Abstract
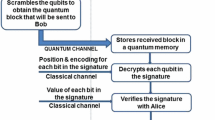
We illustrate the principle of a cryptographic switch for a quantum scenario, in which a third party (Charlie) can control to a continuously varying degree the amount of information the receiver (Bob) receives, after the sender (Alice) has sent her information through a quantum channel. Suppose Charlie transmits a Bell state to Alice and Bob. Alice uses dense coding to transmit two bits to Bob. Only if the 2-bit information corresponding to the choice of the Bell state is made available by Charlie to Bob can the latter recover Alice’s information. By varying the amount of information Charlie gives, he can continuously alter the information recovered by Bob. The performance of the protocol as subjected to the squeezed generalized amplitude damping channel is considered. We also present a number of practical situations where a cryptographic switch would be of use.
Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: “Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, pp. 175–179. Bangalore (1984)
Ekert A.K.: Quantum cryptography based on Bells theorem. Phys. Rev. Lett. 67, 661–663 (1991)
Bennett C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Hillery M., Buzek V., Bertaiume A.: Quantum secret sharing. Phys. Rev. A 59, 1829–1834 (1999)
Shimizu K., Imoto N.: Communication channels secured from eavesdropping via transmission of photonic Bell states. Phys. Rev. A 60, 157–166 (1999)
Bostrom K., Felbinger T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Goldenberg L., Vaidman L.: Quantum cryptography based on orthogonal states. Phys. Rev. Lett. 75, 1239–1243 (1995)
Lucamarini M., Mancini S.: Secure deterministic communication without entanglement. Phys. Rev. Lett. 94, 140501 (2005)
Long G. et al.: Quantum secure direct communication and deterministic secure quantum communication. Front. Phys. China 2, 251–272 (2007)
Li X.H. et al.: Deterministic secure quantum communication without maximally entangled states. J. Korean Phys. Soc. 49, 1354–1359 (2006)
Yan F.L., Zhang X.: A scheme for secure direct communication using EPR pairs and teleportation. Eur. Phys. J. B 41, 75–78 (2004)
Man Z.X., Zhang Z.J., Li Y.: Deterministic secure direct communication by using swapping quantum entanglement and local unitary operations. Chin. Phys. Lett. 22, 18–21 (2005)
Zhu A.D., Xia Y., Fan Q.B., Zhang S.: Secure direct communication based on secret transmitting order of particles. Phys. Rev. A 73, 022338 (2006)
Tsai C.W., Hsieh C.R., Hwang T.: Dense coding using cluster states and its application on deterministic secure quantum communication. Eur. Phys. J. D 61, 779–783 (2011)
Bennett C.H., Wiesner S.J.: Communication via one- and two-particle operators on Einstein-Podolsky-Rosen states. Phys. Rev. Lett. 69, 2881–2884 (1992)
Adhikari, S., Chakrabarty, I., Agrawal, P.: Probabilistic secret sharing through noisy quantum channels, arXiv:1012.5570v2
Jia H.Y., Wen Q.Y., Song T.T., Gao F.: Quantum protocol for millionaire problem. Opt. Commun. 284, 545 (2011)
Giannotti F., Pedreschi D.: Mobility, Data Mining and Privacy: Geographic Knowledge Discovery. Springer, New York (2008)
Brassard G., Broadent A., Fitzsimons J., Gambs S.: Anonymous quantum communication. Lect. Notes Comput. Sci. 4833, 460–473 (2007)
Nielsen M., Chuang I.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2000)
Srikanth R., Banerjee S.: Squeezed generalized amplitude damping channel. Phys. Rev. A 77, 012318 (2008)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Srinatha, N., Omkar, S., Srikanth, R. et al. The quantum cryptographic switch. Quantum Inf Process 13, 59–70 (2014). https://doi.org/10.1007/s11128-012-0487-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-012-0487-3