Abstract
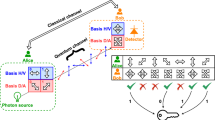
Quantum key distribution (QKD) provides a physical-based way to conciliate keys between remote users securely. Simulation is an essential method for designing and optimizing QKD systems. We develop a universal simulation framework based on quantum operator descriptions of photon signals and optical devices. The optical devices can be freely combined and driven by the photon excitation events, which make it appropriate for arbitrary QKD systems in principle. Our framework focuses on realistic characters of optical devices and system structures. The imperfections of the devices and the non-local properties of a quantum system are taken into account when modeling. We simulate the single-photon and Hong-Ou-Mandel (HOM) interference optical units, which are fundamental of QKD systems. The results using this event-driven framework agree well with the theoretical results, which indicate its feasibility for QKD.
Similar content being viewed by others
References
Bennett C H, Brassard G. Quantum cryptography: public key distribution and coin tossing. In: Proceedings of Conference on Computers, Systems and Signal Processing, Bangalore, 175
Ekert A K. Quantum cryptography based on Bell’s theorem. Phys Rev Lett, 1991, 67: 661–663
Gottesman D, Lo H K, Lutkenhaus N, et al. Security of quantum key distribution with imperfect devices. In: Proceedings of International Symposium on Information Theory, Chicago, 2004. 136
Scarani V, Bechmann-Pasquinucci H, Cerf N J, et al. The security of practical quantum key distribution. Rev Mod Phys, 2009, 81: 1301–1350
Wang X B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys Rev Lett, 2005, 94: 230503
Lo H K, Ma X, Chen K. Decoy state quantum key distribution. Phys Rev Lett, 2005, 94: 230504
Tomamichel M, Renner R. Uncertainty relation for smooth entropies. Phys Rev Lett, 2011, 106: 110506
Laing A, Scarani V, Rarity J G, et al. Reference-frame-independent quantum key distribution. Phys Rev A, 2010, 82: 012304
Yin Z Q, Wang S, Chen W, et al. Reference-free-independent quantum key distribution immune to detector side channel attacks. Quantum Inf Process, 2014, 13: 1237–1244
Lo H K, Curty M, Qi B. Measurement-device-independent quantum key distribution. Phys Rev Lett, 2012, 108: 130503
Curty M, Xu F, Cui W, et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nat Commun, 2014, 5: 3732
Sasaki T, Yamamoto Y, Koashi M. Practical quantum key distribution protocol without monitoring signal disturbance. Nature, 2014, 509: 475–478
Lim C C W, Curty M, Walenta N, et al. Concise security bounds for practical decoy-state quantum key distribution. Phys Rev A, 2014, 89: 022307
Rusca D, Boaron A, Grünenfelder F, et al. Finite-key analysis for the 1-decoy state QKD protocol. Appl Phys Lett, 2018, 112: 171104
Lucamarini M, Yuan Z L, Dynes J F, et al. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature, 2018, 557: 400–403
Ma X, Zeng P, Zhou H. Phase-matching quantum key distribution. Phys Rev X, 2018, 8: 031043
Wang X B, Yu Z W, Hu X L. Twin-field quantum key distribution with large misalignment error. Phys Rev A, 2018, 98: 062323
Cui C, Yin Z Q, Wang R, et al. Twin-field quantum key distribution without phase postselection. Phys Rev Appl, 2019, 11: 034053
Peng C Z, Zhang J, Yang D, et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys Rev Lett, 2007, 98: 010505
Dixon A R, Yuan Z L, Dynes J F, et al. Gigahertz decoy quantum key distribution with 1 Mbit/s secure key rate. Opt Express, 2008, 16: 18790
Wang S, Yin Z Q, Chen W, et al. Experimental demonstration of a quantum key distribution without signal disturbance monitoring. Nat Photon, 2015, 9: 832–836
Wang C, Song X T, Yin Z Q, et al. Phase-reference-free experiment of measurement-device-independent quantum key distribution. Phys Rev Lett, 2015, 115: 160502
Takesue H, Sasaki T, Tamaki K, et al. Experimental quantum key distribution without monitoring signal disturbance. Nat Photon, 2015, 9: 827–831
Yin H L, Chen T Y, Yu Z W, et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys Rev Lett, 2016, 117: 190501
Comandar L C, Lucamarini M, Fröohlich B, et al. Quantum key distribution without detector vulnerabilities using optically seeded lasers. Nat Photon, 2016, 10: 312–315
Liao S K, Cai W Q, Liu W Y, et al. Satellite-to-ground quantum key distribution. Nature, 2017, 549: 43–47
Fröohlich B, Lucamarini M, Dynes J F, et al. Long-distance quantum key distribution secure against coherent attacks. Optica, 2017, 4: 163–167
Boaron A, Boso G, Rusca D, et al. Secure quantum key distribution over 421 km of optical fiber. Phys Rev Lett, 2018, 121: 190502
Wang S, Chen W, Yin Z Q, et al. Practical gigahertz quantum key distribution robust against channel disturbance. Opt Lett, 2018, 43: 2030
Wang S, He D Y, Yin Z Q, et al. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys Rev X, 2019, 9: 021046
Minder M, Pittaluga M, Roberts G L, et al. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat Photon, 2019, 13: 334–338
Zhong X, Hu J, Curty M, et al. Proof-of-principle experimental demonstration of twin-field type quantum key distribution. Phys Rev Lett, 2019, 123: 100506
Liu Y, Yu Z W, Zhang W, et al. Experimental twin-field quantum key distribution through sending or not sending. Phys Rev Lett, 2019, 123: 100505
Chen J P, Zhang C, Liu Y, et al. Sending-or-not-sending with independent lasers: secure twin-field quantum key distribution over 509 km. 2020, 124: 070501
Lo H K, Curty M, Tamaki K. Secure quantum key distribution. Nat Photon, 2014, 8: 595–604
Yoshino K, Fujiwara M, Nakata K, et al. Quantum key distribution with an efficient countermeasure against correlated intensity fluctuations in optical pulses. npj Quantum Inf, 2018, 4: 8
Angrisani L, D’Arco M. Modeling timing jitter effects in digital-to-analog converters. IEEE Trans Instrum Meas, 2008, 58: 330–336
Wang F X, Chen W, Li Y P, et al. Non-Markovian property of afterpulsing effect in single-photon avalanche detector. J Lightw Technol, 2016, 34: 3610–3615
Zhang J, Itzler M A, Zbinden H, et al. Advances in InGaAs/InP single-photon detector systems for quantum communication. Light Sci Appl, 2015, 4: e286
Fan-Yuan G J, Wang C, Wang S, et al. Afterpulse analysis for quantum key distribution. Phys Rev Appl, 2018, 10: 064032
Buhari A, Zukarnain Z A, Subramaniam S K, et al. An efficient modeling and simulation of quantum key distribution protocols using OptiSystem™. In: Proceedings of IEEE Symposium on Industrial Electronics and Applications, 2012. 84–89
Mailloux L O, Morris J D, Grimaila M R, et al. A modeling framework for studying quantum key distribution system implementation nonidealities. IEEE Access, 2015, 3: 110–130
Archana B, Krithika S. Implementation of bb84 quantum key distribution using optsim. In: Proceedings of the 2nd International Conference on Electronics and Communication Systems (ICECS), 2015. 457–460
Ma X, Qi B, Zhao Y, et al. Practical decoy state for quantum key distribution. Phys Rev A, 2005, 72: 012326
Krenn M, Malik M, Fickler R, et al. Automated search for new quantum experiments. Phys Rev Lett, 2016, 116: 090405
Varga A. Using the OMNeT++ discrete event simulation system in education. IEEE Trans Educ, 1999, 42: 11
Varga A. Discrete event simulation system. In: Proceedings of the European Simulation Multiconference (ESM’001), 2001. 1–7
Varga A, Hornig R. An overview of the OMNeT++ simulation environment. In: Proceedings of the 1st International Conference on Simulation Tools and Techniques for Communications, Networks and Systems & Workshops, 2008. 1–10
Hong C K, Ou Z Y, Mandel L. Measurement of subpicosecond time intervals between two photons by interference. Phys Rev Lett, 1987, 59: 2044
Glauber R J. Coherent and incoherent states of the radiation field. Phys Rev, 1963, 131: 2766–2788
Jones R C. A new calculus for the treatment of optical systems. I. description and discussion of the calculus. J Opt Soc Am, 1941, 31: 488–493
Metropolis N, Ulam S. The Monte Carlo method. J Am Stat Assoc, 1949, 44: 335–341
Zehnder L Z. Ein neuer interferenzrefraktor. Instrumentenkunde, 1891, 11: 275–285
Mach L. Ueber einen interferenzrefraktor. Zeitschrift für Instrumentenkunde, 1892, 12: 89
Acknowledgements
This work was supported by National Key Research and Development Program of China (Grant No. 2018YFA0306400), National Natural Science Foundation of China (Grant Nos. 61627820, 61675189, 61622506, 61822115), Anhui Initiative in Quantum Information Technologies (Grant No. AHY030000). We also appreciate Dr. Xuebi AN and Yuyang DING of Anhui Qasky, Co. Ltd. for helpful discussion.
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Fan-Yuan, GJ., Chen, W., Lu, FY. et al. A universal simulating framework for quantum key distribution systems. Sci. China Inf. Sci. 63, 180504 (2020). https://doi.org/10.1007/s11432-020-2886-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-020-2886-x