Abstract
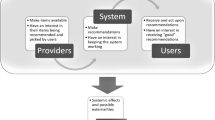
With the development of science and technology, the popularity of smart phones has made exponential growth in mobile phone application market. How to help users to select applications they prefer has become a hot topic in recommendation algorithm. As traditional recommendation algorithms are based on popularity and download, they inadvertently fail to recommend the desirable applications. At the same time, many users tend to pay more attention to permissions of those applications, because of some privacy and security reasons. There are few recommendation algorithms which take account of apps’ permissions, functionalities and users’ interests altogether. Some of them only consider permissions while neglecting the users’ interests, others just perform linear combination of apps’ permissions, functionalities and users’ interests to implement top-N recommendation. In this paper, we devise a recommendation method based on both permissions and functionalities. After demonstrating the correlation of apps’ permissions and users’ interests, we design an app risk score calculating method ARSM based on app-permission bipartite graph model. Furthermore, we propose a novel matrix factorization algorithm MFPF based on users’ interests, apps’ permissions and functionalities to handle personalized app recommendation. We compare our work with some of the state-of-the-art recommendation algorithms, and the results indicate that our work can improve the recommendation accuracy remarkably.









Similar content being viewed by others
References
Baeza-Yates, R., Jiang, D., Silvestri, F., Harrison, B.: Predicting the next app that you are going to use Proceedings of the 8th ACM International Conference on Web Search and Data Mining, pp 285–294. ACM (2015)
Chia, P.H., Yamamoto, Y., Asokan, N.: Is this app safe?: A large scale study on application permissions and risk signals Proceedings of the 21st International Conference on World Wide Web, pp 311–320. ACM (2012)
Guo, G., Zhang, J., Yorke-Smith, N.: Trustsvd: Collaborative filtering with both the explicit and implicit influence of user trust and of item ratings AAAI, pp 123–129 (2015)
Huang, J., Peng, M., Wang, H., Cao, J., Gao, W., Zhang, X.: A probabilistic method for emerging topic tracking in microblog stream. World Wide Web, pp. 1–26 (2016)
Koren, Y.: Factorization meets the neighborhood: A multifaceted collaborative filtering model Proceedings of the 14th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp 426–434. ACM (2008)
Koren, Y., Bell, R., Volinsky, C., et al.: Matrix factorization techniques for recommender systems. Computer 42(8), 30–37 (2009)
Li, M., Sun, X., Wang, H., Zhang, Y., Zhang, J.: Privacy-aware access control with trust management in Web service. World Wide Web 14(4), 407–430 (2011)
Lin, J., Sugiyama, K., Kan, M.Y., Chua, T.S.: Addressing cold-start in app recommendation: Latent user models constructed from twitter followers Proceedings of the 36th International ACM SIGIR Conference on Research and Development in Information Retrieval, pp 283–292. ACM (2013)
Liu, B., Kong, D., Cen, L., Gong, N.Z., Jin, H., Xiong, H.: Personalized mobile app recommendation: Reconciling app functionality and user privacy preference Proceedings of the 8th ACM International Conference on Web Search and Data Mining, pp 315–324. ACM (2015)
Ma, H., Yang, H., Lyu, M.R., King, I.: Sorec: Social recommendation using probabilistic matrix factorization Proceedings of the 17th ACM Conference on Information and Knowledge Management, pp 931–940. ACM (2008)
Ma, J., Sun, L., Wang, H., Zhang, Y., Aickelin, U.: Supervised anomaly detection in uncertain pseudoperiodic data streams. ACM Trans. Internet Technol. 16 (1), 1–20 (2016)
Mooney, R.J., Roy, L.: Content-based book recommending using learning for text categorization Proceedings of the 5th ACM Conference on Digital Libraries, pp 195–204. ACM (2000)
Peng, H., Gates, C., Sarma, B., Li, N., Qi, Y., Potharaju, R., Nita-Rotaru, C., Molloy, I.: Using probabilistic generative models for ranking risks of android apps Proceedings of the 2012 ACM Conference on Computer and Communications Security, pp 241–252. ACM (2012)
Peng, M., Gao, B., Zhu, J., Huang, J., Yuan, M., Li, F.: High quality information extraction and query-oriented summarization for automatic query-reply in social network. Expert Syst. Appl. 44, 92–101 (2016)
Peng, M., Huang, J.J., Ghani, N., Sun, S.T., Wu, B., He, Y.X., Wen, W.D.: Micro-blogger influence analysis based on user features. J. Internet Technol. 14 (2), 307–314 (2013)
Saad, D.: Online algorithms and stochastic approximations. Online Learning
Salakhutdinov, R., Mnih, A.: Bayesian probabilistic matrix factorization using Markov chain Monte Carlo Proceedings of the 25th International Conference on Machine Learning, pp 880–887. ACM (2008)
Salakhutdinov, R., Mnih, A.: Probabilistic matrix factorization NIPS, vol. 20, pp 1–8 (2011)
Sarwar, B., Karypis, G., Konstan, J., Riedl, J.: Item-based collaborative filtering recommendation algorithms Proceedings of the 10th International Conference on World Wide Web, pp 285–295. ACM (2001)
Shi, K., Ali, K.: Getjar mobile application recommendations with very sparse datasets Proceedings of the 18th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp 204–212. ACM (2012)
Tan, C., Liu, Q., Chen, E., Xiong, H.: Prediction for mobile application usage patterns Nokia MDC Workshop, vol. 12 (2012)
Wang, H., Cao, J., Zhang, Y.: A flexible payment scheme and its role-based access control. IEEE Trans. Knowl. Data Eng. 17(3), 425–436 (2005)
Yu, K., Zhang, B., Zhu, H., Cao, H., Tian, J.: Towards personalized context-aware recommendation by mining context logs through topic models Pacific-Asia Conference on Knowledge Discovery and Data Mining, pp 431–443. Springer (2012)
Zhang, J., Tao, X., Wang, H.: Outlier detection from large distributed databases. World Wide Web 17(4), 539–568 (2014)
Zhang, Y., Shen, Y., Wang, H., Yong, J.: On secure wireless communications for iot under eavesdropper collusion. IEEE Trans. Autom. Sci. Eng. 13(3), 1281–1293 (2016)
Zhang, Y., Shen, Y., Wang, H., Zhang, Y., Jiang, X.: On secure wireless communications for service oriented computing. IEEE Transactions on Services Computing (2015)
Zhu, H., Chen, E., Yu, K., Cao, H., Xiong, H., Tian, J.: Mining personal context-aware preferences for mobile users 2012 IEEE 12th International Conference on Data Mining, pp 1212–1217. IEEE (2012)
Zhu, H., Xiong, H., Ge, Y., Chen, E.: Mobile app recommendations with security and privacy awareness Proceedings of the 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp 951–960. ACM (2014)
Acknowledgments
This work is supported by the National Science Foundation of China (NSFC, No.61472291 and No.41472288).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article belongs to the Topical Collection: Special Issue on Security and Privacy of IoT
Guest Editors: Tarik Taleb, Zonghua Zhang, and Hua Wang
Rights and permissions
About this article
Cite this article
Peng, M., Zeng, G., Sun, Z. et al. Personalized app recommendation based on app permissions. World Wide Web 21, 89–104 (2018). https://doi.org/10.1007/s11280-017-0456-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-017-0456-y