Abstract
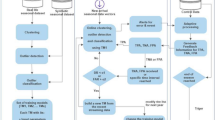
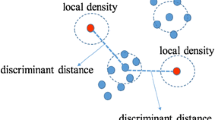
In recent times, the Internet of Things and big data analytics have become a hot research topic in mobile edge computing (MEC) desires wide-ranging research works for intelligent decision making. In this view, this paper designs an intelligent outlier detection with machine learning empowered big data analytics (IODML-BDA) for MEC. The proposed model involves an adaptive synthetic sampling-based outlier detection technique to eradicate the existence of outliers. Besides, the oppositional swallow swarm optimization (OSSO) based feature selection technique is used to choose an effective set of features. Finally, long short-term memory based classification model is employed to identify different class labels. The design of OSSO algorithm for feature selection with ADASYN technique for big data analytics show the novelty of the work. A comprehensive experimental analysis is carried out on GPS trajectories, movement prediction, water treatment plant, hepatitis, and Twitter datasets to confirm the experimental results. The experimentation outcomes pointed out that the proposed IODML-BDA model achieves the higher accuracy of 0.9735, 0.9816, 0.9798, 0.9896, and 0.9912 on the applied datasets.








Similar content being viewed by others
Data availability
Data sharing not applicable to this article as no datasets were generated during the current study.
References
Hou, Y., Garg, S., Hui, L., Jayakody, D.N.K., Jin, R., Hossain, M.S.: A data security enhanced access control mechanism in mobile edge computing. IEEE Access 8, 136119–136130 (2020)
Shafiq, M., Tian, Z., Bashir, A.K., Jolfaei, A., Yu, X.: Data mining and machine learning methods for anomaly and intrusion traffic classification: a survey. Sustain. Cities Soc. Elsevier (2020)
Khan, S., Kifayat, K., Bashir, A.K., Gurtov, A., Hassan. M.: Intelligent intrusion detection system in smart grid using computational intelligence and machine learning. Trans. Emerg. Telecommun. Technol. (2020)
Ma, X.Y.: Research on trusted cooperative mechanism based on edge computing, M.S. thesis, Dept. Abbrev., Beijing Univ. Posts Telecommun., Beijing, China (2019)
Bashir, A.K., Arul, R., Jayaram, R., Arulappan, A., Prathiba, S.B.: An optimal multitier resource allocation of cloud RAN in 5G using machine learning. Transactions on Emerging Telecommunications Technologies, Wiley (2019)
Lv, Z., Chen, D., Lou, R., Wang, Q.: Intelligent edge computing based on machine learning for smart city. Futur. Gener. Comput. Syst. 115, 90–99 (2021)
Pääkkönen, P., Pakkala, D.: Extending reference architecture of big data systems towards machine learning in edge computing environments. J. Big Data 7, 1–29 (2020)
Shafiq, M., Tian, Z., Bashir, A.K., Du, X., Guizani, M.: CorrAUC: a malicious bot-IoT traffic detection method in IoT network using machine learning techniques. IEEE Internet Things J. 8(5), 3242–3254 (2021)
Cui, G., He, Q., Chen, F., Zhang, Y., Jin, H., Yang, Y.: Interference-aware game-theoretic device allocation for mobile edge computing. IEEE Trans Mobile Comput (2021)
Liao, Z., Peng, J., Xiong, B., Huang, J.: Adaptive offloading in mobile-edge computing for ultra-dense cellular networks based on genetic algorithm. J. Cloud Comput. 10(1), 1–16 (2021)
Wang, T., Ke, H., Zheng, X., Wang, K., Sangaiah, A.K., Liu, A.: Big data cleaning based on mobile edge computing in industrial sensor-cloud. IEEE Trans. Industr. Inf. 16(2), 1321–1329 (2019)
Zhou, Z., Yu, H., Xu, C., Chang, Z., Mumtaz, S., Rodriguez, J.: BEGIN: big data enabled energy-efficient vehicular edge computing. IEEE Commun. Mag. 56(12), 82–89 (2018)
Barik, R.K., Dubey, H., Mankodiya, K.: November. SOA-FOG: Secure service-oriented edge computing architecture for smart health big data analytics. In 2017 IEEE global conference on signal and information processing (GlobalSIP), pp. 477–481. IEEE (2017)
Xu, X., Liu, Q., Luo, Y., Peng, K., Zhang, X., Meng, S., Qi, L.: A computation offloading method over big data for IoT-enabled cloud-edge computing. Futur. Gener. Comput. Syst. 95, 522–533 (2019)
Hosseini, M.P., Tran, T.X., Pompili, D., Elisevich, K. Soltanian-Zadeh, H.: Deep learning with edge computing for localization of epileptogenicity using multimodal rs-fMRI and EEG big data. In 2017 IEEE international conference on autonomic computing (ICAC), pp. 83–92. IEEE (2017)
Meng, Q., Wang, K., He, X., Guo, M.: QoE-driven big data management in pervasive edge computing environment. Big Data Min. Anal. 1(3), 222–233 (2018)
Xu, J., Ota, K., Dong, M.: Big data on the Fly: UAV-mounted mobile edge computing for disaster management. IEEE Trans. Netw. Sci. Eng. 7(4), 2620–2630 (2020)
Vengala, D.V.K., Kavitha, D., Kumar, A.S.: Secure data transmission on a distributed cloud server with the help of HMCA and data encryption using optimized CP-ABE-ECC. Clust. Comput. 23(3), 1683–1696 (2020)
Mishra, S.K., Manjula, R.: A meta-heuristic based multi objective optimization for load distribution in cloud data center under varying workloads. Cluster Comput. 1–15 (2020)
Subramanian, E.K., Tamilselvan, L.: Elliptic curve diffie–hellman cryptosystem in big data cloud security. Cluster Comput. 1–11 (2020)
Zhang, Z., Barbary, K., Nothaft, F.A., Sparks, E.R., Zahn, O., Franklin, M.J., Patterson, D.A., Perlmutter, S.: Kira: processing astronomy imagery using big data technology. IEEE Trans. Big Data 6(2), 369–381 (2016)
Neshat, M., Sepidnam, G., Sargolzaei, M.: Swallow swarm optimization algorithm: a new method to optimization. Neural Comput. Appl. 23(2), 429–454 (2013)
Kaveh, A., Bakhshpoori, T., Afshari, E.: An efficient hybrid particle swarm and swallow swarm optimization algorithm. Comput. Struct. 143, 40–59 (2014)
Tizhoosh, H.R.: Opposition-based reinforcement learning. J. Adv. Comput. Intell Intell Inform. 10(3), 578–585 (2006)
Gebrehiwot, A., Hashemi-Beni, L., Thompson, G., Kordjamshidi, P., Langan, T.E.: Deep convolutional neural network for flood extent mapping using unmanned aerial vehicles data. Sensors 19(7), 1486 (2019)
UCI machine learning repository: Data sets, https://archive.ics.uci.edu/ml/datasets.php
Acknowledgements
Taif University Researchers Supporting Project Number (TURSP-2020/154), Taif University, Taif, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
Conceptualization, RFM; formal analysis, RFM; funding acquisition, GPJ and WC; investigation, SAK; methodology, RFM and SAK; Project administration, WC; Resources, GPJ and WC; Software, IHJ and JN; supervision, GPJ; visualization, WC, IHJ and JN; writing—original draft, RFM; writing—review and editing, GPJ.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest. The manuscript was written through contributions of all authors. All authors have given approval to the final version of the manuscript.
Consent to participate
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mansour, R.F., Abdel-Khalek, S., Hilali-Jaghdam, I. et al. An intelligent outlier detection with machine learning empowered big data analytics for mobile edge computing. Cluster Comput 26, 71–83 (2023). https://doi.org/10.1007/s10586-021-03472-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03472-4