Abstract
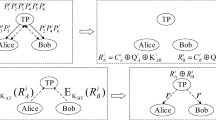
In this paper, we propose a quantum private comparison protocol based on entanglement swapping, where two distrustful parties can compare the values of their secrets with the help of a semi-trusted third party. The protocol can determine not only whether two secrets are equal, but also the size relationship between them. The two parties can deduce the comparison result based on the keys shared between them and the announcement of the third party. Others including the third party will learn nothing about the values of the secrets, as well as the comparison result. The security of our protocol is analyzed. Furthermore, all the particles can be reused in the same protocol model theoretically. So our protocol is efficient and feasible to expand in network service, which in turn gives a solution to the left problem in Lin et al. (Quantum Inf Process, doi:10.1007/s11128-012-0395-6, 2012).
Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: in IEEE International Conference on Computers, Systems and Signal Processing. IEEE, New York: Bangalore, pp. 175–179 (1984)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121–3124 (1992)
Bose, S., Vedral, V., Knight, P.L.: Multiparticle generalization of entanglement swapping. Phys. Rev. A. 57, 822 (1998)
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Boudot, F., Schoenmakers, B., Traore, J.: A fair and efficient solution to the socialist millionaires problem. Discr. Appl. Math. (Special Issue on Coding and Cryptology) 111, 23–25 (2001)
Cerf, N.J., Bourennane, M., et al.: Security of quantum key distribution using d-level systems. Phys. Rev. Lett. 88, 127902 (2002)
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283, 1561–1565 (2010)
Deng, F.G., Long, G.L., Liu, X.S.: Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A. 68, 042317 (2003)
Ekert, A.K.: Quantum cryptography based on Bell theorem. Phys. Rev. Lett. 67(6), 661–663 (1991)
Gao, F., Qin, S.J., Wen, Q.Y., Zhu, F.C.: A simple participant attack on the BradlerCDusek protocol. Quantum Inf. Comput. 7, 329 (2007)
Guo, F.Z., Qin, S.J., Wen, Q.Y., Zhu, F.C.: Cryptanalysis and improvement of two GHZ-state-based QSDC protocols. Chin. Phys. Lett. 27(9), 090307 (2010)
Guo, F.Z., Gao, F., Wen, Q.Y., Zhu, F.C.: A two-step channel-encrypting quantum key distribution protocol. Int. J. Quantum Inf. 8(6), 1013–1022 (2010)
Hillery, M., Buzěk, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A. 59, 1829–1834 (1999)
Jia, H.Y., Wen, Q.Y., Song, T.T., Gao, F.: Quantum protocol for millionaire problem. Opt. Commun. 284, 545–549 (2011)
Jia, H.Y., Wen, Q.Y., Li, Y.B., Gao, F.: Quantum private comparison using genuine four-particle entangled states. Int. J. Theor. Phys. 51, 1187–1194 (2012)
Karimipour, V., Bahraminasab, A.: Quantum key distribution for d-level systems with generalized Bell states. Phys. Rev. A. 65, 052331 (2002)
Lin, S., Sun, Y.,. Liu, X.F, Yao, Z.Q.: Quantum private comparison protocol with d-dimensional Bell states. Quantum. Inf. Process., doi:10.1007/s11128-012-0395-6 (2012)
Lin, S., Wen, Q.Y., Gao, F., Zhu, F.C.: Quantum secure direct communication with chi-type entangled states. Phys. Rev. A. 78, 064304 (2008)
Liu, B., Gao, F., Jia, H.Y., Huang, W., Zhang, W.W., Wen, Q.Y.: Efficient quantum private comparison employing single photons and collective detection. Quantum. Inf. Process., doi:10.1007/s11128-012-0439-y, (2012)
Liu, W., Wang, Y.B.: Quantum private comparison based on GHZ entangled states. Int. J. Theor. Phys., doi:10.1007/s10773-012-1246-z
Liu, W., Wang, Y.B., Jiang, Z.T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun. 284, 3160–3163 (2011)
Liu, B., Gao, F., Wen, Q.Y.: Single-photon multiparty quantum cryptographic protocols with collective detection. IEEE J. Quantum Electron. 47, 1389–1390 (2011)
Liu, W., Wang, Y.B., Cui, W.: Quantum private comparison protocol based on bell entangled states. Commun. Theor. Phys. 57, 583–588 (2012)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z.: A protocol for the quantum private comparison of equality with \(\chi \)-type state. Int. J. Theor. Phys. 51, 69–77 (2012)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z., Cui, W.: New quantum private comparison protocol using \(\chi \)-type state. Int. J. Theor. Phys. 51, 1953–1960 (2012)
Lo, H.K.: Insecurity of quantum secure computations. Phys. Rev. A. 56(2), 1154–1162 (1997)
Ma, J.J., Guo, F.Z., Yang, Q., et al.: Semi-loss-tolerant strong coin flipping protocol using EPR pairs. Quantum Inf. Comput. 12, 0490–0501 (2012)
Pan, J.W., Bouwmeester, D., et al.: Experimental entanglement swapping: entangling photons that never interacted. Phys. Rev. Lett. 80, 3891 (1998)
Steane, A.: Quantum computing. Rep. Prog. Phys. 61, 117–173 (1998)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum. Inf. Process. 11, 373–384 (2012)
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Comment on “quantum private comparison protocols with a semi-honest third party”. Quantum. Inf. Process., doi:10.1007/s11128-012-0433-4 (2012)
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A-Math. Theor. 42, 055305 (2009)
Yang, Y.G., Cao, W.F., Wen, Q.Y.: Secure quantum private comparison. Phys. Scr. 80(6), 065002 (2009)
Yao, A.C.: Protocols for secure computations. In: Proceedings of 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82). Washington, DC, USA, pp. 160 (1982)
Zhang, W.W., Gao, F., Liu, B., et al.: A quantum watermark protocol. Int. J. Theor. Phys. doi:10.1007/s10773-012-1354-9 (2012)
Zhang, W.W., Gao, F., Liu, B. et al.: A watermark strategy for quantum images based on quantum fourier transform. Quantum. Inf. Process. doi:10.1007/s11128-012-0423-6 (2012)
Zukowski, M., Zeilinger, A., Horne, M.A., Ekert, A.K.: “Event-ready-detectors” Bell experiment via entanglement swapping. Phys. Rev. Lett. 71, 4287 (1993)
Acknowledgments
This work is supported by NSFC (Grant Nos. 61272057, 61170270, 61100203, 61003286, 61121061), NCET (Grant No. NCET-10-0260), SRFDP (Grant No. 20090005110010), Beijing Natural Science Foundation (Grant Nos. 4112040, 4122054), the Fundamental Research Funds for the Central Universities (Grant No. 2011YB01, 2012RC0710).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Guo, F.Z., Gao, F., Qin, S.J. et al. Quantum private comparison protocol based on entanglement swapping of \(d\)-level Bell states. Quantum Inf Process 12, 2793–2802 (2013). https://doi.org/10.1007/s11128-013-0536-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-013-0536-6