Abstract
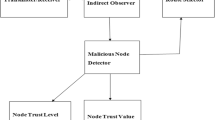
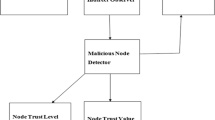
The maximum hard side of MANET is that they’re power resource-limited wherein energy cannot be replenished. Our evaluation intention is to give a high power saving management system for MANET. Cluster approaches in MANET make other nodes into small disjoint groups, wherever every cluster node encompasses an organizer known as CH (Cluster Head). The primary difficult task within the methods is retaining created clusters. To decide any node as Cluster Head, it’s very essential to summarize its constraints and eligibility which is supported by the information of the node’s properties like its remaining power or energy. There may be a possibility of the Cluster Heads might be unsuccessful and act wrongly due to power instability. During failure, the Cluster Heads are unable to collect the date and transfer information well. This influences the effectiveness of the MANET. We can decrease the information failure by detecting the failure of CH earlier, and also it needs the lowest improvement efforts. A self-configurable cluster mechanism is proposed. We planned to identify the unstable Cluster Heads and soon it will be replaced by some other nodes. k-means protocol method has been developed to select Cluster Heads effectively. This protocol (k-means) operates on an interval or periodic irregular rotations of the Cluster Heads and some of the clusters vary between 0 and 1. If the arbitrary number is smaller than the pre-decided preset (threshold) value, the node becomes a Cluster Heads for the existing round. We’ve achieved and realized a decrease in power and energy loss in comparison to other protocols like transmission and direct communication protocols. The experimental result suggests that the proposed scheme works properly in a reduction in energy dissipation compared to other protocols like transmission and direct communication protocols.















Similar content being viewed by others
Data availability
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
References
Ahmed, A., Abu Bakar, K., Channa, M. I., & Ahmed, A. (2014). A survey on trust based detection and isolation of malicious nodes in ad-hoc and sensor networks. Frontiers of Computer Science, 9, 280–296.
Apirajitha, P. S., Gopala Krishnan, C., Aravind Swaminathan, G., & Manohar, E. (2019). Enhanced secure user data on cloud using cloud data centre computing and decoy technique. International Journal of Innovative Technology and Exploring Engineering (IJITEE), 8(9), 2278–3075. https://doi.org/10.35940/ijitee.I7777.078919
Elwin, M. L., Freeman, R. A., & Lynch, K. M. (2017). Distributed Voronoi neighbor identification from inter-robot distances. IEEE Robotics and Automation Letters, 2(3), 1320–1327.
Gomathi, S., & Gopala Krishnan, C. (2020). Malicious node detection in wireless sensor networks using an efficient secure data aggregation protocol. Wireless Personal Communications. https://doi.org/10.1007/s11277-020-07291-5
Govindan, K., & Mohapatra, P. (2012). Trust computations and trust dynamics in mobile adhoc networks: a survey. IEEE Communications Surveys & Tutorials, 14(2), 279–298.
He, D., Chan, S., Tang, S., & Guizani, M. (2013). Secure data discovery and dissemination based on hash tree for wireless sensor networks. IEEE Transactions on Wireless Communications, 12(9), 4638–4646. https://doi.org/10.1109/TWC.2013.090413.130072
He, D., Chen, C., Chan, S., & Bu, J. (2012). DiCode: DoS-resistant and distributed code dissemination in wireless sensor networks. IEEE Transactions on Wireless Communications, 11(5), 1946–1956. https://doi.org/10.1109/TWC.2012.030812.111857
Janani, V. S., & Manikandan, M. S. K. (2018). Efficient trust management with Bayesian- Evidence theorem to secure public key infrastructure-based mobile ad hoc networks. Journal of Wireless Communications and Networking, 25, 1–272.
Krishnan, C. G., Julie, E. G., & Robinson, Y. H. (2020). Predictive algorithm and criteria to perform big data analytics. In V. Balas, V. Solanki, & R. Kumar (Eds.), Internet of things and big data applications. Intelligent systems reference library. (Vol. 180). Springer. https://doi.org/10.1007/978-3-030-39119-5_16
Krishnan, C., Rengarajan, A., & Manikandan, R. (2015). Delay reduction by providing location based services using hybrid cache in peer to peer networks. KSII Transactions on Internet and Information Systems, 9(6), 2078–2094. https://doi.org/10.3837/tiis.2015.06.006
Krishnan, C. G., Robinson, Y. H., & Chilamkurti, N. (2020). Machine learning techniques for speech recognition using the magnitude. Journal of Multimedia Information System, 7(1), 33–40. https://doi.org/10.33851/JMIS.2020.7.1.33
Krishnan, C. G., Sivakumar, K., & Manohar, E. (2018). An enhanced method to secure and energy effective data transfer in WSN using hierarchical and dynamic elliptic curve cryptosystem. In 2018 International Conference on Smart Systems and Inventive Technology (ICSSIT) (pp. 1-7). IEEE. DOI: https://doi.org/10.1109/ICSSIT.2018.8748785.
Nagaraju, A., Kumar, G. C., & Ramachandram, S. (2011). Ad-hoc on demand distance vector routing algorithm using neighbor matrix method in static Ad-hoc networks. In N. Meghanathan, B. K. Kaushik, & D. Nagamalai (Eds.), Advances in networks and communications. CCSIT 2011. Communications in computer and information science. (Vol. 132). Springer.
O. Pandithurai, M. Poongodi, S. P. Kumar and C. G. Krishnan. A method to support multi-tenant as a service. 2011 Third International Conference on Advanced Computing, Chennai, 2011, pp. 157–162, DOI: https://doi.org/10.1109/ICoAC.2011.6165166.
Priya, S., & Kannan, N. (2017). Refined trust energy-ad hoc on demand distance vector (ReTE-AODV) routing algorithm for secured routing in MANET. Wireless Networks, 23, 2227–2237. https://doi.org/10.1007/s11276-016-1284-1
Rashvand, H. F., Abedi, A., Alcaraz-Calero, J. M., Mitchell, P. D., & Mukhopadhyay, S. C. (2014). wireless sensor systems for space and extreme environments: a review. IEEE Sensors Journal, 14(11), 3955–3970. https://doi.org/10.1109/JSEN.2014.2357030
Shabut, A. M., Dahal, K. P., Bista, S. K., & Awan, I. U. (2015). Recommendation based trust model with an effective defence scheme for MANETs. IEEE Transactions on Mobile Computing, 14(10), 2101–2115.
Sirisala, S., & Ramakrishna, S. (2019). Survey: Enhanced trust management for improving QoS in MANETs. In R. Bapi, K. Rao, & M. Prasad (Eds.), First international conference on artificial intelligence and cognitive computing. Advances in intelligent systems and computing. (Vol. 815). Springer.
Tong, F., Pan, J., & Zhang, R. (2017). Distance distributions in finite ad hoc networks: Approaches, applications, and directions. In Ad Hoc Networks (pp. 167–179). Springer, Cham.
Velu S.G., Gopala Krishnan C., Sivakumar K., Jevin J.A. (2020) Proof of Shared Ownerships and Construct A Collaborative Cloud Application. In: Balaji S., Rocha Á., Chung YN. (eds) Intelligent Communication Technologies and Virtual Mobile Networks. ICICV 2019. Lecture Notes on Data Engineering and Communications Technologies, vol 33. Springer, Cham.
Wei, Z., Tang, H., Yu, F. R., Wang, M., & Mason, P. (2014). Security enhancements for mobile ad hoc networks with trust management using uncertain reasoning. IEEE Transactions on Vehicular Technology, 63(9), 4647–4658.
Zhang, D., Gao, J., & Liu, X. (2019). Novel approach of distributed & adaptive trust metrics for MANET. Wireless Networks, 25, 3587–3603.
Funding
The author received no financial support for the research publication of this article.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The author have no conflict of interest and agree with the contents of the manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gopala Krishnan, C., Gomathi, S., Aravind Swaminathan, G. et al. Trust Management Framework and High Energy Efficient Lifetime Management System for MANET using Self-Configurable Cluster Mechanism. Wireless Pers Commun 128, 2397–2417 (2023). https://doi.org/10.1007/s11277-022-10048-x
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-10048-x