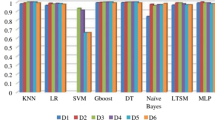
Abstract
Performance of wireless sensor network are highly prone to network anomalies particularly to misdirection attacks and blackhole attacks. Therefor intrusion detection system has a key role in WSN and it’s essential in security application. However the identification of active attacks is cumbersome in many cases particularly for remote sensing applications. This paper proposes hybrid anomaly detection method for misdirection and blackhole attacks by employing K-medoid customized clustering technique. A synthetic dataset was established by defining network parameters and threshold values were obtained to detect the anomalies. Experimental work was performed on network simulator (NS-2) and R studio. The proposed algorithm successfully detect the hybrid anomalies with high accuracy. This work is suitable for hybrid anomaly detection including misdirection and blackhole attacks in wireless environment.




Similar content being viewed by others
References
Nishani, L., & Biba, M. (2016). Machine learning for intrusion detection in MANET: A state-of-the-art survey. Journal of Intelligent Information Systems, 46(2), 391–407.
Pachauria, G., & Sharma, S. (2015). Anomaly detection in medical wireless sensor networks using machine learning algorithms. Procedia Computer Science, 70, 325–333.
Alsheikh, M. A., Lin, S., Niyato, D., & Tan, H.-P. (2015). Machine learning in wireless sensor networks: Algorithms, strategies, and applications. Procedia Computer Science, 70, 325–333.
Kavitha, P., & Usha, M. (2014). Cluster based anomaly detection in wireless LAN. International Journal of Computer Trends and Technology (IJCTT), 12(5), 227–230.
Kalaiselvan, K., & Singh, G. (2015). Detection and isolation of black hole attack in wireless sensor networks. International Journal of Innovative Research in Science, Engineering and Technology, 4(5), 3516–3524.
Kaur, R., Sharma, D., & Kaur, N. (2013). Comparative analysis of leach and its descendant protocols in wireless sensor network. International Journal of P2P Network Trends and Technology, 3(1), 51–55.
Almomani, I., Al-Kasasbeh, B., & AL-Akhras, M. (2016). WSN-DS: A dataset for intrusion detection systems in wireless sensor networks. Journal of Sensors, 2016, Article ID 4731953.
Shi, Qiong, Qin, Li, Song, Lipeng, Zhang, Rongping, & Jia, Yanfeng. (2017). A dynamic programming model for internal attack detection in wireless sensor networks. Discrete Dynamics in Nature and Society, 2017, 1–9.
Hou, X., Lei, C.-U., & Kwok, Y.-K. (2017). OP-DCI: A riskless K-means clustering for influential user identification in MOOC forum. In 16th IEEE international conference on machine learning and applications (ICMLA) (pp. 936–939).
Alipour, H., Al-Nashif, Y. B., Satam, P., & Hariri, S. (2015). Wireless anomaly detection based on IEEE 802.11 behavior analysis. IEEE Transactions on Information Forensics and Security, 10(10), 2158–2170.
Garcia-Font, V., Garrigues, C., & Rifà-Pous, H. (2016). A comparative study of anomaly detection techniques for smart city wireless sensor networks. In Lu, R. (Ed.) Sensors, Vol. 16, no. 6, Basel, Switzerland.
Shah, Z., & Patel, R. (2016). Misdirection attack in wireless sensor network: A survey. International Journal for Technological Research in Engineering, 3(9), 2044–2047.
Gao, H., Wu, R., Cao, M., & Zhang, C. (2014). Detection and defense technology of blackhole attacks in wireless sensor network. In X. Sun et al. (Eds.), Algorithms and architectures for parallel processing (pp. 601–610). Cham: Springer.
Syarif, I., Prugel-Bennett, A., & Wills, G. (2012). Unsupervised clustering approach for network anomaly. In R. Benlamri (Ed.), Networked digital technologies. Communications in computer and information science (Vol. 293, pp. 135–145). Berlin: Springer.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ahmad, B., Jian, W., Ali, Z.A. et al. Hybrid Anomaly Detection by Using Clustering for Wireless Sensor Network. Wireless Pers Commun 106, 1841–1853 (2019). https://doi.org/10.1007/s11277-018-5721-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5721-6