Abstract
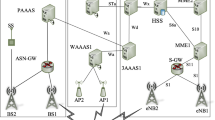
The incorporation of Wireless Local Area Networks (WLANs) within the third generation (3G) networks materializes the next generation of mobile/wireless systems, named 3G-WLANs integrated networks. This paper proposes an improved authentication procedure for the 3G-WLANs integrated networks that enables a WLAN user to get access to the 3G packet switched services or to the public Internet through the 3G public land mobile network. The proposed procedure reduces significantly the authentication overhead compared to the legacy one, without compromising the provided security services. A security analysis of the proposed authentication procedure is elaborated that ensures the correctness of the authentication procedure, the provision of advanced security services and the elimination of possible attacks that may threaten the proposed authentication procedure. In addition, an energy cost analysis is carried out that compares the energy consumption induced by the legacy and the proposed authentication procedures. Finally, a communication cost analysis is provided that estimates the cost improvement of the proposed over the legacy authentication procedure.
Similar content being viewed by others
References
3GPP TS 23.234 (v7.3.0). (2006). 3GPP system to WLAN interworking; system description. Release 7, Sep. 2006.
3GPP TS 33.234 (v7.2.0). (2006). 3G security; WLAN interworking security; system description. Release 7, Sep. 2006.
Arkko, J., & Haverinen, H. (2006). EAP-AKA authentication. RFC 4187, Jan. 2006.
Kaufman, C. (2005). The internet key exchange (IKEv2) protocol. RFC 4306, Dec. 2005.
Xenakis C. and Ntantogian C. (2007). Security architectures for B3G mobile networks. Telecommunication Systems 35: 123–139. doi:10.1007/s11235-007-9044-2.
Liang W. and Wang W. (2005). On performance analysis of challenge/response based authentication in wireless networks. Computer Networks 48(2): 267–288
Zhang Y. and Fujise M. (2006). An improvement for authentication protocol in third generation wireless networks. IEEE Transactions on Wireless Communications 5(9): 2348–2352. doi:10.1109/TWC.2006.1687756.
Lin Y.B. and Chen Y.K. (2003). Reducing authentication signalling traffic in third-generation mobile network. IEEE Transactions on Wireless Communications 2(3): 493–501. doi:10.1109/TWC.2003.811171.
Saraireh, J. A., & Yousef, S. (2006). A new authentication protocol for UMTS mobile networks. EURASIP Journal on Wireless Communications and Networking.
Chang C.C., Lee J.S. and Chang Y.F. (2005). Efficient authentication protocols of GSM. Computer Communication 28(8): 921–928
Yang C.C., Yang Y.W. and Liu W.T. (2006). A robust authentication protocol with non-repudiation service for integrating WLAN and 3G network. Wireless Personal Communications 39(2): 229–251. doi:10.1007/s11277-006-9090-1.
Salgarelli L., Buddhikot M., Garay J., Patel S. and Miller S. (2003). Efficient authentication and key distribution in wireless IP networks. IEEE Wireless Communications 10(6): 52–61. doi:10.1109/MWC.2003.1265853.
Prasithsangaree, P., & Krishnamurthy, P. (2004). A new authentication mechanism for loosely coupled 3G-WLAN integrated networks. In IEEE 59th Vehicular Technology Conference, (VTC) (Vol. 5, pp. 2998–3003), May 2004.
Liang, W., & Wang, W. (2004). A local authentication control scheme based on AAA architecture in wireless networks. In IEEE 60th Vehicular Technology Conference (VTC) (Vol. 7, pp. 5276–5280), Sep. 2004.
Lin Y.B., Chang M.F., Hsu M.T. and Wu L.Y. (2005). One-pass GPRS and IMS authentication procedure for UMTS. IEEE Journal on Selected Areas in Communications 23(6): 1233–1239. doi:10.1109/JSAC.2005.845631.
Std, I.E.E.E. 802.11. (1999). Wireless LAN medium access control (MAC) and physical layer (PHY) specifications.
Calhoun, P., Loughney, J., Guttman, E., Zorn, G., & Arkko, J. (2003). Diameter base protocol. RFC 3588, Sep. 2003.
Std, I.E.E.E. 802.11i. (2004). Wireless medium access control (MAC) and physical layer (PHY) specifications: Medium access control (MAC) security enhancements.
Kent, S., & Atkinson, R. (1998). Security architecture for internet protocol. RFC 2401, Nov. 1998.
Kent, S., & Atkinson, R. (1998). IP encapsulating security payload (ESP). RFC 2406, Nov. 1998.
Xenakis C. and Merakos L. (2004). Security in third generation mobile networks. Computer Communications 27(7): 638–650
IEEE Std 802.11X. (2004). Port based network access control.
ETSI TS 33.902. (2002). Formal analysis of 3G authentication protocol.
Potlapally, N. R., Ravi, S., Raghunathan, A., & Jha, N. K. (2003). Analyzing the energy consumption of security protocols. In International Symposium on Low Power Electronics and Design (ISLPED), Seoul, Korea, Aug. 2003.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ntantogian, C., Xenakis, C. One-Pass EAP-AKA Authentication in 3G-WLAN Integrated Networks. Wireless Pers Commun 48, 569–584 (2009). https://doi.org/10.1007/s11277-008-9548-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-008-9548-4