Abstract
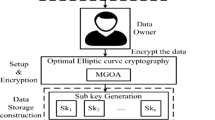
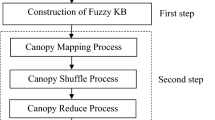
The main intention of this paper is develop a technique for privacy preserving-aware over big data in clouds using variation step size firefly algorithm and MapReduce framework. This paper consists of two phases such as MapReduce phase and evaluation phase. In MapReduce phase, at first we split the big data into a number of maps. After that, we apply the convolution process to the dataset and create a new kernel matrix. Once the convolution process is over, the privacy-persevering framework over big data in cloud systems is performed based on the evaluation phase. In evaluation module, the neural network is trained based on the optimal weight and radial basis function neural network algorithm, which is improving the utility of the privacy data. After that, a MapReduce framework is to protect the private information. Finally, the reduced privacy data are stored in the computer service provider. In this big data experiment, we used census income KDD dataset to evaluate the result.















Similar content being viewed by others
References
Sen, J. (2013). Security and privacy issues in cloud computing. In Architectures and protocols for secure information technology infrastructures (pp. 1–42). IGI Global book series, Chapter publication, ISSN: 978-1-4666-4514-1.
Satpute, K., Satpute, C., & Bhade, D. (2014). Review on internet base services of cloud computing. International Journal on Recent and Innovation Trends in Computing and Communication, 2(2), 263–266.
Carolan, J., & Gaede, S. (2009). Introduction to cloud computing architecture (pp. 1–40). SUN Microsystems Inc.
Dule, C. S., Girijamma, H. A., & Rajasekharaiah, K. M. (2014). Privacy preservation enriched MapReduce for Hadoop based big data applications. International Journal of Research in Science, Technology, Engineering & Mathematics, 6(3), 293–299.
Takabi, H., Joshi, J. B. D., & Ahn, G. (2010). Security and privacy challenges in cloud computing environments. IEEE Security and Privacy, 8(6), 24–31.
Zissis, D., & Lekkas, D. (2011). Addressing cloud computing security issues. Future Generation Computer Systems, 28(3), 583–592.
Agrawal, D., El Abbadi, A., & Wang, S. (2012). Secure and privacy-preserving data services in the cloud: A data centric view. Proceedings of the VLDB Endowment, 5(12), 2019–2028.
Hemalatha, S., & AlaudeenBasha, S. (2013). Enabling for cost-effective privacy preserving of intermediate data sets in cloud. International Journal of Scientific and Research Publications, 3(10), 1–5.
Dean, J., & Ghemawat, S. (2004). MapReduce: Simplified data processing on large clusters. In Proceedings of OSDI (pp. 137–150).
Dean, J., & Ghemawat, S. (2010). MapReduce: A flexible data processing tool. ACM Journal of Communication, 53(1), 72–77.
Apache hadoop. (2013). http://hadoop.apache.org/.
Chaudhuri, S. (2012). What next? A half-dozen data management research goals for big data and the cloud. In Proceedings of the 31st symposium on principles of dataset systems (pp. 1–4).
Cao, N., Wang, C., Li, M., Ren, K., & Lou, W. (2011). Privacy-preserving multi-keyword ranked search over encrypted cloud data. In Proceedings of the 31st annual IEEE international conference on computer communications (pp. 829–837).
Puttaswamy, K. P. N., Kruegel, C., & Zhao, B. Y. (2011). Toward data confidentiality in storage-intensive cloud applications. In Proceedings of the 2nd ACM symposium on cloud computing (pp. 1–9).
Roy, I., Setty, S. T. V., Kilzer, A., Shmatikov, V., & Witchel, E. (2010). Security and privacy for MapReduce. In Proceedings of 7th USENIX conference on networked systems design and implementation (pp. 297–312).
Xiao, Z., & Xiao, Y. (2011). Accountable MapReduce in cloud computing. In Proceedings of the 2011 IEEE conference on computer communications workshops (pp. 1082–1087).
Fung, B. C. M., Wang, K., Chen, R., & Yu, P. S. (2010). Privacy-preserving data publishing: A survey of recent developments. Journal of ACM Computer Survey, 42(4), 1–53.
Apache. (2013). Apache Mahout machine learning library. Accessed March 10, 2013, from http://mahout.apache.org/.
Rahulamathavan, Y., Phan, R. C.-W., Veluru, S., Cumanan, K., & Rajarajan, M. (2014). Privacy-preserving multi-class support vector machine for outsourcing the data classification in cloud. IEEE Transactions on Dependable and Secure Computing, 11(5), 467–479.
Zhang, X., Liu, C., Nepal, S., Pandey, S., & Chen, J. (2013). A privacy leakage upper bound constraint-based approach for cost-effective privacy preserving of intermediate data sets in cloud. IEEE Transactions on Parallel and Distributed Systems, 24(6), 1192–1203.
Li, X. (2014). An algorithm for mining frequent itemsets from library big data. Journal of Software, 9(9), 2361–2365.
Dhasarathan, C., Dananjayan, S., Dayalan, R., & Ponnurangam, V. T. D. (2015). A multi-agent approach: To preserve user information privacy for a pervasive and ubiquitous environment. Egyptian Informatics Journal, 16(1), 151–166.
Dong, X., Jiadi, Y., Luo, Y., Chen, Y., Xue, G., & Li, M. (2014). Achieving an effective, scalable and privacy-preserving data sharing service in cloud computing. Journal of Computers and Security, 42, 151–164.
Zhang, X., Liu, C., Nepal, S., Dou, W., & Chen, J. (2012). Privacy-preserving layer over MapReduce on cloud. In Proceeding CGC ‘12 Proceedings of the 2012 second international conference on cloud and green computing (pp. 304–310).
Yang, X. S. (2009). Firefly algorithms for multimodal optimization. In O. Watanabe and T. Zeugmann (Eds.), Proceedings 5th symposium on stochastic algorithms, foundations and applications. Lecture notes in computer science (pp. 169–178).
Dean, J., & Ghemawat, S. (2010). MapReduce: A flexible data processing tool. Communications of the ACM, 53(1), 72–77.
Qasem, S. N., & Shamsuddin, S. M. (2011). Radial basis function network based on time variant multi-objective particle swarm optimization for medical diseases diagnosis. Applied Soft Computing Journal, 11(1), 1427–1438.
Wang, L., Zhan, J., Shi, W., & Liang, Y. (2012). In cloud, can scientific communities benefit from the economies of scale? IEEE Transactions on Parallel and Distributed Systems, 23(2), 296–303.
UCI Machine Learning Repository. (2013). Census-income (KDD) data set. Accessed Nov 30, 2013, from http://archive.ics.uci.edu/ml/datasets/Census-Income+ (KDD).
Fung, B. C. M., Wang, K., & Yu, P. S. (2007). Anonymizing classification data for privacy preservation. IEEE Transactions on Knowledge and Data Engineering, 19(5), 711–725.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Thiyagarajan, V.S., Ayyasamy, A. Privacy Preserving Over Big Data Through VSSFA and MapReduce Framework in Cloud Environment. Wireless Pers Commun 97, 6239–6263 (2017). https://doi.org/10.1007/s11277-017-4836-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4836-5