Abstract
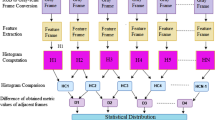
This paper addresses the problem of ensuring the integrity of a digital video and presents a scalable signature scheme for video authentication based on cryptographic secret sharing. The proposed method detects spatial cropping and temporal jittering in a video, yet is robust against frame dropping in the streaming video scenario. In our scheme, the authentication signature is compact and independent of the size of the video. Given a video, we identify the key frames based on differential energy between the frames. Considering video frames as shares, we compute the corresponding secret at three hierarchical levels. The master secret is used as digital signature to authenticate the video. The proposed signature scheme is scalable to three hierarchical levels of signature computation based on the needs of different scenarios. We provide extensive experimental results to show the utility of our technique in three different scenarios—streaming video, video identification and face tampering.
Similar content being viewed by others
References
Atrey PK, Yan WQ, Chang EC, Kankanhalli MS (2004) A hierarchical signature scheme for robust video authentication using secret sharing. In: International multi-media modelling conference, Brisbane, Australia, pp 330–337
Celik MU, Sharma G, Tekalp AM, Saber ES (2002) Video authentication with self-recovery. In: SPIE: security and watermarking of multimedia contents IV, vol 4675. San Jose, CA, pp 531–541
Daniel C, Bijan M (2002) Watermarking for self-authentication of compressed video. In: IEEE international conference on image processing, vol II. Rochester, NY, pp 913–916
Dittman J, Steinmetz A, Steinmetz R (1999) Content based digital signature for motion pictures authentication and content-fragile watermarking. In: IEEE international conference on multimedia computing and systems, vol 2. Firenze, Italy, p 204
Divakaran A, Radhakrishnan R, Peker KA (2002) Motion activity based extraction of key frames from video shots. In: IEEE international conference on image processing, vol I. Rochester, NY, pp 932–935
Du R, Fridrich J (2002) Lossless authentication of MPEG-2 video. In: IEEE international conference on image processing, vol II. Rochester, NY, pp 893–896
Eskicioglu AM (2001) A prepositioned secret sharing scheme for message authentication in broadcast networks. In: The 5th joint working conference on communications and multimedia security, Darmstadt, Germany, pp 363–373
He D, Sun Q, Tian Q (2003) A semi-fragile object based video authentication system. In: IEEE international symposium on circuits and systems, vol III. Bangkok, Thailand, pp 814–817
Lang ST, Peticolos FA (2003) Authentication of MPEG-4 data: risks and solutions. In: SPIE international conference on security and watermarking of multimedia contents V, vol 5020. Santa Clara, CA, pp 452–461
Lin CY, Chang SF (1999) Issues and solutions for authenticating MPEG video. In: IEEE international conference on acoustics, speech and signal processing, pp 54–65
Mobasseri BG, Sieffert MJ, Simard RJ (2000) Content authentication and tamper detection in digital video. In: IEEE international conference on image processing, vol I. Vancouver, BC, Canada, pp 458–461
Qi Y, Liu T, Hauptmann A (2004) Supervised classification of video shot segmentation. In: IEEE international conference on multimedia and expo, vol II. Baltimore, MD, pp 689–692
Quisquater JJ, Marc J, Macq B, Degand N, Bernard A (1997) Practical solutions to authentication of images with a secure camera. In: SPIE international conference on storage and retrieval for image and video databases V, vol 3022. San Jose, CA, pp 290–297
Radhakrishnan R, Xiong Z, Memon ND (2003) On the security of visual hash function. In: SPIE international conference annual symposium on electronic imaging: Science and technology, vol 5020. Santa Clara, CA, pp 644–652
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Stinson DR (1995) Cryptography: Theory and Practice, 1st edn, Chap 11. CRC Press, Boca Raton
Tzeng CH, Tsai WH (2001) A new technique for authentication of image/video for multimedia applications. In: Multimedia and security workshop at ACM multimedia, Ottawa, Canada
Yan WQ, Kankanhalli MS (2003) Motion trajectory based video authentication. In: IEEE international symposium on circuits and systems, vol III. Bangkok, Thailand, pp 810–813
Yin P, Yu HH (2002) A semi-fragile watermarking system for MPEG video authentication. In: International conference on acoustic speech and signal processing, vol IV. Orlando, FL, pp 3461–3464
Zhang HJ, Wu J, Zhong D, Smoliar S (1997) An integrated system for content-based video retrieval and browsing. Pattern Recogn 30(4):643–658
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Atrey, P.K., Yan, WQ. & Kankanhalli, M.S. A scalable signature scheme for video authentication. Multimed Tools Appl 34, 107–135 (2007). https://doi.org/10.1007/s11042-006-0074-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-006-0074-7