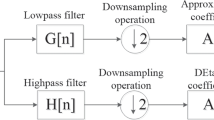
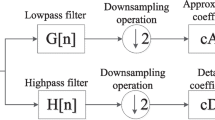
Abstract
Many audio applications such as audio surveillance and human acoustic health monitoring require security protections for audio streaming over WSNs. The process of watermarking which embeds small amounts of data (i.e., the watermark) into the original audio is an effective technique to ensure the integrity of received audio data at the receiver in energy-constrained WSNs. However, the selection of positions to embed watermark into audio streams is critical to both received audio quality and watermarking authentication performance in error-prone wireless transmission environments. In this paper we propose an approach that dynamically determines the range of middle sub-band components for embedding the watermark with minimum quality distortions, based on psycho-acoustic models and adaptive sub-band thresholds. In addition, through unequal network resource allocation schemes the proposed approach protects both middle sub-bands and high sub-bands, which include the important audio components. Our theoretical analysis and simulation results demonstrate that the proposed quality-driven energy-efficient watermarking approach for audio transmissions can achieve considerable performance gains in WSNs.







Similar content being viewed by others
References
Arnold M (2000) Audio watermarking: features, applications and algorithms. In: Proc. IEEE international conference on multimedia and Expo (ICME ’00). New York, NY, USA, pp 1013–1016
Bassia P, Pitas I, Nikolaidis N (2001) Robust audio watermarking in the time domain. IEEE Trans Multimedia 3(2):232–241
Boney L, Tewfik AH, Hamdy KN (1996) Digital watermarks for audio signals. In: Proc. 3rd IEEE int conf multimedia computing and systems, pp 473–480
Boney L, Tewfik AH, Hamdy KN (1996) Digital watermarks for audio signals. In: Proc. VIII European signal proc. conf. (EUSIPCO ’96). Trieste, Italy
Daniel G, Anthony L, Walter B (1996) Echo hiding, vol 1174. Lecture Notes in Computer Science, Information Hiding. Springer, Berlin, Germany, pp 295–315
Ge X, Huang K, Wang C, Hong X, Yang X (2011) Capacity analysis of a multi-cell multi-antenna cooperative cellular network with co-channel interference. IEEE Trans Wirel Commun (TWC) 10(10):3298–3330
Haitsma J, Kalker T, Oostveen J (2001) Robust audio hashing for content identification. In: Proc international workshop content-based multimedia indexing. Brescia, Italy
Humar I, Ge X, Xiang L, Jo M, Chen M, Zhang J (2011) Rethinking energy-efficiency models of cellular networks with embodied energy. IEEE Netw 25(3):40–49
Khalifeh CA, Yousefi’zadeh H (2008) An optimal UEP scheme of audio transmission over MIMO wireless links. In: Proc. wireless communications and networking conference, 31 March–3 April 2008, pp 3191–3196
Lai CF, Huang Y, Chao HC (2010) DLNA-based multimedia sharing system for OSGI framework with extension to P2P network. IEEE Systems Journal 4(2):262–270
Li X, Yu H (2000) Transparent and robust audio data hiding in sub-band domain. In: Proc. IEEE int conf information technology: coding and computing, pp 74–79
Li Z, Sun Q, Lian Y, Chang WC (2007) Joint source-channel-authentication resource allocation and unequal authenticity protection for multimedia over wireless networks. IEEE Trans Multimedia 9(4):837–850
Lin C-Y, Chang S-F (1998) A robust image authentication method surviving JPEG lossy compression. SPIE Storage and Retrieval of Image/Video Database 3312:296–307
Lin C-Y, Chang S-F (2001) A robust image authentication method distinguishing JPEG compression from malicious manipulation. IEEE Transaction on Circuits System and Video Technology 11(2):153–168
Lin K, Lai CF, Liu X, Guan X (2011) Energy efficiency routing with node compromised resistance in wireless sensor networks. Mobile Networks and Applications. doi:10.1007/s11036-010-0287-x
Neubauer C, Herre J (1998) Digital watermarking and its influence on audio quality. In: Proc. 105th AES convention, audio engineering society. San Francisco (preprint 4823)
Neubauer C, Herre J (2000) Audio watermarking MPEG-2 AAC bitstream. In: 108th AES convention, audio engineering society. Paris (preprint 5101)
Neubauer C, Herre J (2001) Advanced audio watermarking and applications. In: 109th AES convention, audio engineering society. Los Angeles (preprint 5176)
Perkins C, Hodso O, Hardman V (1998) A survey of packet loss recovery techniques for streaming audio. IEEE Network, pp 40–48
Qiao L, Nahrstedt K (1999) Non-invertible watermarking methods for MPEG encoded audio. In: Wong PW, Delp EJ (eds) Proc. SPIE, security and watermarking of multimedia contents, vol 3657, pp 194–202
Skraparlis D (2003) Design of an efficient authentication method for modern image and video. IEEE Trans Consum Electron 49(2):417–426
Sun Q, Chang S (2005) A secure and robust digital signature scheme for JPEG2000 image authentication. IEEE Trans. Multimedia 7(3):480–494
van Dam T, Langendoen K (2003) An adaptive energy-efficient MAC protocol for wireless sensor networks. In: Proc. Sensys‘03
Wang H, Hempel M, Peng D, Wang W, Sharif H, Chen HH (2010) Index-based selective audio encryption for wireless multimedia sensor networks. IEEE Trans Multimedia 12(3):215–223. doi:10.1109/TMM.2010.2041102
Wang H, Peng D, Wang W, Sharif H, Chen HH (2008) Energy-aware adaptive watermarking for real-time image delivery in wireless sensor networks. In: Proc. IEEE international conference on communications (ICC)
Wang W, Peng D, Wang H, Sharif H, Chen HH (2008) Energy-constrained distortion reduction optimization for wavelet-based coded image transmission in wireless sensor networks. IEEE Trans Multimedia (TMM) 10(6):1169–1180
Wang H, Peng D, Wang W, Sharif H, Chen HH (2009) Image transmission with security enhancement based on region and path diversity in wireless sensor networks. IEEE Trans Wirel Commun (TWC) 8(2):757–765
Wang Y, Ahmaniemi A, Isherwood D, Huang W (2003) Content-based UEP: a new scheme for packet loss recovery in music streaming. In: Proc. the eleventh ACM international conference on multimedia. ACM Press, New York, NY, USA, pp 412–421
Wu C-P, Kuo C-CJ (2002) Comparison of two speech content authentication approaches. In: Photonics West, vol 4675. San Jose, Calif, USA, pp 158–169
Wu Z, Bilgin A, Marcellin M (2005) Joint source/channel coding for multiple images. IEEE Trans Commun 53(10):1648–1654
Zhou L, Chao H (2011) Multimedia traffic security architecture for internet of things. IEEE Netw 25(3):35–40
Zhou L, Chao H, Vasilakos A (2011) Joint forensics-scheduling strategy for delay-sensitive multimedia applications over heterogeneous networks. IEEE J Sel Areas Commun 29(7):1358–1367
Acknowledgements
The work of Min Chen was supported in part by the Program for New Century Excellent Talents in University (NCET), and through the National Research Foundation of Korea (NRF) grant funded by the Korean government (MEST) (No. 2011-0009454).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, H., Wang, W., Chen, M. et al. Quality-driven secure audio transmissions in wireless multimedia sensor networks. Multimed Tools Appl 67, 119–135 (2013). https://doi.org/10.1007/s11042-011-0928-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-011-0928-5