Abstract
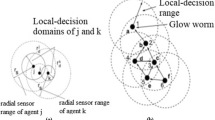
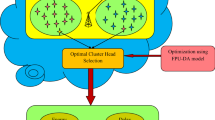
Wireless sensor networks (WSNs) contain numerous nodes that their main goals are to monitor and control environments. Also, sensor nodes distribute based on network usage. One of the most significant issues in this type of network is the energy consumption of sensor nodes. In fixed-sink networks, nodes which are near the sink act as an interface to transfer data of other nodes to sink. This causes the energy consumption of sensors reduces rapidly. Therefore, the lifetime of the network declines. Sensor nodes owing to their weaknesses are susceptible to several threats, one of which is denial-of-sleep attack (DoSA) threatening WSN. Hence, the DoSA refers to the energy loss in these nodes by maintaining the nodes from entering energy-saving and sleep mode. In this paper, a hybrid approach is proposed based on mobile sink, firefly algorithm based on leach, and Hopfield neural network (WSN-FAHN). Thus, mobile sink is applied to both improve energy consumption and increase network lifetime. Firefly algorithm is proposed to cluster nodes and authenticate in two levels to prevent from DoSA. In addition, Hopfield neural network detects the direction route of the sink movement to send data of CH. Furthermore, here WSN-FAHN technique is assessed through wide simulations performed in the NS-2 environment. The WSN-FAHN procedure superiority is demonstrated by simulation outcomes in comparison with contemporary schemes based on performance metrics like packet delivery ratio (PDR), average throughput, detection ratio, and network lifetime while decreasing the average residual energy.










Similar content being viewed by others
References
Juneja V, Gupta DV (2018) Security against vampire attack in ADHOC wireless sensor network: detection and prevention techniques. In: International Conference on Wireless Intelligent and Distributed Environment for Communication. Springer, Cham, pp 25–38
Osanaiye OA, Alfa AS, Hancke GP (2018) Denial of service defence for resource availability in wireless sensor networks. IEEE Access 6:6975–7004
Fotohi R, Jamali S (2014) A comprehensive study on defence against wormhole attack methods in mobile Ad hoc networks. Int J Comput Sci Netw Solut 2:37–56
Zandiyan S, Fotohi R, Koravand M (2016) P-method: improving AODV routing protocol for against network layer attacks in mobile Ad-Hoc networks. Int J Comput Sci Inf Secur 14(6):95
Behzad S, Fotohi R, Jamali S (2013) Improvement over the OLSR routing protocol in mobile Ad Hoc networks by eliminating the unnecessary loops. Int J Inf Technol Comput Sci (IJITCS) 5(6):2013
Fotohi R, Ebazadeh Y, Geshlag MS (2016) A new approach for improvement security against DoS attacks in vehicular ad-hoc network. Int J Adv Comput Sci Appl 7(7):10–16
Fotohi R, Heydari R, Jamali S (2016) A Hybrid routing method for mobile ad-hoc networks. J Adv Comput Res 7(3):93–103
Childs LN (2019) RSA cryptography and prime numbers. Cryptology and error correction. Springer, Cham, pp 135–151
Yang XS (2009) Firefly algorithms for multimodal optimization. In: International symposium on stochastic algorithms. Springer, Berlin, pp 169–178
Mohd N, Singh A, Bhadauria HS (2019) A novel SVM based IDS for distributed denial of sleep strike in wireless sensor networks. Wirel Pers Commun. https://doi.org/10.1007/s11277-019-06969-9
Bhattasali T, Chaki R (2012) AMC model for denial of sleep attack detection. arXiv preprint arXiv:1203.1777
Bhattasali T, Chaki R, Sanyal S (2012) Sleep deprivation attack detection in wireless sensor network. arXiv preprint arXiv:1203.0231
Bhattasali T, Chaki R (2011) Lightweight hierarchical model for HWSNET. arXiv preprint arXiv:1111.1933
Bhushan B, Sahoo G (2018) Recent advances in attacks, technical challenges, vulnerabilities and their countermeasures in wireless sensor networks. Wirel Pers Commun 98(2):2037–2077
Periyanayagi S, Sumathy V (2013) Swarm based defense technique for denial-of-sleep attacks in wireless sensor networks. Int Rev Comput Softw (IRECOS) 8(6):1263–1270
Krentz KF, Meinel C (2019) Denial-of-sleep defenses for IEEE 802.15. 4 coordinated sampled listening (CSL). Comput Netw 148:60–71
Chen RC, Hsieh CF, Huang YF (2010) An isolation intrusion detection system for hierarchical wireless sensor networks. JNW 5(3):335–342
Rughiniş R, Gheorghe L (2010) Storm control mechanism in wireless sensor networks. In: 9th RoEduNet IEEE International Conference. IEEE, pp 430–435
Hsueh CT, Wen CY, Ouyang YC (2015) A secure scheme against power exhausting attacks in hierarchical wireless sensor networks. IEEE Sens J 15(6):3590–3602
Kalnoor G, Agarkhed J (2018) Detection of intruder using KMP pattern matching technique in wireless sensor networks. Proc Comput Sci 125:187–193
Krentz KF, Meinel C, Graupner H (2017) Countering three denial-of-sleep attacks on ContikiMAC. In: EWSN.pp 108–119
Gunasekaran M, Periakaruppan S (2017) GA-DoSLD: genetic algorithm based denial-of-sleep attack detection in WSN. Secur Commun Netw 2017:1–10
Keerthana G, Padmavathi G (2016) Detecting sinkhole attack in wireless sensor network using enhanced particle swarm optimization technique. Int J Secur Appl 10(3):41–54
Mahalakshmi G, Subathra P (2018) Denial of sleep attack detection using mobile agent in wireless sensor networks. Int J Res Trends Innov 3(5):139–149
Jamali S, Fotohi R (2017) DAWA: Defending against wormhole attack in MANETs by using fuzzy logic and artificial immune system. J Supercomput 73(12):5173–5196
Fotohi R (2020) Securing of unmanned aerial systems (UAS) against security threats using human immune system. Reliab Eng Syst Saf 193:106675
Li J, Serpen G (2016) Adaptive and intelligent wireless sensor networks through neural networks: an illustration for infrastructure adaptation through Hopfield network. Appl Intell 45(2):343–362
Sarkohaki F, Fotohi R, Ashrafian V (2017) An efficient routing protocol in mobile ad-hoc networks by using artificial immune system. Int J Adv Comput Sci Appl (IJACSA) 8(4):554–561
Al Ameen M, Liu J, Kwak K (2012) Security and privacy issues in wireless sensor networks for healthcare applications. J Med Syst 36(1):93–101
Behzad S, Fotohi R, Balov JH, Rabipour MJ (2018) An artificial immune based approach for detection and isolation misbehavior attacks in wireless networks. JCP 13(6):705–720
Jamali S, Fotohi R, Analoui M (2018) An artificial immune system based method for defense against wormhole attack in mobile adhoc networks. Tabriz J Electr Eng 47(4):1407–1419
Behzad S, Fotohi R, Dadgar F (2015) Defense against the attacks of the black hole, gray hole and wormhole in MANETs based on RTT and PFT. Int J Comput Sci Netw Solut (IJCSNS) 3:89–103
Talpur A, Shaikh FK, Baloch N, Felemban E, Khelil A, Alm MM (2019) Validation of wired and wireless interconnected body sensor networks. Sensors 19(17):3697
Heinzelman WR, Chandrakasan A, Balakrishnan H (2000) Energy-efficient communication protocol for wireless microsensor networks. In: System sciences, 2000. Proceedings of the 33rd Annual Hawaii International Conference on. 2000. IEEE
Jamali S, Fotohi R (2016) Defending against wormhole attack in MANET using an artificial immune system. New Rev Inf Network 21(2):79–100
Fotohi R, Jamali S, Sarkohaki F, Behzad S (2013) An improvement over AODV routing protocol by limiting visited hop count. Int J Inf Technol Comput Sci (IJITCS) 5(9):87–93
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Fotohi, R., Firoozi Bari, S. A novel countermeasure technique to protect WSN against denial-of-sleep attacks using firefly and Hopfield neural network (HNN) algorithms. J Supercomput 76, 6860–6886 (2020). https://doi.org/10.1007/s11227-019-03131-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-019-03131-x