Abstract
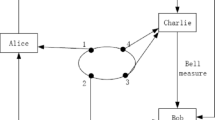
Based on the controlled quantum operation teleportation, a secure voting protocol is proposed in this paper. Genuine four-qubit entangled state functions as the quantum channel. The eligible voter’s quantum operation which represents his vote information can be transmitted to the tallyman Bob with the help of the scrutineer Charlie. Voter’s quantum identity authentication provides the anonymity of voters’ID, which is ensured by a zero-knowledge proof of the notary organization CA. Charlie’s supervision in the whole voting process can make the protocol satisfy verifiability and non-reusability so as to avoid Bob’s dishonest behaviour. The security analysis shows that the voting protocol satisfies unforgeability, and has great advantages over some relevant researches. Additionally, the quantum operation can be transmitted successfully with the probability 1, which can make the protocol reliable and practical.


Similar content being viewed by others
References
Gritzalis, D.: Secure Electronic Voting, 7 th Computer Security Incidents Response Teams Workshop Syros, Greece (2002)
Hillerv, M.: Quantum voting and privacy ptotection:first steps. Int. Soc. Opt. Eng. (2006). doi:10.1117/2.1200610.0419
Vaccaro, J.A., Spring, J., Chefles, A.: Quantum protocols for anonymous voting and surveying. Phys. Rev. A 75(1), 012333 (2007)
Wen, X.J., Cai, X.J.: Secure quantum voting protocol. Shangdong Univ.(Natural Science) 46(9), 9–13 (2011)
Yi, Z., He, G.Q., Zeng, G.H.: Quantum voting protocol using two-mode squeezed states. Acta Phys.Sin. 58(5), 3166–3172 (2009)
Horoshko, D., Kilin, S.: Quantum anonymous voting with anonymity check. Phys.Lett. A 375, 1172–1175 (2011)
Bennett, C.H., Brassard, G., Crépeau, C., et al.: Teleporting an unknown quantum state via dual classical and einstein-podolsky-rosen channels. Phys. Rev. Lett. 70, 1895–1899 (1993)
Huelga, S.F., Vaccaro, J.A., Chefles, A., et al.: Quantum remote control: Teleportation of unitary operations. Phys. Rev. A 63(4), 042303 (2001)
Zhao, N.B., Wang, A.M.: Local implementation of nonlocal operations with block form. Phys.Rev. A 78(1), 014305 (2008)
Yao, C.M., Cao, B.F.: Efficient implementation of a nonlocal gate with nonmaximal entanglement. Phys. Rev. A 373, 1011–1014 (2009)
Zhang, Z.J., Cheung, C.Y.: Shared quantum remote control: quantum operation sharing. J. Phys. B 44(16), 165508 (2011)
Wang, Y.W., Wei, X.H., Zhu, Z.H.: Quantum voting protocols based on the non-symmetric quantum channel with controlled quantum operation teleportation. Acta Phys. Sin. 62(16), 160302 (2013)
Tang, S.Q., Shan, C.J., Zhang, X.X.: Quantum teleportation of an unknown two-atom entangled state using foue-atom cluster state. Int. J. Theor. Phys. 49(8), 1899–1903 (2010)
Tao, Y.H., Zheng, J.H.: Probabilistic controlled teleportation of two-particle entangled state via the optimal quantum state. Int. J. Theor. Phys. 52(6), 2001–2007 (2013)
Yuan, W., Guo, Q., Nie, L.P., et al.: Quantum teleportation of an arbitrary two-ion state by using a genuine four-ion entangled state in ion-trap systems. Int. J. Theor. Phys. 54(7), 2170–2174 (2015)
Li, M.L., Liu, J.J., Hong, W.N.: Quantum information splitting of a single-qubit via genuine four-qubit entangled states. Acta Sinica Quantum Optica 19(2), 141–145 (2013)
Wang, Y.W., Zhan, Y.B.: A theoretical scheme for zero-knowledge proof quantum identity authentication. Acta Phys. Sin. 58(11), 7668–7671 (2009)
Wen, X.J., Tian, Y., Niu, X.M.: A strong blind quantum signature scheme protocol based on secret sharing. Acta Electronic Sinica 38(3), 720–724 (2010)
Pati, A.K., Agrawal, P.: Probabilistic teleportation of a qudit. Phys. Lett. A 371, 185–189 (2007)
Bennett, C.H., Brassard.G.: Quantum cryptography:public key distribution and coin tossing. In: Proceedings of the International Conference on Computers, IEEE, pp 175–179 (1984)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J Assoc:Comput Math 48(1), 351–406 (2001)
Inamon, H., Lutkenhaus, N., Mayers, D.: Unconditional security of practical quantum key distribution. Eur. Phys. J. D 41(3), 599–627 (2007)
Hillery, M., Ziman, M., Buzek, V., Bielikova, M.: Towards quantum-based privacy and voting. Phys. Lett. A 349(1–4), 75–81 (2006)
Wang, T.Y., Cai, X.Q., Zhang, R.L.: Security of a sessional blind signature based on quantum cryptograph. Quantum Inf. Process. 13(8), 1677–1685 (2014)
Wang, T.Y., Cai, X.Q., Ren, Y.L., et al.: Security of quantum digital signatures for classical messages. Sci. Rep. 5, 9231 (2015)
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant Nos.61402275, 61273311, 61202317), the Natural Science Foundation of Shaanxi Province (Grant No.2015JM6263), Scientific Research Plan Projects of Shaanxi Education Department(Grant No.2012JK1003), and the Fundamental Research Funds for the Central Universities(Grant No.GK201402004).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tian, JH., Zhang, JZ. & Li, YP. A Voting Protocol Based on the Controlled Quantum Operation Teleportation. Int J Theor Phys 55, 2303–2310 (2016). https://doi.org/10.1007/s10773-015-2868-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-015-2868-8