Abstract
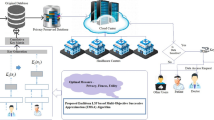
Cloud computing serves as a major boost for the digital era since it handles data from a large number of users simultaneously. Besides the several useful characteristics, providing security to the data stored in the cloud platform is a major challenge for the service providers. Privacy preservation schemes introduced in the literature trying to enhance the privacy and utility of the data structures by modifying the database with the secret key. In this paper, an optimization scheme, Brain Storm based Whale Optimization Algorithm (BS-WOA), is introduced for identifying the secret key. The database from the data owner is modified with the optimal secret key for constructing the retrievable perturbation data for preserving the privacy and utility. The proposed BS-WOA is designed through the hybridization of Brain Storm Optimization and Whale Optimization Algorithm. Simulation of the proposed technique with the BS-WOA is done in the three standard databases, such as chess T10I4D100 K, and the retail databases. When evaluated for the key size of 256, the proposed BS-WOA achieved privacy value of 0.186 and utility value of 0.8777 for the chess database, and thus, has improved performance.




Similar content being viewed by others
References
Lee, J., Ko, H.J., Lee, E., Choi, W., Kim, U.M.: A data sanitization method for privacy preserving data re-publication. In: Proceedings of IEEE Fourth International Conference on Networked Computing and Advanced Information Management, pp. 28–31 (2008)
Pan, Y., Xiaolin, G., Jian, A., Jing, Y., Jiancai, L., Feng, T.: A retrievable data perturbation method used in privacy-preserving in cloud computing. China Commun. 11(8), 73–84 (2014)
Kao, Y.H., Lee, W.B., Hsu, T.Y., Lin, C.Y.: Data perturbation method based on contrast mapping for reversible privacy-preserving data mining. J. Med. Biol. Eng. 35(6), 789–794 (2015)
Chinnasamy, A., Sivakumar, B., Selvakumari, P., Suresh, A.: Minimum connected dominating set based RSU allocation for smartCloud vehicles in VANET. Clust. Comput. (2018). https://doi.org/10.1007/s10586-018-1760-8
Huang, Q.L., YANG, Y.X., Fu, J.Y., Niu, X.X.: Secure and privacy-preserving DRM scheme using homomorphic encryption in cloud computing. J. China Univ. Posts Telecommun. 20(6), 88–95 (2013)
Cheng, Y., Wang, Z.Y., Ma, J., Wu, J.J., Mei, S.Z., Ren, J.C.: Efficient revocation in ciphertext-policy attribute-based encryption based cryptographic cloud storage. J. Zhejiang Univ. Sci. C 14(2), 85–97 (2013)
Yang, K., Zhang, K., Jia, X., Hasan, M.A., Shen, X.S.: Privacy-preserving attribute-keyword based data publish-subscribe service on cloud platforms. Inf. Sci. 387, 116–131 (2017)
Allard, T., Nguyen, B., Pucheral, P.: METAP: revisiting privacy-preserving data publishing using secure devices. Distrib. Parallel Databases 32(2), 191–244 (2014)
Jaina, I., Jain, V.K., Jain, R.: Correlation feature selection based improved-Binary Particle Swarm Optimization for gene selection and cancer classification. Appl. Soft Comput. 62, 203–215 (2018)
Sabin Begum, R., Sugumar, R.: Novel entropy-based approach for cost-effective privacy preservation of intermediate datasets in cloud. Clust. Comput. (2017). https://doi.org/10.1007/s10586-017-1238-0
Komninos, N., Junejo, A.K.: Privacy preserving attribute-based encryption for multiple cloud collaborative environment. In Proceedings of IEEE/ACM 8th International Conference on Utility and Cloud Computing, pp. 595–600 (2015)
Fahad, A., Tari, Z., Almalawi, A., Goscinski, A.: PPFSCADA: privacy preserving framework for SCADA data publishing. Future Gener. Comput. Syst. 37, 496–511 (2014)
Wang, H.: Privacy-preserving data sharing in cloud computing. J. Comput. Sci. Technol. 25(3), 401–414 (2010)
Hong, M.Q., Zhao, W.B., Wang, P.Y.: Homomorphic encryption scheme based on elliptic curve cryptography for privacy protection of cloud computing. In: Proceedings of IEEE International Conference on Intelligent Data and Security (IDS), pp. 152–157 (2016)
Curtmola, R., Garay, J.A., Kamara, S., Ostrovsky, R.: Searchable symmetric encryption: improved definitions and efficient constructions. In: Proceeding of the 13th ACM Conference on Computer and Communications Security (CCS ‘06), pp. 79–88 (2006)
Jiang, X., Yu, J., Kong, F., Cheng, X., Hao, R.: A novel privacy preserving keyword search scheme over encrypted cloud data. In: Proceedings of IEEE 10th International Conference on P2P, Parallel, Grid, Cloud, and Internet Computing, pp. 836–839 (2015)
Palanisamy, B., Liu, L.: Privacy-preserving data publishing in the cloud: a multi-level utility-controlled approach. In: Proceedings of IEEE 8th International Conference on Cloud Computing, pp. 130–137 (2015)
Sweeney, L.: k-anonymity: a model for protecting privacy. Int. J. Uncertain. Fuzziness Knowledge-Based Syst. 10(2), 557–570 (2002)
Cao, Z., Rong, X., Du, Z.: An improved brain storm optimization with dynamic clustering strategy. MATEC Web Conf. 95, 19002 (2017). https://doi.org/10.1051/matecconf/20179519002
Song, W., Wang, B., Wang, Q., Peng, Z., Lou, W., Cui, Y.: A privacy-preserved full-text retrieval algorithm over encrypted data for cloud storage applications. J. Parallel Distrib. Comput. 99, 14–27 (2016)
Mafarja, M., Mirjalili, S.: Whale optimization approaches for wrapper feature selection. Appl. Soft Comput. 62, 441–453 (2017)
Cao, N., Wang, C., Li, M., Ren, K., Lou, W.: Privacy-preserving multi-keyword ranked search over encrypted cloud Data. IEEE Trans. Parallel Distrib. Syst. 25(1), 222–233 (2014)
Langville, A.N., Stewart, W.J.: The Kronecker product and stochastic automata networks. J. Comput. Appl. Math. 167, 429–447 (2004)
Liu, S., Li, T.: A new hypernetwork model based on matrix operation. In: 2015 10th International Conference on Intelligent Systems and Knowledge Engineering (ISKE), Taipeipp. pp. 176–182 (2015)
Frequent Itemset Mining Dataset Repository. http://fimi.ua.ac.be/data/. Accessed Nov 2017
Wu, Z., Xu, G., Lu, C., Chen, E., Jiang, F., Li, G.: An effective approach for the protection of privacy text data in the CloudDB. World Wide Web (2017). https://doi.org/10.1007/s11280-017-0491-8
Suresh, A., Varatharajan, R.: Competent resource provisioning and distribution techniques for cloud computing environment. Clust. Comput. (2017). https://doi.org/10.1007/s10586-017-1293-6
Qiu, M., Ming, Z., Li, J., Gai, K., Zong, Z.: Phase-change memory optimization for green cloud with genetic algorithm. IEEE Trans. Comput. 64(12), 3528–3540 (2015)
Mirjalili, S., Lewis, A.: The whale optimization algorithm. Adv. Eng. Softw. 95, 51–67 (2016)
Shi, Y., Brain storm optimization algorithm. In: International Conference on Swarm Intelligence, pp. 303–309. Springer, Berlin (2011)
Mafarja, M.M., Mirjalili, S.: Hybrid Whale Optimization Algorithm with simulated annealing for feature selection. Neurocomputing 260, 302–312 (2017)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Thanga Revathi, S., Ramaraj, N. & Chithra, S. Brain storm-based Whale Optimization Algorithm for privacy-protected data publishing in cloud computing. Cluster Comput 22 (Suppl 2), 3521–3530 (2019). https://doi.org/10.1007/s10586-018-2200-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-018-2200-5