Abstract
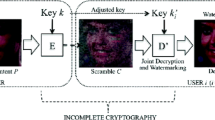
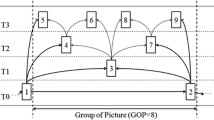
Intellectual Property (IP) protection is a critical element in multimedia transmission and delivery systems. Conventional IP protection on multimedia data can be categorized into encryption and watermarking. In this paper, a structure to perform layered access control on scalable media by combining encryption and robust watermarking is proposed, implemented, and verified. By taking advantages of the nature of both encryption and watermarking, copyrights of multimedia contents can be well protected and at the same time, multiple-grade services can be provided. In the summated examples, we assume a scalable transmission scheme over the broadcasting environment and use it to test the effectiveness of proposed method. When the embedded watermark is extracted with high confidence, the key to decrypt the next layer can be perfectly recovered. Then, the media contents are reconstructed and the copyrights are assured. The application examples also demonstrate the practicality of the proposed system.
Similar content being viewed by others
References
X. Sun et al., “Seamless switching of scalable video bitstreams for efficient streaming,” IEEE Trans. Multimedia, vol. 6, no. 4, 2004, pp. 291–303.
J.M. Almeida et al., “Minimizing delivery cost in scalable streaming content distribution systems,” IEEE Trans. Multimedia, vol. 6, no. 2, 2004, pp. 356–365, Apr.
T. Wiegand et al., “Overview of the H.264/AVC video coding standard,” IEEE Trans. Circuits Syst. Video Technol., vol. 13, no. 7, 2003, pp. 560–576, Jul.
R. Parviainen and P. Parnes, “Large scale distributed watermarking of multicast media through encryption,” Proc. IFIP TC6/TC11, 2001, pp. 149–158.
W. Trappe et al., “Key management and distribution for secure multimedia multicast,” IEEE Trans. Multimedia, vol. 5, no. 4, 2003, pp. 544–557, Dec.
X. Xu, S. Dexter and A.M. Eskicioglu, “A hybrid scheme for encryption and watermarking,” IS&T/SPIE Symp. Electron. Imaging 2004, 2004, pp. 723–734.
J.S. Pan, H.-C. Huang and L.C. Jain (Eds.), Intelligent Watermarking Techniques, World Scientific, 2004.
H.-C. Huang, F.H. Wang and J.S. Pan, “A VQ-based robust multi-watermarking algorithm,” IEICE Trans. Fundam. Electron., Commun. Comput. Sci., vol. E-85A, no. 7, 2002, pp. 1719–1726, Jul.
S.J. Wee and J.G. Apostolopoulos, “Secure scalable streaming enabling transcoding without decryption,” IEEE Int. Conf. Image Proc., 2001, pp. 437–440.
Data encryption standard (DES), http://www.itl.nist.gov/fipspubs/fip46-2.htm, 1993.
Advanced encryption standard (AES), http://csrc.nist.gov/CryptoToolkit/aes/, 2001.
G. O’Driscoll, The Essential Guide to Digital Set—top Boxes and Interactive TV, Prentice Hall, 2000.
Real time streaming protocol, http://www.rtsp.org/, 2004.
H. Schulzrinne, http://www.cs.columbia.edu/~hgs/rtp/, 2004.
F.-C. Chang, H.-C. Huang and H.-M. Hang, “Combined encryption and watermarking approaches for scalable multimedia coding,” 2004 Pacific-Rim Conf. on Multimedia (PCM2004), 2004, pp. 356–363, Dec.
C.S. Shieh et al., “Genetic watermarking based on transform domain techniques,” Pattern Recogn., vol. 37, no. 3, 2004, pp. 555–565, Mar.
V. Chande and N. Farvardin, “Progressive transmission of images over memoryless noisy channels,” IEEE J. Sel. Areas Commun., vol. 18, 2000, pp. 850–860.
J.S. Pan et al., “Robust VQ-based digital watermarking for the memoryless binary symmetric channel,” IEICE Trans. Fundam. Electron. Commun. Comput. Sci., vol. E-87A, no. 7, 2004, pp. 1839–1841, Jul.
J.S. Pan et al., “Robust image watermarking based on multiple description vector quantisation,” IEE Electron. Lett., vol. 40, no. 22, 2004, pp. 1409–1410, Oct.
F.-C. Chang, H.-C. Huang and H.-M. Hang, “Layered access control schemes on watermarked scalable media,” 2005 IEEE Int. Symp. Circuits Syst. (ISCAS2005), 2005, pp. 4983–4986, May.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chang, FC., Huang, HC. & Hang, HM. Layered Access Control Schemes on Watermarked Scalable Media. J VLSI Sign Process Syst Sign Im 49, 443–455 (2007). https://doi.org/10.1007/s11265-007-0095-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11265-007-0095-0