Abstract
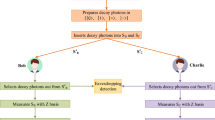
Quantum secret sharing (QSS) protocols are designed to allow a secret message to be divided into several shadows, and the secret can be reconstructed cooperatively. Motivated by the eight quantum entangled (EQE) state, a tripartite verifiable QSS scheme is proposed. It involves three agents, in four phases, i.e., shadow distribution phase, eavesdropping detection phase, measurement and secret sharing phase, verification and secret recover phase. The protocol can not only share and recover the secret correctly, but also verify whether there are dishonest participants in communication. In addition, the protocol is extended to a multiparty quantum secret sharing scheme by utilizing the unitary operations. Security analysis shows that the proposed schemes achieve the fundamental security requirements against the external and internal attackers with the aid of the quantum decoy states. It is shown that the efficiency in classical and quantum transmission is higher than the other protocols.

Similar content being viewed by others
References
Shamir, A.: How to share a secret. Commun. ACM 22, 612–613 (1979)
Blakley, G.R.: Safeguarding cryptographic keys[C]. In: 1979 International Workshop on Managing Requirements Knowledge (MARK), pp 313–318. IEEE (1979)
Cirac, J.I., Pellizzari, T., Zoller, P.: Enforcing coherent evolution in dissipative in quantum dynamics. Science 273(5279), 1207–1210 (1996)
Deutsch, D.: Quantum theory, the Church–Turing principle and the universal quantum computer. R. Soc. Lond. A. 400(1818), 97–117 (1985)
Vandersypen, L.M.K., Steffen, M., Breyta, G., et al.: Experimental realization of Shor’s quantum factoring algorithm using nuclear magnetic resonance. Nature 414(6866), 883–887 (2001)
Hillery, M., Buźek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A. 59(3), 1829 (1999)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett. 83(3), 648 (1999)
Guo, G.P., Guo, G.C.: Quantum secret sharing without entanglement. Phys. Rev. A. 310(4), 247–251 (2003)
Xiao, L., Long, G.L., Deng, F.G., et al.: Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A. 69(5), 052307 (2004)
Yan, F.L., Gao, T.: Quantum secret sharing between multiparty and multiparty without entanglement. Phys. Rev. A. 72(1), 012304 (2005)
Xiang, Y., Mo, Z.W.: Quantum secret sharing protocol based on four-dimensional three-particle entangled states. Mod. Phys. Lett. B. 30(02), 1550267 (2016)
Chen, X.B., Dou, Z., Xu, G., et al.: A kind of universal quantum secret sharing protocol. Sci. Rep. 7, 39845 (2017)
Liu, J., Liu, Y.M., Zhang, Z. J., et. al.: GeneRaliZeD multiparty quantum single-qutrit-state sharing. Int. J. Theor. Phys. 47(9), 2353–2362 (2008)
Muralidharan, S., Panigrahi, P.K.: Quantum-information splitting using multipartite cluster states. Phys. Rev. A. 78(6), 062333 (2008)
Khakbiz, P., Asoudeh, M.: Sequential quantum secret sharing in noisy environments. Quantum. Inf. Process. 18(1), 1–19 (2019)
Qin, H., Tso, R.: Efficient quantum secret sharing based on special multi-dimensional GHZ state. Opt. Quantum. Electron. 50(4), 1–10 (2018)
Ye, C.Q., Ye, T.Y.: Circular semi-quantum secret sharing using single particles. Commun. Theor. Phys. 70(6), 661 (2018)
Lai, H., Pieprzyk, J., Luo, M.X., et. al.: High-capacity (2,3) threshold quantum secret sharing based on asymmetric quantum lossy channels. Quantum Inf. Process. 19(5), 1–13 (2020)
Lee, S.M., Lee, S.W., Jeong, H., et. al.: Quantum teleportation of shared quantum secret. Phys. Rev. Lett. 124(6), 060501 (2020)
Muralidharan, S., Panigrahi, P.K.: Perfect teleportation quantum-state sharing and superdense coding through a genuinely entangled five-qubit state. Phys. Rev. A. 77(3), 032321 (2008)
Ray, M., Chatterjee, S., Chakrabarty, I.: Sequential quantum secret sharing in a noisy environment aided with weak measurements. Eur. Phys. J. D 70(5), 114 (2016)
Yu, Y.: Comment on ”Generalized Smolin states and their properties” Phys. Rev. A. 75(6), 066301 (2007)
Lin, S., Gao, F., Guo, F.Z., et. al.: Comment on ”Multiparty quantum secret sharing of classical messages based on entanglement swapping” Phys. Rev. A. 76(3), 036301 (2007)
Chor, B., Goldwasser, S., Micali, S., et al.: Verifiable secret sharing and achieving simultaneity in the presence of faults. In: Proceedings of 26th IEEE Symposium on Foundations of Computer Science, pp 383–395 (1985)
Yang, Y.G., Teng, Y.W., Chai, H.P., et. al.: Verifiable quantum (k, n)-threshold secret key sharing. Int. J. Theor. Phys. 50(3), 792–798 (2011)
Lu, C., Miao, F., Hou, J., et. al.: Verifiable threshold quantum secret sharing with sequential communication. Quantum. Inf. Process. 17(11), 310 (2018)
Cai, X., Wang, T., Zhang, R., et al.: Security of verifiable threshold quantum secret sharing with sequential communication. IEEE. Access. 7, 134854–134861 (2019)
Song, Y., Li, Y., Wang, W.: Multiparty quantum direct secret sharing of classical information with bell states and bell measurements. Int. J. Theor. Phys. 57(5), 1559–1571 (2018)
Cao, W.F., Yang, Y.G.: Verifiable quantum secret sharing protocols based on four-qubit entangled states. Int. J. Theor. Phys. 58(4), 1202–1214 (2019)
Sadeghi Zadeh, M.S., Houshmand, M., Aghababa, H.: Bidirectional teleportation of a two-qubit state by using eight-qubit entangled state as a quantum channel. Int. J. Theor. Phys. 56(7), 2101–2112 (2017)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85(26), 5635 (2000)
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China (61602172, 61972418), Natural Science Foundation of Hunan Province (2017JJ3223, 2020JJ4750), the Training Program for Excellent Young Innovators of Changsha (Grant Nos. kq1905058).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jiang, S., Liu, Z., Lou, X. et al. Efficient Verifiable Quantum Secret Sharing Schemes via Eight-Quantum-Entangled States. Int J Theor Phys 60, 1757–1766 (2021). https://doi.org/10.1007/s10773-021-04796-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-021-04796-y