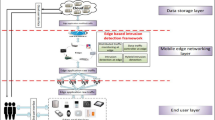
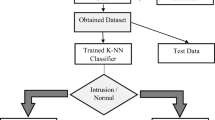
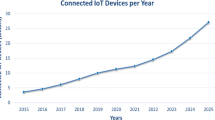
Abstract
Classic security methods become less effective against the Internet of Things (IoT) cyber-attacks, such as cryptography. An urgent need for real-time and lightweight detection of cyber-attacks is needed to secure IoT networks. This demand is achieved by a reliable and efficient intrusion detection system (IDS) that can meet IoT environments' high scalability and dynamicity.
Herein, we analyzed the traffic and features of commonly used and recently published datasets for IoT networks. Furthermore, we proposed an ensemble feature selection method. Also, we studied the effects of traffic heterogeneity levels and time-window size on several classification methods to justify the detection model selection. Regarding the BotNet-IoT dataset, we noticed that few features play a critical role in IDS performance, and larger time-windows were slightly better than the shorter time-windows. Furthermore, we found that PCA classifier performance was significantly affected by traffic heterogeneity. On the other hand, the Boosted Tree showed the best and the most stable performance among all the considered classification methods.








Similar content being viewed by others
References
Alfandi, O., Khanji, S., Ahmad, L., Khattak, A.: A survey on boosting IoT security and privacy through blockchain. Clust. Comput. (2020). https://doi.org/10.1007/s10586-020-03137-8
Mirsky, Y., Doitshman, T., Elovici, Y., Shabtai, A.: Kitsune: an ensemble of autoencoders for online network intrusion detection. ArXiv180209089 Cs, 2018. Available: http://arxiv.org/abs/1802.09089 (accessed 24 Oct 2019)
Li, D., Cai, Z., Deng, L., Yao, X., Wang, H.H.: Information security model of block chain based on intrusion sensing in the IoT environment. Clust. Comput. 22(1), 451–468 (2019). https://doi.org/10.1007/s10586-018-2516-1
Mahdavi Hezavehi, S., Rahmani, R.: An anomaly-based framework for mitigating effects of DDoS attacks using a third party auditor in cloud computing environments. Clust. Comput. 23(4), 2609–2627 (2020). https://doi.org/10.1007/s10586-019-03031-y
Mohamed, T. Otsuka, T., Ito, T.: Towards machine learning based IoT intrusion detection service. In: Recent Trends Future Technol. Appl. Intell. IEAAIE 2018 Lect. Notes Comput. Sci., vol. 10868 (2018). https://doi.org/10.1007/978-3-319-92058-0_56
Shameli-Sendi, A., Cheriet, M., Hamou-Lhaj, A.: Taxonomy of intrusion risk assessment and response system | Elsevier Enhanced Reader. Comput. Secur. 45, 1–16 (2014). https://doi.org/10.1016/j.cose.2014.04.009
Alsmadi, I., Burdwell, R., Aleroud, A., Wahbeh, A., Qudah, M., Al-Omari, A.: Practical Information Security: A Competency-Based Education Course. Springer, New York (2018)
Moustafa, N., Hu, J., Slay, J.: A holistic review of Network Anomaly Detection Systems: a comprehensive survey | Elsevier Enhanced Reader. J. Netw. Comput. Appl. 128, 33–55 (2019). https://doi.org/10.1016/j.jnca.2018.12.006
Guo, A., Xu, M., Ran, F., Wang, H.: A novel medical internet of things perception system based on visual image encryption and intrusion detection. Clust. Comput. 22(6), 13405–13413 (2019). https://doi.org/10.1007/s10586-018-1944-2
Kim, D.-Y., Kim, S., Hassan, H., Park, J.H.: Radio resource management for data transmission in low power wide area networks integrated with large scale cyber physical systems. Clust. Comput. 20(2), 1831–1842 (2017). https://doi.org/10.1007/s10586-017-0841-4
Deng, L., Li, D., Yao, X., Cox, D., Wang, H.: Mobile network intrusion detection for IoT system based on transfer learning algorithm. Clust. Comput. 22(4), 9889–9904 (2019). https://doi.org/10.1007/s10586-018-1847-2
Tama, B.A., Comuzzi, M., Rhee, K.-H.: TSE-IDS: A two-stage classifier ensemble for intelligent anomaly-based intrusion detection system. IEEE Access 7, 94497–94507 (2019). https://doi.org/10.1109/ACCESS.2019.2928048
Okoli, C., Schabram, K.: A guide to conducting a systematic literature review of information systems research. SSRN Electron. J. (2010). https://doi.org/10.2139/ssrn.1954824
Moustafa, N., Turnbull, B., Choo, K.-K.R.: An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of Internet of Things. IEEE Internet Things J. 6(3), 4815–4830 (2019). https://doi.org/10.1109/JIOT.2018.2871719
Pham, N.T., Foo, E., Suriadi, S., Jeffrey, H., Lahza, H.F.M.: Improving performance of intrusion detection system using ensemble methods and feature selection. In: Proceedings of the Australasian Computer Science Week Multiconference on—ACSW '18, Brisband, Queensland, Australia, 2018, pp. 1–6. https://doi.org/10.1145/3167918.3167951
Kang, S.-H., Kim, K.J.: A feature selection approach to find optimal feature subsets for the network intrusion detection system. Clust. Comput. 19(1), 325–333 (2016). https://doi.org/10.1007/s10586-015-0527-8
Radford, B.J., Richardson, B.D., Davis, S.E.: Sequence aggregation rules for anomaly detection in computer network traffic. ArXiv Prepr. ArXiv180503735, p. 13, 2018.
"NSL-KDD | Datasets | Research | Canadian Institute for Cybersecurity | UNB." https://www.unb.ca/cic/datasets/nsl.html (accessed Nov. 20, 2019)
Meidan, Y., et al.: N-BaIoT—network-based detection of iot botnet attacks using deep autoencoders. IEEE Pervasive Comput. 17(3), 12–22 (2018). https://doi.org/10.1109/MPRV.2018.03367731
Al-Hawawreh, M., Moustafa, N., Sitnikova, E.: Identification of malicious activities in industrial internet of things based on deep learning models. J. Inf. Secur. Appl. 41, 1–11 (2018). https://doi.org/10.1016/j.jisa.2018.05.002
Moustafa, N., Slay, J.: UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In: 2015 Military Communications and Information Systems Conference (MilCIS), 2015, pp. 1–6, https://doi.org/10.1109/MilCIS.2015.7348942
Verma, A., Ranga, V.: ELNIDS: Ensemble Learning Based Network Intrusion Detection System for RPL based Internet of Things. In: Proceedings of the 2019 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), 2019, pp. 1–6. https://doi.org/10.1109/IoT-SIU.2019.8777504
Verma, A., Ranga, V.: RPL-NIDDS17—a data set for Intrusion Detection in RPL based 6LoWPAN Networks (Internet of Things). https://doi.org/10.5281/zenodo.1406034
Vimala, S., Khanaa, V., Nalini, C.: A study on supervised machine learning algorithm to improvise intrusion detection systems for mobile ad hoc networks. Clust. Comput. 22(2), 4065–4074 (2019). https://doi.org/10.1007/s10586-018-2686-x
Balamurugan, V., Saravanan, R.: Enhanced intrusion detection and prevention system on cloud environment using hybrid classification and OTS generation. Clust. Comput. 22(6), 13027–13039 (2019). https://doi.org/10.1007/s10586-017-1187-7
Mukherjee, S., Sharma, N.: Intrusion detection using Naive bayes classifier with feature reduction | Elsevier enhanced reader. Procedia Technol. 4, 119–128 (2012). https://doi.org/10.1016/j.protcy.2012.05.017
Han, J., Pei, J., Kamber, M.: Data Mining: Concepts and Techniques. Elsevier, New York (2011)
Aljawarneh, S., Yassein, M.B., Aljundi, M.: An enhanced J48 classification algorithm for the anomaly intrusion detection systems. Clust. Comput. 22(5), 10549–10565 (2019). https://doi.org/10.1007/s10586-017-1109-8
Miller, S.T., Busby-Earle, C.: Multi-perspective machine learning a classifier ensemble method for intrusion detection. In: Proceedings of the 2017 International Conference on Machine Learning and Soft Computing—ICMLSC '17, Ho Chi Minh City, Vietnam, 2017, pp. 7–12. https://doi.org/10.1145/3036290.3036303
Gao, L., Li, F., Xu, X., Liu, Y.: Intrusion detection system using SOEKS and deep learning for in-vehicle security. Clust. Comput. 22(6), 14721–14729 (2019). https://doi.org/10.1007/s10586-018-2385-7
UCI Machine Learning Repository: detection_of_IoT_botnet_attacks_N_BaIoT Data Set. https://archive.ics.uci.edu/ml/datasets/detection_of_IoT_botnet_attacks_N_BaIoT (accessed 27 Nov 2019)
Siddiqui, A.J., Boukerche, A.: TempoCode-IoT: temporal codebook-based encoding of flow features for intrusion detection in Internet of Things. Clust. Comput. (2020). https://doi.org/10.1007/s10586-020-03153-8
Tavallaee, M., Bagheri, E., Lu, W., Ghorbani, A.A.: A detailed analysis of the KDD CUP 99 data set. In: 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, 2009, pp. 1–6. https://doi.org/10.1109/CISDA.2009.5356528
García, S., Zunino, A., Campo, M.: Survey on network-based botnet detection methods. Secur. Commun. Netw. 7(5), 878–903 (2014). https://doi.org/10.1002/sec.800
Aldwairi, M., Mardini, W., Alhowaide, A.: Anomaly payload signature generation system based on efficient tokenization methodology. In: Int. J. Commun. Antenna Propag. IRECAP 2018, 2018.
Figures/PerformanceMeasuresFigures.pdf master Alaa Alhowaide / Towards the Design of Real-Time Autonomous IoT NIDS. GitLab. https://gitlab.com/azalhowaide/towards-the-design-of-real-time-autonomous-iot-nids/-/blob/master/Figures/PerformanceMeasuresFigures.pdf (accessed 3 Mar 2020)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Alhowaide, A., Alsmadi, I. & Tang, J. Towards the design of real-time autonomous IoT NIDS. Cluster Comput 26, 2489–2502 (2023). https://doi.org/10.1007/s10586-021-03231-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03231-5