Abstract
An important pursuit by a body of criminological research is its endeavor to determine whether interventions or policy changes effectively achieve their intended goals. Because theories predict that interventions could either improve or worsen outcomes, estimators designed to improve the accuracy of identifying program or policy effects are in demand. This article introduces the series hazard model as an alternative to interrupted time series when testing for the effects of an intervention on event-based outcomes. It compares the two approaches through an example that examines the effects of two interventions on aerial hijacking. While series hazard modeling may not be appropriate for all event-based time series data or every context, it is a robust alternative that allows for greater flexibility in many contexts.



Similar content being viewed by others
Notes
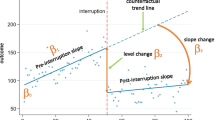
While different transfer functions can be used to model the intervention, all rely on an indicator marking the beginning of the intervention period (Cook and Campbell 1979).
Kelly and Lim (2000) discuss three approaches to account for within subject correlation: conditional, marginal, and random effects. We use the conditional approach when we include time dependent independent variables to capture the structure of dependence across the recurrent failures. For example, the analyst may include a variable that measures the number of previous failures. The marginal approach, also referred to as variance-correction, models the data as if all failures are independent, and then calculates the robust standard errors by using a sandwich estimator (Kelly and Lim 2000; Box-Steffensmeier and Zorn 2002). The random effects approach, also referred to as frailty models, introduces a random covariate into the model which accommodates the dependence across repeated failures (Kelly and Lim 2000).
Analysis of high frequency events would likely have much tied data. One strategy to avoid this problem would be to estimate the time until the next N events instead of the subsequent event.
As it turns out, in this example the substantive findings are the same whether the (0, 0] cases are deleted or recoded and retained.
The models were re-estimated after extending the end date by monthly increments for up to 36 months. Graphical displays of the estimates with 95% confidence bounds show that the findings were robust to any end date.
Arey (1972) records the year of this event as 1930, however, current FAA records record it as August 31, 1931.
Success density is measured by taking the current and six previous flights, and calculating the proportion of those flights that were successful over the number of days spanning the seven events and then calculating the natural logarithm after adding a value of 0.05 to avoid missing values. Thus, a large success density indicates that most events were successful over a relatively short period. This measure differs from the one used in Dugan et al. (2005), which only used the three most recent hijackings. I found that the one based on 7 flights better demonstrates the model and the natural logarithm is more linearly related to the Martingale residuals (Cleves et al. 2004). Both serve the same substantive purpose.
The natural logarithm of the count of days plus 0.05 is used because it produces a more linear relationship with the Martingale residuals (Cleves et al. 2004).
The results are similar when the intervention is lagged.
The asymptotic change in hijackings was calculated using \( {\frac{\omega }{{\left( {1 - \delta } \right)}}} \), where ω is the coefficient estimate for Metal Detectors and δ is the estimated rate parameter (McDowall et al. 1980).
For the restricted model, AIC = 5067.388 and BIC = 5100.361; and for the unrestricted model, AIC = 5054.063 and BIC = 5091.747.
In a separate equation that includes the Metal Detector interaction with Monthly Count, the findings remain virtually the same. A likelihood ratio test concludes that model 5 is a better fit than the more flexible model that includes the Metal Detector interaction (p = 0.2204). Furthermore, when comparing model 5 to a more restrictive model that only includes the two policy interaction, model 5 is once again preferred (p = 0.0018).
Temporal covariates can also be included in the series model. In another paper by LaFree et al. (2009), the authors model annual measures of the number of troops in Northern Ireland and the number of reported crimes. Because republican terrorists also combated loyalist terrorist groups we included the monthly total of loyalist attacks from the previous calendar month, which was found to be marginally significant.
References
Allison PD (1995) Survival analysis using the SAS system: a practical guide. SAS Institute Inc, Cary
Alt JE, King G, Signorino CS (2000) Aggregation among binary, count, and duration models: estimating the same quantities from different levels of data. Polit Anal 9:21–44
Arey JA (1972) The sky pirates. Charles Schribner’s Sons, New York
Bartholomew B (2009) Fear and darkness: anti-abortion terrorism and the United States Supreme Court. Working Paper, The University of Maryland
Box-Steffensmeier JM, Jones B (2004) Event history modeling. Cambridge University Press, New York
Box-Steffensmeier JM, Zorn C (2002) Duration models for repeated events. J Polit 64:1069–1094
Braithwaite J (1989) Crime, shame and reintegration. Cambridge University Press, Cambridge
Braithwaite J (2005) Pre-empting terrorism. Curr Iss Crim Justice 17:96–114
Brandt PT, Williams JT (2001) A linear poisson autoregressive model: the poisson AR(p) model. Polit Anal 9:164–184
Brandt PT, Williams JT (2007) Multiple time series models. Sage Publications, Inc, Thousand Oaks
Brandt PT, Williams JT, Fordham BO, Pollins B (2000) Dynamic modeling for persistent event-count time series. Am J Polit Sci 44:823–843
Chen X, Minacapelli L, Fishman S, Orehek E, Dechesne M, Segal E, Kruglanski AW (2008) Impact of political and military interventions on terrorist activities in Gaza and the West Bank: a hazard modeling analysis. Poster presented at START Workshop, September 2008. College Park, MD
Clarke RV, Felson M (eds) (1993) Routine activities and rational choice. Transaction Publishers, New Brunswick
Cleves MA, Gould WW, Gutierrez RG (2004) An introduction to survival analysis using Stata College Station. Stata Press, TX
Cook TD, Campbell DT (1979) Quasi-experimentation design & analysis issues for field settings. Houghton Mifflin Company, Boston
Cornish DB, Clarke RV (1986) The reasoning criminal: rational choice perspectives on offending. Springer, New York
Cox D (1972) Regression models and life-tables. J R Stat Soc Ser B (Methodological) 34:187–220
D’Alessio SJ, Stolzenberg L (1995) The impact of sentencing guidelines on jail incarceration in Minnesota. Criminology 33(2):283–302
Dugan L (2010) Estimating effects over time for single and multiple observations. In: Piquero A, Weisburd D (eds) Handbook of quantitative criminology. Springer, New York, pp 741–763
Dugan L, Nagin D, Rosenfeld R (2003) Exposure reduction or retaliation? The effects of domestic violence resources on intimate partner homicide. Law Soc Rev 27:169–198
Dugan L, LaFree G, Piquero AR (2005) Testing a rational choice model of airline hijackings. Criminology 43:1031–1066
Dugan L, Huang JY, LaFree G, McCauley C (2009) Sudden desistance from terrorism: the Armenian secret army for the liberation of Armenia and the Justice Commandos of the Armenian Genocide. Dyn Asymmetr Conflict (forthcoming)
Ezell ME, Land KC, Cohen LE (2003) Modeling multiple failure time data: a survey of variance-correction proportional hazards models with empirical applications to arrest data. Sociol Methods 33:111–167
Federal Aviation Administration (FAA) (1983) Aircraft hijackings and other criminal acts against civil aviation statistical and narrative reports. Office of Civil Aviation Security, Washington, DC
Freeman JR (1989) Systematic sampling, temporal aggregation, and the study of political relationships. Polit Anal 1:61–98
Gibbs JP (1975) Crime, punishment, and deterrence. Elsevier, New York
Greene WH (2008) Econometric analysis, 6th edn. Pearson Prentice Hall, Upper Saddle River
Holden RT (1986) The contagiousness of aircraft hijacking. Am J Sociol 91:874–904
Kaminski RJ, Edwards SM, Johnson JW (1998) The deterrent effects of oleoresin capsicum on assaults against police. Police Quart 1:1–20
Kelly P, Lim LL-Y (2000) Survival analysis for recurrent event data: an application to childhood infectious diseases. Stat Med 19:13–33
LaFree G, Dugan L (2007) Introducing the global terrorism database. Polit Viol Terror 19:181–204
LaFree G, Dugan L, Korte R (2009) Is counter terrorism counterproductive? Northern Ireland 1969–1992. Criminology 47:501–530
Land KC, McCall PL, Nagin DS (1996) A comparison of poisson, negative binomial, and semi-parametric mixed poisson regression models with empirical applications to criminal career data. Sociol Methods Res 24:387–442
Lawless JF (1982) Statistical models and methods for lifetime data wiley series in probabilty and mathematical statistics. Wiley, New York
Lewis-Beck MS (1986) Interrupted time series. In: Berry WD, Lewis-Beck MS (eds) New tools for social scientists. Sage Publications, Beverly Hills, pp 209–240
Lewis-Beck MS, Alford JR (1980) Can government regulate safety? The coal mine example. Am Polit Sci Rev 74:745–756
McDowall D, McCleary R, Meidinger EE, Hay RA (1980) Interrupted time series analysis. Sage Publications, Inc, Thousand Oaks
McDowall D, Lizotte AJ, Wiersema B (1991) General deterrence through civilian gun ownership: an evaluation of the quasi-experimental evidence. Criminology 29:541–559
Nagin D, Paternoster R (1991) On the relationship of past and future participation in delinquency. Criminology 29(2):163–190
Nagin D, Paternoster R (2000) Population heterogeneity and state dependence: state of the evidence and directions for future research. J Quantitat Criminol 16(2):117–144
Paternoster R (1987) The deterrent effect of the perceived certainty and severity of punishment: a review of the evidence and issues. Justice Q 4:173–217
Pridemore WA, Chamlin MB, Cochran JK (2007) An interrupted time-series analysis of Durkheim’s social deregulation thesis: the case of the Russian federation. Justice Q 24:271–290
Pridemore WA, Chamlin MB, Trahan A (2008) A test of competing hypotheses about homicide following terrorist attacks: an interrupted time series analysis of September 11 and Oklahoma City. J Quant Criminol 24:381–396
Shellman SM (2004a) Time series intervals and statistical inference: the effects of temporal aggregation on event data analysis. Polit Anal 12:97–104
Shellman SM (2004b) Measuring the intensity of international political events data: two interval-like scales. Int Interact 30:109–141
Shellman SM (2008) Coding disaggregated intrastate conflict: machine processing the behavior of substate actors over time and space. Polit Anal 16:464–477
Sherman LW (1993) Defiance, deterrence, and irrelevance: a theory of the criminal sanction. J Res Crime Delinq 30:445–473
Stata Press (2005) Stata times-series reference manual release 9. Stata Press, College Station
Stolzenberg L, D’Alessio SJ (1994) Sentencing and unwarranted disparity: an empirical assessment of the long-term impact of sentencing guidelines in Minnesota. Criminology 32(2):301–310
Varriale J (2009) The threat of radical environmental and animal rights groups: the role of moral inhibitions in ‘Monkey-Wrenching. Dissertation proposal, The University of Maryland
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Dugan, L. The Series Hazard Model: An Alternative to Time Series for Event Data. J Quant Criminol 27, 379–402 (2011). https://doi.org/10.1007/s10940-010-9127-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10940-010-9127-1