Abstract
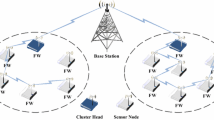
Nodes in a wireless sensor network (WSN) are generally deployed in unattended environments making them susceptible to attacks. Therefore, the need of defending such attacks is of utmost importance. The challenge in providing security in this network is that the securing mechanism must be lightweight to make it implementable for such resource-constrained nodes. A robust security solution for such networks must facilitate authentication of sensor nodes. So far, only data authentication has drawn much attention from the research community. In this paper, a digital watermark based low-overhead solution (LoWaNA) is proposed for node authentication. The proposed watermarking technique consists of three modules viz. watermark generation, embedding and detection. The robustness of the algorithm is measured in terms of cracking probability and cracking time. This robustness analysis helps us to set the design guideline regarding size of watermark. Performance of the scheme is analyzed in terms of storage, computation and communication overhead. The analytical results are compared with two of the existing schemes and that show significant reduction of all such overheads. Thus it proves the suitability of the proposed scheme for resource-constrained networks like WSN. Finally the entire scheme is simulated in Cooja, the Contiki network simulator to make it readily implementable in real life mote e.g. MICAz.






Similar content being viewed by others
References
Newman, R., & Beyah, R. A. (2009). On the performance of using Covert Timing Channels for node authentication. Security and Communication Networks, 2(6), 492–506.
Zhang, W., Liu, Y., Das, S., & De, P. (2008). Secure data aggregation in wireless sensor networks: A watermark based authentication supportive approach. Pervasive and Mobile Computing, 4, 658–680.
Akyildiz, I. F., Su, W., Sankarasubramaniam, Y., & Cayirci, E. (2002). Wireless sensor network: A survey. Computer Networks, 38, 393–422.
Xiao, R., Sun, X., & Yang, Y. (2008). Copyright protection in wireless sensor networks by watermarking. In: International conference on intelligent information hiding and multimedia signal processing (IIH-MSP), pp. 7–10.
Dong, X., & Li, X. (2009). An authentication method for self nodes based on watermarking in wireless sensor networks. In: International conference on wireless communication (WiCOM), pp. 4529–4532.
Gupta, S., Verma, H. K., & Sangal, A. L. (2010). Authentication protocol for wireless sensor networks. International Journal of World Academy of Science, Engineering and Technology (WASET), Paris, 42, 630–636.
Zhang, J., Shankaran, R., Orgun, M. A., Sattar, A., & Varadharajan, V. (2012). A Dynamic authentication scheme for hierarchical wireless sensor networks. Mobile and Ubiquitous Systems: Computing, Networking, and Services, Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, Vol. 73, pp. 186–197.
Zhang, Q., Zhou, X., & Yang, F. (2009). Distributed node authentication in wireless sensor networks. In: 5th International conference on wireless communications, networking and mobile computing (WiCOM), pp. 3361–3364.
Kugler, P., Nordhus, P., & Eskofier, B. (2013). Shimmer, Cooja and Contiki: A new toolset for the simulation of on-node signal processing algorithms. In: International conference on body sensor networks, pp. 1–6.
Menezes, A., van Oorschot, P., & Vanstone, S. (1996). Handbook of Applied Cryptography, CRC Press.
Pathan, A. S. K., Lee, H.-W., & Hong, C. S.(2006). Security in wireless sensor networks: Issues and challenges. In: International conference on advanced computing technologies, pp. 1043–1045.
Karlof, C., & Wagner, D. (2003). Secure routing in wireless sensor networks: Attacks and counter measures. Elsevier’s AdHoc Networks Journal, 1(2–3), 293–315 (special issue on Sensor Network Applications and Protocols).
MD5 algorithm. http://en.wikipedia.org/wiki/MD5.
MICAz Datasheet. http://www.openautomation.net/uploadsproductos/micazdatasheet.pdf.
MD5 Analysis. http://daoyuan.li/category/projects/9-md5/.
de Meulenaer, G., Gosset, F., Standaert, F.-X., & Pereira, O.(2008). On the energy cost of communication and cryptography in wireless sensor networks. In: Networking and communications. International conference on wireless and mobile computing (wimob), pp. 580–585.
Chowdhury, A. R., Chatterjee, T., & DasBit, S. (2014). LOCHA: A light-weight one-way cryptographic hash algorithm for wireless sensor network. In: 5th International conference on ambient systems, networks and technologies (ANT), procedia computer science, Vol. 32, pp. 497–504.
Yussoff, Y. M., Hashim, H., & Baba, M. D. (2012). Identity-based trusted authentication in wireless sensor network. International Journal of Computer Science Issues (IJCSI), 9(3), 230–239.
Contiki COOJA Crash Course ppt. www.sics.se/~thiemo/seniot09cccc-slides.pdf.
Dunkels, A., Osterlind, F., & He, Z. (2007). An adaptive communication architecture for wireless sensor networks. In: International conference on embedded networked sensor systems (SenSys), ACM digital library, pp. 335–349.
Kuhn, F., Wattenhofer, R., & Zollinger, A. (2003). Ad hoc networks beyond unit disk graphs. In Proceedings of the 2003 joint workshop on foundations of mobile computing (DIALM-POMC ’03), pp. 69–78.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sen, A., Chatterjee, T. & DasBit, S. LoWaNA: low overhead watermark based node authentication in WSN. Wireless Netw 22, 2453–2467 (2016). https://doi.org/10.1007/s11276-015-1157-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-015-1157-z