inherent properties of channel impulse response. In Proceedings of the IEEE Military communications conference (MILCOM).
Refaei, M. T., DaSilva, L. A., Eltoweissy, M., & Nadeem, T. (2010). Adaptation of reputation management systems to dynamic network conditions in ad hoc networks. IEEE Transactions on Computers, 59(5), 707–719.
Zhang, N., Lu, N., Lu, R., Mark, J. W., Xuemin (Sherman) Shen. (2012). Energy-efficient and trust-aware cooperation in cognitive radio networks. In IEEE ICC.
Jana, Shraboni, Zeng, Kai, Cheng, Wei, & Mohapatra, Prasant. (2013). Trusted collaborative spectrum sensing for mobile cognitive radio networks. IEEE Transactions on Information Forensics and Security, 8(9), 1497–1507.
Jana, S., Zeng, K., Cheng, W., & Mohapatra, P. (2013). Trusted collaborative spectrum sensing for mobile cognitive radio networks. IEEE Transactions on Information Forensics and Security, 8(9), 1497–1507.
Hyder, Chowdhury S., Grebur, Brendan, Xiao, Li, & Ellison, Max. (2014). Adaptive reputation based clustering against spectrum sensing data falsification attacks. IEEE Transactions on Mobile Computing, 13(8), 1707–1719.
Pei, Q., Ma, L., Li H., Li, Z., Yan, D., & Li, Z. (2015). Reputation-based coalitional games for spectrum allocation in distributed cognitive radio networks. In Communication and information systems security symposium.
Naveed, A., & Kanhere, S. S. (2006). Security vulnerabilities in channel assignment of multi-radio multi-channel wireless mesh networks. In Proceedings of IEEE conference in global telecommunications, GLOBECOM (pp. 1–5).
Kaligineedi, P., Khabbazian, M., & Bhargava, V. K. (2008). Secure cooperative sensing techniques for cognitive radio systems. In ICC. IEEE international conference on communications (pp. 3406–3410).
Akyildiz, I. F., Lee, W. Y., Vuran, M. C., & Mohanty, S. (2008). A survey on spectrum management in cognitive radio networks. In IEEE Communications magazine (pp. 40–48).
Zhang, X., & Li, C. (2009b). The security in cognitive radio networks: A survey. In Proceedings of international conference on wireless communications and mobile computing, Leipzig, Germany (pp. 309–313).
Jithesh, M., & Harish Kumar, C. (2015). Malicious user detection in cognitive radio networks. International Journal of Science and Research (IJSR), 4(8), 496–501.
Parvin, S., Hussain, F. K., Hussain, O. K., Han, S., Tian, B., & Chang, E. (2012). Cognitive radio network security: A survey. Journal of Network and Computer Applications., 35, 1691–1708.
Alrabaee, S., Agarwal, A., Anand, D., & Khasawneh, M. (2012). Game theory for security in cognitive radio networks. In The proceedings of international conference on advances in mobile network, communication and its applications.
Bhattacharjee, S., Sengupta, S., & Chatterjee, M. (2013). Vulnerabilities in cognitive radio networks: A survey. Computer Communications, 36, 1387–1398.
Hlavacek, D., & Chang, J. M. (2014). A layered approach to cognitive radio network security: A survey. Computer Networks, 75, 414–436.
Marchang, Ningrinla, & Rajkumari, Roshni. (2016). Modelling and mitigating spectrum sensing non-cooperation attack in cognitive radio network. International Journal of Ad Hoc and Ubiquitous Computing, 1, 1. https://doi.org/10.1504/IJAHUC.2016.
Amjad, M., & Faisal, M. (2015). Opportunistic spectrum utilization by cognitive radio networks: Challenges and solutions. Electronic Theses and Dissertations (pp. 49).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix





Rights and permissions
About this article
Cite this article
Poonam, Nagpal, C.K. A Game Theory Based Solution for Security Challenges in CRNs. 3D Res 9, 11 (2018). https://doi.org/10.1007/s13319-018-0161-3
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13319-018-0161-3