Abstract
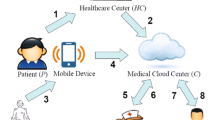
Mobile Healthcare (m-Healthcare) systems, namely smartphone applications of pervasive computing that utilize wireless body sensor networks (BSNs), have recently been proposed to provide smartphone users with health monitoring services and received great attentions. An m-Healthcare system with flaws, however, may leak out the smartphone user’s personal information and cause security, privacy preservation, or user anonymity problems. In 2012, Lu et al. proposed a secure and privacy-preserving opportunistic computing (SPOC) framework for mobile-Healthcare emergency. The brilliant SPOC framework can opportunistically gather resources on the smartphone such as computing power and energy to process the computing-intensive personal health information (PHI) in case of an m-Healthcare emergency with minimal privacy disclosure. To balance between the hazard of PHI privacy disclosure and the necessity of PHI processing and transmission in m-Healthcare emergency, in their SPOC framework, Lu et al. introduced an efficient user-centric privacy access control system which they built on the basis of an attribute-based access control mechanism and a new privacy-preserving scalar product computation (PPSPC) technique. However, we found out that Lu et al.’s protocol still has some secure flaws such as user anonymity and mutual authentication. To fix those problems and further enhance the computation efficiency of Lu et al.’s protocol, in this article, the authors will present an improved mobile-Healthcare emergency system based on extended chaotic maps. The new system is capable of not only providing flawless user anonymity and mutual authentication but also reducing the computation cost.




Similar content being viewed by others
References
Amirbekyan, A., and Estivill-Castro, V., A new efficient privacy-preserving scalar product protocol. In Proc. of AusDM'07. pp. 209–214, 2007.
Avvenuti, M., Corsini, P., Masci, P., and Vecchio, A. Opportunistic computing for wireless sensor networks. In IEEE Proc. of MASS'07. pp. 1–6, 2007.
Bergamo, P., D’Arco, P., De Santis, A., and Kocarev, L., Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circ. Syst-I 52(7):1382–1393, 2005.
D. Boneh and M. K. Franklin, Identity-based encryption from the weil pairing, in Proc. of CRYPTO’01, pp. 213–229, 2001.
Burrows, M., Abadi, M., and Needham, R. M., A logic of authentication. Proc. R. Soc. Lond. A 426(1871):233–271, 1989.
Chen, J. T., Boreli, R., and Sivaraman, V., Improving the efficiency of anonymous routing for MANETs. Comput. Commun. 35(5):619–627, 2012.
Conti, M., Giordano, S., May, M., and Passarella, A., From opportunistic networks to opportunistic computing. IEEE Commun. Mag. 48(9):126–139, 2010.
Conti, M., and Kumar, M., Opportunities in opportunistic computing. IEEE Comput. 43(1):42–50, 2010.
W. Du and M. Atallah, Privacy-preserving cooperative statistical analysis, in Proc. of ACSAC'01, pp. 102–111, 2001.
Han, S., and Chang, E., Chaotic map based key agreement with/out clock synchronization. Chaos, Solitons Fractals 39(3):1283–1289, 2009.
He, D., Chen, Y., and Chen, J., Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dyn 69(3):1149–1157, 2012.
Huang, J. L., Yeh, L. Y., and Chien, H. Y., ABAKA: An anonymous batch authenticated and key agreement scheme for value-added services in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 60(1):248–262, 2011.
Lee, C. C., Chen, C. L., Wu, C. Y., and Huang, S. Y., An extended chaotic maps-based key agreement protocol with user anonymity. Nonlinear Dyn. 69(1–2):79–87, 2012.
Lee, C. C., and Hsu, C. W., A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn. 71(1–2):201–211, 2013.
Lee, C. C., and Lai, Y. M., Toward a secure batch verification with group testing for VANET. Wirel. Netw, 2013. doi:10.1007/s11276-013-0543-7.
Li, M., Lou, W., and Ren, K., Data security and privacy in wireless body area networks. IEEE Wirel. Commun. 17(1):51–58, 2010.
Lin, X., Lu, R., Shen, X., Nemoto, Y., and Kato, N., Sage: A strong privacy-preserving scheme against global eavesdropping for Ehealth systems. IEEE J. Select. Areas Commun. 27(4):365–378, 2009.
Lin, X., Sun, X., Ho, P., and Shen, X., Gsis: A secure and privacy preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 56(6):3442–3456, 2007.
Li, M., Yu, S., Zheng, Y., Ren, K., and Lou, W., Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans. Parallel Distrib. Syst. 24(1):131–143, 2013.
Lu, H., Lane, N. D., Eisenman, S. B., and Campbell, A. T., Bubble-sensing: Binding sensing tasks to the physical world. Pervasive Mob. Comput. 6(1):58–71, 2010.
Lu, R., Lin, X., Liang, X., and Shen, X., A secure handshake scheme with symptoms-matching for Mhealthcare social network. Mob. Netw. Appl. 16(6):683–694, 2011.
R. Lu, X. Lin, X. Liang, and X. Shen, Secure handshake with symptoms-matching: the essential to the success of Mhealthcare social network, in Proc. BodyNets'10, pp. 8–15, 2010.
Lu, R., Lin, X., Luan, H., Liang, X., and Shen, X., Pseudonym changing at social spots: An effective strategy for location privacy in VANETs. IEEE Trans. Veh. Technol. 61(1):86–96, 2012.
Lu, R., Lin, X., and Shen, X., SPOC: A secure and privacy-preserving opportunistic computing framework for mobile-healthcare emergency. IEEE Trans. Parallel Distrib. Syst. 24(3):614–624, 2012.
Lu, R., Lin, X., Zhu, H., and Shen, X., An intelligent secure and privacy-preserving parking scheme through vehicular communications. IEEE Trans. Veh. Technol. 59(6):2772–2785, 2010.
J. C. Mason and D. C. Handscomb, Chebyshev polynomials Chapman & Hall/CRC Press, New York NY 10017, USA, 2003.
Miyaji, A., Nakabayashi, M., and Takano, S., New explicit conditions of elliptic curve traces for FR-reduction. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E84-A(5):1234–1243, 2001.
A. Passarella, M. Conti, E. Borgia, and M. Kumar, Performance evaluation of service execution in opportunistic computing, in Proc. of ACM MSWIM'10, pp. 291–298, 2010.
Ren, Y., Pazzi, R. W. N., and Boukerche, A., Monitoring patients via a secure and mobile healthcare system. IEEE Wirel. Commun. 17(1):59–65, 2010.
Sun, J., and Fang, Y., Cross-domain data sharing in distributed electronic health record systems. IEEE Trans. Parallel Distrib. Syst. 21(6):754–764, 2010.
Toninelli, A., Montanari, R., and Corradi, A., Enabling secure service discovery in mobile healthcare enterprise networks. IEEE Wirel. Commun. 16(3):24–32, 2009.
J. Vaidya and C. Clifton, Privacy preserving association rule mining in vertically partitioned data, in Proc. of ACM KDD'02, pp. 639–644, 2002.
J. Wessels, Application of BAN-Logic, CMG Public Sector B.V., 2001, available at http://www.win.tue.nl/ipa/archive/springdays2001/banwessels.pdf, access date: 2012/12/20.
Yoon, E. J., Efficiency and security problems of anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 17(7):2735–2740, 2012.
Yuce, M. R., Ng, S. W. P., Myo, N. L., Khan, J. Y., and Liu, W., Wireless body sensor network using medical implant band. J. Med. Syst. 31(6):467–474, 2007.
Zhang, L., Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons Fractals 37(3):669–674, 2008.
Acknowledgments
The authors would like to express their appreciation to the anonymous referees for their valuable suggestions and comments. This research was partially supported by the National Science Council, Taiwan, R.O.C., under contract no.: NSC102-2221-E-030-003.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lee, CC., Hsu, CW., Lai, YM. et al. An Enhanced Mobile-Healthcare Emergency System Based on Extended Chaotic Maps. J Med Syst 37, 9973 (2013). https://doi.org/10.1007/s10916-013-9973-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-013-9973-0