Abstract
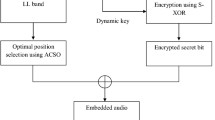
This paper proposes a multi-tier SegmEntation ECC Desegmentation (SEED) model to suit audio cryptosystem for Securing Audio sIgnal (SAIL) based on discrete wavelet transform and elliptic curve encryption. It is aimed with the prospect of enhancing the level of security in digital audio communication for unreliable public networks. The proposed SAIL system works as a multitier SEED model by performing segmentation, DWT compression, ECC encryption and desegmentation. In the reverse process, this multitier model proceeds with segmentation, decryption, decompression, and desegmentation. The novelty of this work relies on the adoption of ECC for encryption as it is first of its kind in audio streaming. The selection of appropriate ECC curve is a real challenge, and complex multiplication method has been applied. ECC has been chosen for encryption as it has been identified as a discrete logarithm problem which is resistant to be attacked by quantum computers. The performance of the recommended SAIL cryptosystem has been tested using different audio samples characterizing human voice, animal voice and Instrumental music. Analysis of the proposed model shows the effectiveness for fast audio encryption as it works on compressed data and also computationally simple. Various statistical analysis have been done on the proposed model, and the obtained result ratifies better level protection of audio signals from different security threats and can be recommended for multi channel audio processing.












Similar content being viewed by others
References
Akgül, A., & Kaçar, S. (2015). An audio data encryption with single and double dimension discrete-time chaotic systems. Turkish Online Journal of Science & Technology, 5(3), 14–23
Al Saad, S. N., & Hato, E. (2014). A speech encryption based on chaotic maps. International Journal of Computer Applications, 93(4), 19–28.
al-Karim, A., Al-Jalil, M. A., & Qays, I. (2013). Speech encryption using a chaotic map and blowfish algorithms. Journal of Basrah Researches (Sciences), 39(2), 68–76.
Alwahbani, S. M. H., & Bashier, E. B. M. (2013). Speech scrambling based on chaotic maps and one-time pad. 2013 International Conference on Computing, Electrical and Electronics Engineering (ICCEEE), IEEE (pp. 128–133).
Anees, A. (2015). An image encryption scheme based on Lorenz system for low profile applications. 3D Research, 6(3), 1–10.
Asok, S. B., et al. (2013). A secure cryptographic scheme for audio signals. 2013 International Conference on Communications and Signal Processing (ICCSP), IEEE.
Augustine, N., George, S. N., & Pattathil, D. P. (2015). An audio encryption technique through compressive sensing and Arnold transform. International Journal of Trust Management in Computing and Communications, 3(1), 74–92.
Barni, M., Bartolini, F., & Piva, A. (2001). Improved wavelet-based watermarking through pixel-wise masking. IEEE Transactions on Image Processing, 10(5), 783–791.
Chen, L. H., & Lin, J. J. (2003). Mean quantization based image watermarking. Image and Vision Computing, 21(8), 717–727.
Cichowski, J., & Czyzewski, A. (2012). Sensitive audio data encryption for multimodal surveillance systems. In Audio Engineering Society Convention 132. Audio Engineering Society.
Ciptasari, R. W., Rhee, K. H., & Sakurai, K. (2014). An enhanced audio ownership protection scheme based on visual cryptography. EURASIP Journal on Information Security, 1, 2.
Datta, K., & Gupta, I. S. (2013). Partial encryption and watermarking scheme for audio files with controlled degradation of quality. Multimedia Tools and Applications, 64(3), 649–669.
Dengre, A., & Gawande, A. D. (2015). Audio encryption and digital image watermarking in an uncompress video. International Journal of Advances in Applied Sciences, 4(2), 66–72.
Eldin, S. M. S., et al. (2015). New audio encryption package for TV cloud computing. International Journal of Speech Technology, 18(1), 131–142.
Elkholy, M. M., Hennawy, H. M. E. L., & Elkouny, A. (2015). Design and implementation of hyperchaotic masking system for secured audio transmission. 2015 Tenth International Conference on Computer Engineering & Systems (ICCES), IEEE.
Elshamy, A. M., et al. (2013). Optical image encryption based on chaotic baker map and double random phase encoding. Journal of Lightwave Technology, 31(15), 2533–2539.
Fazeen, M., Bajwa, G., & Dantu, R. (2014). Context-aware multimedia encryption in mobile platforms. Proceedings of the 9th Annual Cyber and Information Security Research Conference. ACM
Hedelin, P., Nordén, F., & Skoglund, J. (1999). SD optimization of spectral coders. 1999 IEEE Workshop on Speech Coding Proceedings, IEEE.
Iyer, S. C., Sedamkar, R. R., & Gupta, S. (2016). A novel idea on multimedia encryption using hybrid crypto approach. Procedia Computer Science, 79, 293–298.
James, S. P., George, S. N., & Deepthi, P. P. (2014). An audio encryption technique based on LFSR based alternating step generator. 2014 IEEE International Conference on Electronics, Computing and Communication Technologies (IEEE CONECCT), IEEE
Kim, S. W., Kim, Y. G., & Simon, M. K. (2004). Generalized selection combining based on the log-likelihood ratio. IEEE Transactions on Communications, 52(4), 521–524.
Kohad, H., Ingle, V. R., & Gaikwad, M. A. (2012). An overview of speech encryption techniques. International Journal of Engineering Research and Development, 3, 29–32.
Kulkarni, S. A., & Patil, S. B. (2015). A robust encryption method for speech data hiding in digital images for optimized security. 2015 International Conference on Pervasive Computing (ICPC), IEEE.
Kwon, J. K., Park, S., & Sung, D. K. (2006). Collision mitigation by log-likelihood ratio (LLR) conversion in orthogonal code-hopping multiplexing. IEEE Transactions on Vehicular Technology, 55(2), 709–717.
Langelaar, G. C., Setyawan, I., & Lagendijk, R. L. (2000). Watermarking digital image and video data. A state-of-the-art overview. IEEE Signal processing magazine, 17(5), 20–46.
Li, H., et al. (2009). A novel audio scrambling algorithm in variable dimension space. 11th International Conference on Advanced Communication Technology, 2009, ICACT. (Vol. 3, pp 1647–1651). IEEE.
Lima, J. B., & da Silva Neto, E. F. (2016). Audio encryption based on the cosine number transform. Multimedia Tools and Applications, 75(14), 8403–8418.
Lin, C. Y., & Chang, S. F. (2001). A robust image authentication method distinguishing JPEG compression from malicious manipulation. IEEE Transactions on Circuits and Systems for Video Technology, 11(2), 153–168.
Liu, H., & Wang, X. (2010). Color image encryption based on one-time keys and robust chaotic maps. Computers & Mathematics with Applications, 59(10), 3320–3327.
Lu, X., et al. (2012). Digital audio information hiding based on Arnold transformation and double random-phase encoding technique. Optik-International Journal for Light and Electron Optics, 123(8), 697–702.
Mermoul, A., & Belouchrani, A. (2010). A subspace-based method for speech encryption. 2010 10th International Conference on, Information Sciences Signal Processing and their Applications (ISSPA). IEEE.
Mostafa, A., et al. (2015). Speech encryption using two-dimensional chaotic maps. 2015 11th International Computer Engineering Conference (ICENCO), IEEE
Nguyen, H. H., Mehaoua, A., & Hong, J. W. K. (2013). Secure medical tele-consultation based on voice authentication and realtime audio/video encryption. 2013 First International Symposium on Future Information and Communication Technologies for Ubiquitous HealthCare (Ubi-HealthTech), IEEE.
Petitcolas, Fabien, A. P., Ross, J.. Anderson, & Markus, G., & Kuhn (1999). Information hiding-a survey. Proceedings of the IEEE 87(7): 1062–1078.
Rashidi, B., & Rashidi, B. (2013). FPGA based A new low power and self-timed AES 128-bit encryption algorithm for encryption audio signal. International Journal of Computer Network and Information Security, 5(2), 10.
Refregier, P., & Javidi, B. (1995). Optical image encryption based on input plane and Fourier plane random encoding. Optics Letters, 20(7), 767–769.
Sadkhan, S. B., & Mohammed, R. S. (2015). Proposed random unified chaotic map as PRBG for voice encryption in wireless communication. Procedia Computer Science, 65, 314–323.
Sharma, D. (2012). Five level cryptography in speech processing using multi hash and repositioning of speech elements. International Journal of Emerging Technology and Advanced Engineering, 2(3), 21–26
Sheu, L. J. (2011). A speech encryption using fractional chaotic systems. Nonlinear Dynamics, 65(1), 103–108.
Tamimi, A. A., & Abdalla, A. M. (2014). An audio shuffle-encryption algorithm. Proceedings of the World Congress on Engineering and Computer Science. San Francisco, USA: WCECS
Tong, X. J., et al. (2015). A fast encryption algorithm of the color image based on the four-dimensional chaotic system. Journal of Visual Communication and Image Representation, 33, 219–234.
Wang, S., & Fan, Y. (2010). A watermarking algorithm of gray image based on histogram statistical characteristics. Computer Technology and Development, 1, 045.
Washio, S., & Watanabe, Y. (2014). Security of audio secret sharing scheme encrypting audio secrets with bounded shares. 2014 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). IEEE.
Wu, Y., & Ng, B. P. (2002). Speech scrambling with Hadamard transform in the frequency domain. Signal Processing, 2002 6th International Conference on. Vol. 2. IEEE
Yang, W., Benbouchta, M., & Robert, Y. (1998). Performance of the modified bark spectral distortion as an objective speech quality measure. Acoustics, Speech and Signal Processing, 1998. Proceedings of the 1998 IEEE International Conference on. Vol. 1. IEEE.
Zeng, L., et al. (2012). Scrambling-based speech encryption via compressed sensing. EURASIP Journal on Advances in Signal Processing, 2012(1), 257.
Zhang, C., Wang, J., & Wang, X. (2008). Digital image watermarking algorithm with double encryption by Arnold transform and logistic. NCM’08 Fourth International Conference on Networked Computing and Advanced Information Management, Vol. 1. IEEE
Zhao, H., et al. (2014). Dual key speech encryption algorithm based underdetermined BSS. The Scientific World Journal. https://doi.org/10.1155/2014/974735
Acknowledgements
This part of this research work is supported by Department of Science and Technology (DST), Science and Engineering Board (SERB), Government of India under the ECR Grant (ECR/2017/000679/ES).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sasikaladevi, N., Geetha, K. & Venkata Srinivas, K.N. A multi-tier security system (SAIL) for protecting audio signals from malicious exploits. Int J Speech Technol 21, 319–332 (2018). https://doi.org/10.1007/s10772-018-9510-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10772-018-9510-0