Abstract
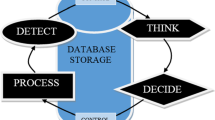
Nowadays, the number of software vulnerabilities incidents and the loss due to occurrence of software vulnerabilities are growing exponentially. The current existing security strategies, the vulnerability detection and remediating approaches are not intelligent, automated, self-managed and not competent to combat against the vulnerabilities and security threats, and to provide secured self-managed software environment to the organizations. Hence, there is a strong need to devise an intelligent and automated approach to optimize security and prevent the occurrence of vulnerabilities or mitigate the vulnerabilities. The autonomic computing is a nature-inspired and self-management-based computational model. In this paper, an autonomic-computing-based integrated framework is proposed to detect, fire the trigger of alarm, assess, classify, prioritize, mitigate and manage the software vulnerability automatically. The proposed framework uses a knowledge base and inference engine, which automatically takes the remediating actions on future occurrence of software security vulnerabilities through self-configuration, self-healing, self-prevention and self-optimization as per the needs. The proposed framework is beneficial to industry and society in various aspects because it is an integrated, cross-concern and intelligent framework and provides more secured self-managed environment to the organizations. The proposed framework reduces the security risks and threats, and also monetary and reputational loss. It can be embedded easily in existing software and incorporated or implemented as an inbuilt integral component of the new software during software development.





Similar content being viewed by others
References
Agrawal A, Chandra S and Khan R A 2009 An efficient measurement of object oriented design vulnerability. In: Proceedings of the International Conference on Availability, Reliability and Security, ARES’09
Dai H, Murphy C and Kaiser G 2010 Configuration fuzzing for software vulnerability detection. In: Proceedings of the International Conference on Availability, Reliability and Security, pp. 525–530
Kumar M 2016 A paradigm shift towards incorporation and exploration of autonomic computing for software vulnerability detection, mitigation and management. Communicated to Informatica
Sharma A, Chauhan S and Grover P S 2011 Autonomic computing: paradigm shift for software development. CSI Commun. 35(6): 16–18
Howard M and Lipner S 2003 Inside the Windows security push. IEEE Security Privacy 1(1): 57–61
Alhazmi O H, Woo S W and Malaiya Y K 2006 Security vulnerability categories in major software systems. In: Proceedings of Communication, Network, and Information Security 2006, 138–143
Bansiya J and Davis C G 2002 A hierarchical model for object-oriented design quality assessment. IEEE Trans. Softw. Eng. 28: 4–17
Bansiya J 1997 A hierarchical model for quality assessment of object-oriented designs. PhD Thesis, University of Alabama in Huntsville
Bishop M and Bailey D 1996 A critical analysis of vulnerability taxonomies. Technical Report, CSE-96-11, Department of Computer Science at the University of California at Davis, September
Bishop M 2003 Computer security: art and science. Boston: Addison-Wesley
Byres D and Shahmehri N 2007 Design of a process for software security. In: Proceedings of the Second International Conference on Availability, Reliability and Security (ARES’07), 10–13 April, IEEE Press, Vienna, pp. 301–309
McGraw G 2006 Software security: building security. Upper Saddle River, NJ: Addison-Wesley
Meland P H and Jensen J 2008 Secure software design in practice. In: Proceedings of the Third International Conference on Availability, Reliability and Security (ARES’09), 4–7 March, IEEE Press, Fukuoka, Japan, pp. 1164–1171, doi:10.1109/ARES.2008.48
Walsh L 2003 Trustworthy yet? Inf. Security Mag. February
Kannan K, Telang R and Xu H 2004 Economic analysis of the market for software vulnerability. In: Proceedings of the 37th Hawali International Conference on System Sciences
Sahadeva K, Kumar Y S and Sharma A 2012 A new SDLC framework with autonomic computing elements. Int. J. Comput. Appl. 54(3): 17–23
Gilliam D P, Wolfe T L, Sherif J S and Bishop M 2003 Softawre secuirty checklist for the software life cycle. In: Proceedings of the Twelfth IEEE International Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETIC’03), IEEE Press, Allahabad, India
Ren J, Cai B, He H and Hu C 2011 A method for detecting software vulnerabilities based on clustering and model analyzing. J. Comput. Inf. Syst. 7(4): 1065–1073
Wang Y, Wang Y and Ren J 2011 Software vulnerabilities detection using rapid density-based clustering. J. Inf. Comput. Sci. 8(14): 3295–3302
Alves-Foss J and Barbosa S 1995 Assessing computer security vulnerability. ACM SIGOPS Oper. Syst. Rev. 29: 3–13
Wang C and Wulf W A 1997 A framework for security measurement. In: Proceedings of the National Information System Security Conference (NISSC’97), pp. 522–533
Gilliam D, Powell J, Bishop J and Kelly M 2001 Reducing software security risk through an integrated approach. In: Proceedings of the NASA IV&V Symposium, September 4–7
Butler S A 2002 Security attribute evaluation method: a cost–benefit approach. In: Proceedings of the International Conference on Software Engineering (ICSE 2002), ACM Press, Orlando, Florida, pp. 232–240, doi:10.1145/581339.581370
Halkidis S T Chatzigeorgiou A and Stephanides G 2004 A qualitative evaluation of security patterns. In: Proceedings of ICICS 2004, Lecture Notes in Computer Science 3269, Springer-Verlag, Málaga, Spain, pp. 132–144
Hallberg J, Hunstad A and Peterson M 2005 A framework for system security assessment. In: Proceedings of the 6th Annual IEEE System, Man and Cybernetics (SMC) Information Assurance Workshop, IEEE Press, Budapest, pp. 224–231, doi:10.1109/IAW.2005.1495956
Alhazmi O A, Malaiya Y K and Ray I 2005 Security vulnerabilities in software systems: a quantitative perspective. In: Proceedings of Data and Applications Security 2005, Lecture Notes in Computer Science 3654, pp. 281–294, doi:10.1007/11535706
Chandra S, Khan R A and Agrawal A 2009 Security estimation framework: design phase perspective. In: Proceedings of the Sixth International Conference on Information Technology, New Generations, ITNG 2009, 27–29 April, IEEE Computer Society, pp. 254–259
Chen Y, Boehm B and Sheppard L 2007 Value driven security threat modeling based on attack path analysis. In: Proceedings of the 40th Annual Hawaii International Conference on System Sciences (HICSS’07), 3–6 January, IEEE Press, Big Island, Hawaii, p. 280
Chowdhury I, Chan B and Zulkernine M 2008 Security metrics for source code structures. In: Proceedings of the Fourth International Workshop on Software Engineering for Secure Systems, Leipzig, Germany: ACM
Alshammari B, Fidge C and Corney D 2009 Security metrics for object-oriented class designs. In: Proceedings of the 9th Quality Software International Conference, QSIC ‘09,, 24–25 August, pp. 11–20, doi:10.1109/QSIC.2009.11
Agrawal A and Khan R A 2009 An algorithm to measure attribute vulnerability ratio of an object oriented design. Int. J. Recent Trends Eng. 2(3): 61–63
Alkussayer A and Allen W H 2010 A scenario-based framework for the security evaluation of software architecture. In: Proceedings of the International Conference on Computer Science and Information Technology (ICCSIT’10), 9–11 July, IEEE Press, Chengdu, China, pp. 687–695
Alberts C, Allen J and Stoddard R 2010 Integrated measurement and analysis framework for software security. Technical Report, CMU/SEI-2010-TN-025, CERT® Program, Software Engineering Institute, http://www.sei.cmu.edu/library/abst
Agrawal A and Khan R A 2010 A vulnerability metric for the design phase of object oriented software. In: Proceedings of the Conference on Communications in Computer and Information Science
Agrawal A and Khan R A 2011 Assessing and improving encapsulation for minimizing vulnerability of an object oriented design. In: Communication in Computer and Information Science, vol. 250, Springer-Verlag, pp. 531–533
Alhazmi O H, Malaiya Y K and Ray I 2015 Measuring, analyzing and predicting security vulnerabilities in software systems. Comput. Security 26(3): 219–228
Khan K M and Jun Han J 2002 Composing security-aware software. IEEE Softw. 19(1): 34–41
Wang J A, Wang H, Guo M, Zhou L and Camargo J 2010 Ranking attacks based on vulnerability analysis. In: Proceedings of the 43rd Hawaii International Conference on System Sciences (HICSS’10), 5–8 January, IEEE Press, Hawai, USA, pp. 1–10
Agrawal A and Khan R A 2011 A framework for vulnerability minimization—object oriented design perspective. In: Proceedings of the 2nd International Conference on Computer and Communication Technology, ICCCT, 15–17 September, IEEE Computer Society, pp. 499–504
Agrawal A and Khan R A 2009 A framework to detect and analyze software vulnerabilities—development phase perspective. Int. J. Recent Trends Eng. 2(2): 82–84
Ahuja K and Dangey H 2014 Autonomic computing: an emerging perspective and issues. In: Proceedings of the International Conference on Issues and Challenges in Intelligent Computing Techniques (ICICT), Ghaziabad, pp. 471–475
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kumar, M., Sharma, A. An integrated framework for software vulnerability detection, analysis and mitigation: an autonomic system. Sādhanā 42, 1481–1493 (2017). https://doi.org/10.1007/s12046-017-0696-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12046-017-0696-7