Abstract
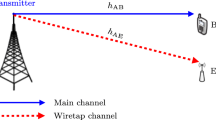
We consider a secure wireless multicasting scenario over Generalized \(\kappa -\mu\) fading channels via multiple amplify-and-forward cooperative relays. In the first hop, a source S transmits a common stream of information to a group of K relays. In the second hop, the best relay which has the highest signal-to-noise ratio, forwards the amplified version of information to a group of M destination users in the presence of multiple eavesdroppers. We assume that there is no direct link between source and destination users as well as eavesdroppers. Destinations and eavesdroppers are communicating with the source via relays only. The key contribution of this paper is to enhance the security of wireless multicasting using the additional diversity provided by the best relay of K relays. In order to investigate the performance of the proposed model, we derive the analytical expressions for the probability of non-zero secrecy multicast capacity and the secure outage probability in terms of the number of relays, destination users and eavesdroppers. Finally, the analytical expressions are verified via Monte Carlo simulation.





Similar content being viewed by others
References
Khalil, M. I., Berber, S. M., & Sowerby, K. W. (2017). Bit error rate performance analysis in amplify-and-forward relay networks. Wireless Networks, 23, 947–957.
Amin, O., Mesleh, R., Ikki, S. S., Ahmed, M. H., & Dobre, O. A. (2014). Performance analysis of multiple relays cooperative systems with signal space diversity. IEEE Transactions on Vehicular Technology, 64(8), 3414–3425.
Chu, S., Wang, X., & Yang, Y. (2012). Exploiting cooperative relay for high performance communications in MIMO ad hoc networks. IEEE Transactions on Computers, 62(4), 716–729.
Moharrer, H., Olfat, A., & Beaulieu, N. C. (2015). Cooperative beamforming for two-hop multi-relay decode-and-forward networks. IEEE Transactions on Communications, 63(9), 3143–3156.
Vashistha, A., Sharma, S., & Bohara, V. A. (2015). Outage analysis of a multiple antenna cognitive radio system with cooperative decode-and-forward relaying. IEEE Communications Letters, 4(2), 125–128.
Majhi, S., & Banarjee, A. (2015). Asymptotic outage analysis of incremental decode and forward cognitive radio relay network. In Proceedings of IEEE 7th international conference on communication systems and networks (COMSNETS 2015).
Duong, T. Q., Bao, V. N. Q., & Zepernick, H.-J. (2009). On the performance of selection decode-and-forward relay networks over Nakagami-m fading channels. IEEE Communications Letters, 13(3), 172–174.
Darsena, D., Gelli, G., Melito, F., & Verde, F. (2014). Performance analysis of amplify-and-forward multiple-relay MIMO systems with ZF reception. IEEE Transactions on Vehicular Technology, 64(7), 3274–3280.
Han, J.-S., Baek, J.-S., Jeon, S., & Seo, J.-S. (2014). Cooperative networks with amplify-and-forward multiple-full-duplex relays. IEEE Transactions on Wireless Communications, 13(4), 2137–2149.
Som, P., & Chokalingam, A. (2014).Decode-and-forward cooperative multicast with space shift keying. In Proceedings of IEEE wireless communication and networking conference (WCNC2014).
Lim, S. H., Kim, K. T., & Kim, Y.-H. (2014). Distributed decode-forward for multicast. In Proceedings of IEEE international symposium on information theory (ISIT 2014) (pp. 636–640).
Chattha, J., & Uppal, M. (2016). Layered multiplexed-coded relaying in wireless multicast using QAM transmissions. IEEE Communications Letters, 20(4), 760–763.
Lei, H., Dai, Z., Park, K.-H., Lei, W., Pan,G., & Alouini, M.-S. (2018). Secrecy outage analysis of mixed RF-FSO downlink SWIPT systems. IEEE Transactions on Communications. https://doi.org/10.1109/TCOMM.2018.2865944
Bassily, R., & Ulukas, S. (2012). Secure communication in multiple relay networks through decode-and-forward strategies. Journal of Communications and Networks, 14(4), 352–363.
Zhu, J., Zou, Y., Champagne, B., Zhu, W.-P., & Hanzo, L. (2016). Security-reliability tradeoff analysis of multirelay-aided decode-and-forward cooperation systems. IEEE Transactions on Vehicular Technology, 65(7), 5825–5831.
Wang, D., Bai, B., Chen, W., & Han, Z. (2015). Energy efficient secure communication over decode-and-forward relay channels. IEEE Transactions on Communications, 63(3), 892–905.
Liu, Y., Wang, L., Duy, T., Elkashlan, M., & Duong, T. Q. (2015). Relay selection for security enhancement in cognitive relay networks. IEEE Wireless Communications Letters, 4(1), 46–49.
Sun, L., Ren, P., Du, Q., Wang, Y., & Gao, Z. (2015). Security-aware relaying scheme for cooperative networks with untrusted relay nodes. IEEE Communications Letters, 19(3), 463–466.
Zhang, J., & Pan, G. (2017). Secrecy outage analysis with Kth best relay selection in dual-hop inter-vehicle communication systems. International Journal of Electronics and Communications (AEU), 71, 139–144.
Wang, X., Tao, M., & Xu, Y. (2014). Outage analysis of cooperative secrecy multicast transmission. IEEE Wireless Communications Letters, 3(2), 161–164.
Zou, Y., Zhu, J., Li, X., & Hanzo, L. (2016). Relay selection for wireless communications against eavesdropping: A security-reliability tradeoff perspective. IEEE Networks, 30(5), 74–79.
Lei, H., Zhang, H., Ansari, I. S., Ren, Z., Pan, G., Qaraqe, K. A., et al. (2017). On secrecy outage of relay selection in underlay cognitive radio networks over Nakagami-m fading channels. IEEE Transactions on Cognitive Communications and Networking, 3(4), 614–627.
Sarker, D. K., Sarkar, M. Z. I., & Anower, M. S. (2017). Secure wireless multicasting with linear equalization. Physical Communication, 25(1), 201–213.
Wayner, A. D. (1975). The wire-tap channel. Bell Systems Technical Journal, 54(8), 1355–1387.
Bloch, M., Barros, J., Rodrigues, M., & McLaughlin, S. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54(6), 2515–2534.
Mavoungou, S., Kaddoum, G., Taha, M., & Matar, G. (2016). Survey on threats and attacks on mobile networks. IEEE Access, 4, 4543–4572.
Shannon, C. E. (1949). Communication theory of secrecy systems. Bell System Technical Journal, 28, 656–715.
Fragkiadakis, A., Tragos, E., & Askoxylakis, I. (2013). A survey on security threats and detection techniques in cognitive radio networks. IEEE Communications Surveys and Tutorials, 15(1), 428–445.
Yacoub, M. D. (2001). The \(\kappa -\mu\) distribution: A general fading distribution. In Proceedings of IEEE 54th Vehicular Technology Conference (VTC 2001) (pp. 1427–1431).
Krikidis, I., Thompson, J. S., McLaughlin, S., & Goertz, N. (2009). Max-min relay selection for legacy amplify-and-forward systems with interference. IEEE Transactions on Wireless Communications, 8(6), 3016–3027.
Ambramowitz, M., & Stegum, A. (1970). Handbook of mathematical functions with formulas, Graphs and mathematical tables (9th ed.). New York: Dover Press.
Nagendra, K., & Vimal, B. (2015). Performance analysis of amplify-and-forward cooperative networks with best-relay selection over Weibull fading channels. Wireless Personal Communications, 85, 641–653.
Gradshteyn, I. S., & Ryzhik, I. M. (2007). Table of integrals, series, and products (7th ed.). San Diego: Academic Press.
Fedele, G. (1996). N-branch diversity reception of M-ary DPSK signals in slow and nonselective Nakagami fading. European Transactions on Telecommunication, 7, 119–123.
Khisti, A., & Zhang, D. (2013). Artificial-noise alignment for secure multicast using multiple antennas. IEEE Communications Letters, 17(8), 1568–1571.
Sarkar, M. Z. I. & Ratnarajah, T. (2011). Secure wireless multicasting through Nakagami-m fading MISO channel. In Proceedings of IEEE 45th Asilomar conference on signals, systems and computers (ASILOMAR 2011) (pp. 300–304).
Sarkar, M. Z. I., & Ratnarajah, T. (2012). Enhancing security in correlated channel with maximal ratio combining diversity. IEEE Transactions on Signal Processing, 60(12), 6745–6751.
Sarkar, M. Z. I. & Ratnarajah, T. (2010). Information-theoretic security in wireless multicasting. In Proceedings of IEEE 6th international conference on electrical and computer engineering (ICECE 2010) (pp. 53–56).
Wang, P., Yu, G., & Zhang, Z. (2007). On the secrecy capacity of fading wireless channel with multiple eavesdroppers. In Proceedings of IEEE international symposium on information theory (ISIT 2007) (pp. 1301–1305).
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1
This appendix evaluates the integral, \(I_{1}\) as shown below:
Performing integration using Eq. (36) and the following identity
we obtain
where
Appendix 2
In this appendix, we provide evaluation of the integrals, \(I_{2}\) to \(I_{7}\) as follows:
Using Eqs. (16) and (17), we have
Substituting the value of L, we obtain
where
Similar to Eq. (59), we obtain
where
Rights and permissions
About this article
Cite this article
Sarker, D.K., Sarkar, M.Z.I. & Anower, M.S. Secure wireless multicasting through AF-cooperative networks with best-relay selection over generalized fading channels. Wireless Netw 26, 1717–1730 (2020). https://doi.org/10.1007/s11276-018-1861-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-018-1861-6