Abstract
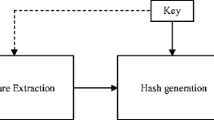
Image hash is a content-based compact representation of an image for applications such as image copy detection, digital watermarking, and image authentication. This paper proposes a lexicographical-structured framework to generate image hashes. The system consists of two parts: dictionary construction and maintenance, and hash generation. The dictionary is a large collection of feature vectors called words, representing characteristics of various image blocks. It is composed of a number of sub-dictionaries, and each sub-dictionary contains many features, the number of which grows as the number of training images increase. The dictionary is used to provide basic building blocks, namely, the words, to form the hash. In the hash generation, blocks of the input image are represented by features associated to the sub-dictionaries. This is achieved by using a similarity metric to find the most similar feature among the selective features of each sub-dictionary. The corresponding features are combined to produce an intermediate hash. The final hash is obtained by encoding the intermediate hash. Under the proposed framework, we have implemented a hashing scheme using discrete cosine transform (DCT) and non-negative matrix factorization (NMF). Experimental results show that the proposed scheme is resistant to normal content-preserving manipulations, and has a very low collision probability.








Similar content being viewed by others
References
Fridrich J, Goljan M (2000) Robust hash functions for digital watermarking. In: Proceedings of IEEE International Conference on Information Technology: Coding and Computing (ITCC’00), Las Vergas, USA, Mar. 27–29, 2000, pp 178–183
Ground Truth Database, http://www.cs.washington.edu/research/imagedatabase/groundtruth/. Accessed 8 May 2008
Kozat SS, Mihcak K, Venkatesan R (2004) Robust perceptual image hashing via matrix invariants. In: Proceedings of IEEE Conference on Image Processing (ICIP’04), Singapore, Oct. 24–27, 2004, pp 3443–3446
Lefebvre F, Macq B, Legat J-D (2002) RASH: Radon soft hash algorithm. In: Proceedings of European Signal Processing Conference (EUSIPCO’02), Toulouse, France, Sep. 3–6, 2002, pp 299–302
Lehmann EL, Romano JP (2005) Testing statistical hypotheses, 3rd edn. Springer, New York, pp 590–599
Lin Y, Chang SF (2001) A robust image authentication system distinguishing JPEG compression from malicious manipulation. IEEE Trans Circuits Syst Video Technol 11(2):153–168
Mao Y, Wu M (2007) Unicity distance of robust image hashing. IEEE Trans Inf Forensics Secur 2(3):462–467
Monga V, Evans BL (2006) Perceptual image hashing via feature points: performance evaluation and trade-offs. IEEE Trans Image Process 15(11):3453–3466
Monga V, Mihcak MK (2007) Robust and secure image hashing via non-negative matrix factorizations. IEEE Trans Inf Forensics Secur 2(3):376–390
Petitcolas FAP (2000) Watermarking schemes evaluation. IEEE Signal Process Mag 17(5):58–64
Roover CD, Vleeschouwer CD, Lefebvre F, Macq B (2005) Robust video hashing based on radial projections of key frames. IEEE Trans Signal Process 53(10):4020–4036
Swaminathan A, Mao Y, Wu M (2006) Robust and secure image hashing. IEEE Trans Inf Forensics Secur 1(2):215–230
Tang Z, Wang S, Zhang X, Wei W, Su S (2008) Robust image hashing for tamper detection using non-negative matrix factorization. Journal of Ubiquitous Convergence and Technology 2(1):18–26
Tang Z, Wang S, Zhang X, Wei W (2009) Perceptual similarity metric resilient to rotation for application in robust image hashing. In: Proceedings of the 3rd International Conference on Multimedia and Ubiquitous Engineering (MUE’09), Qingdao, China, June 4–6, 2009, pp 183–188
USC-SIPI Image Database, http://sipi.usc.edu/services/database/database.html. Accessed 12 Jan. 2007
Venkatesan R, Koon S-M, Jakubowski MH, Moulin P (2000) Robust image hashing. In: Proceedings of IEEE International Conference on Image Processing (ICIP’00), Vancouver, Canada, Sep. 10–13, 2000, pp 664–666
Wang S, Zhang X (2007) Recent development of perceptual image hashing. Journal of Shanghai University 11(4):323–331
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13(4):600–612
Wang S, Lu X, Su S, Zhang X (2007) Image block feature vectors based on a singular-value information metric and color-texture description. Journal of Shanghai University 11(3):205–209
Acknowledgements
This work was supported by the Natural Science Foundation of China (60773079, 60872116, and 60832010), the High-Tech Research and Development Program of China (2007AA01Z477), and the Innovative Research Foundation of Shanghai University for Ph.D. Programs (shucx080148). The authors would like to thank the anonymous referees for their valuable comments and suggestions.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tang, Z., Wang, S., Zhang, X. et al. Lexicographical framework for image hashing with implementation based on DCT and NMF. Multimed Tools Appl 52, 325–345 (2011). https://doi.org/10.1007/s11042-009-0437-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-009-0437-y