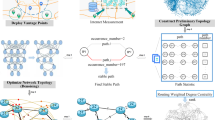
Abstract
The primary goal in a remote system is to have a beyond any doubt information conveyance from the begin to end. One reason for information conveyance disappointments as often as possible happening in remote applications is hub developments. One answer for this issue is to recreate the course so that the impacts of topology change are decreasing. Then again, a few assets are required to finish this errand. In this paper, we make the consistency in hub versatility designs and guarantee that correspondence of information between the hubs is adequate. The positions of the switches are planned, and tree topology grew so that all hubs activities coordinate with the foundation of the tree. Initially send the hubs in a system then ascertain the most extreme in degree every hub. The facilitator hub is unified with most extreme in-degree lastly develop the tree to send the information to the destination. On the off chance that in-degree hub numbers are the same in any two hubs the best hub is picked in light of a background marked by the two hubs. On the off chance that the limit of both the hubs is same and hub reliability is ascertained utilizing the proposal framework and a most dependable hub is picked as the facilitator hub. This procedure diminishes the clog in the system furthermore the loss of information parcels in the system.













Similar content being viewed by others
Change history
05 December 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s10586-022-03885-9
References
Baek, J., Vu, Q.H., Liu, J.K., Huang, X., Xiang, Y.: A secure cloud computing based framework for big data information management of smart grid. IEEE Trans. Cloud Comput. 3(2), 233–244 (2015)
Chang, J., Hsiu, P., Kuo, T.: Search-oriented deployment strategies for wireless sensor networks. In: 10th IEEE International Symposium on Object and Component-Oriented Real-Time Distributed Computing (ISORC), pp. 164–171 (2007)
Chen, L., Sun, T., Liang, N.: An evaluation study of mobility support in zigbee networks. J. Signal Process. Syst 59(1), 111–122 (2010)
Barsoum, A.F., Hasan, M.A.: Provable multicopy dynamic data possession in cloud computing systems. In: IEEE Transactions on Information Forensics and Security, vol. 10, No. 3 (2015)
Tao, F., Li, C., Liao, T.W., Laili, Y.: BGM-BLA: a new algorithm for dynamic migration of virtual machines in cloud computing. In: IEEE Transactions on Services Computing, vol. 9, No. 6 (2016)
Jin, A.L., Song, W., Wang, P., Niyato, D., Ju, P.: Auction mechanisms toward efficient resource sharing for cloudlets in mobile cloud computing. IEEE Trans. Serv. Comput. 9(6), 895–909 (2016)
Li, J., Tan, X., Wong, D.S., Xhafa, F.: OPoR: enabling proof of retrievability in cloud computing with resource-constrained devices. IEEE Trans. Cloud Comput. 3(2), 195–205 (2015)
Vijayaraj, A., Sudharshana, U.: Construction of routing tree and node discovery in wireless networks. In: International Conference on Communication and Signal Processing(ICCSP) in IEEE, pp. 1519–1523, 2014
Chumkamon, S., Tuvaphanthaphiphat, P., Keeratiwintakorn, P.: The vertical handoff between GSM and Zigbee networks for vehicular communication. In: 2010 International Conference on Electrical Engineering/Electronics Computer Telecommunications and Information Technology (ECTI-CON), pp. 603–606 (2010)
Kashiki, K.: Cognitive Radio Lab., KDDI R&D Lab., Fujimino, Japan Yamaguchi, A.: Experimental and analytical study regarding transmission quality of Wireless LAN system—for implementation of heterogeneous wireless network. In: Personal Indoor and Mobile Radio Communications (PIMRC) in IEEE 22nd International Symposium, pp. 685–689, 2011
Djemame, K., Armstrong, D., Guitart, J., Macias, M.: A risk assessment framework for cloud computing. IEEE Trans. Cloud Comput. 4(3), 265–278 (2016)
Djemame, K., Gourlay, I., Padgett, J., Voss, K., Kao, O.: Risk management in grids. In: Buyya, R., Bubendorfer, K. (eds.) Market-Oriented Grid and Utility Computing. Wiley, Hoboken (2009)
Zhang, X., Wuwong, N., Li, H., Zhang, X.: Information security risk management framework for the cloud computing environments. In: 2010 IEEE 10th International Conference on Computer and Information Technology (CIT), pp. 1328–1334 (2010)
Fit_o, J.O., Guitart, J.: Business-driven management of infrastructure- level risks in cloud providers. Future Gener. Comput. Syst. 32, 41–53 (2014)
Saripalli, P., Walters, B.: QUIRC: A quantitative impact and risk assessment framework for cloud security. In: 2010 IEEE 3rd International Conference on Cloud Computing (CLOUD), pp. 280–288 (2010)
Djemame, K., Padgett, J., Gourlay, I., Armstrong, D.: Brokering of risk-aware service level agreements in grids. Concurr. Comput. 23(7), 1558–1582 (2011)
Chung, W., Hsiu, P., Shih, Y., Pang, A., Hung, K.: Mobility aware node deployment and tree construction in ZigBee wireless networks. In: IEEE International Conference on Communications, pp. 1–6 (2013)
Chung, W., Hsiu,P., Shih, Y., Pang, A., Huang, Y., Hung, K.: Mobility robust tree construction in ZigBee wireless networks. In: IEEE International Conference on Communications (ICC), pp. 1–6 (2011)
Willing, A., Matheus, K., Wolisz, A.: Wireless technology in industrial networks. Proc. IEEE 93(6), 1130–1151 (2010)
Mitzenmacher, M.: On the analysis of randomized load balancing schemes. In: ACM Symposium on Parallel Algorithms and Architectures (SPAA) (1997)
Mitzenmacher, M. et al.: Load balancing with memory. In: 43rd Annual IEEE Symposium on Foundations of Computer Science (FOCS), (2002)
Nath, S., Gibbons, P.B., Seshan, S., Anderson, Z.R.: Synopsis diffusion for robust aggregation in sensor networks. In: Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys), pp. 250–262. ACM (2004)
Tsai, J.L., Lo, N.W.: A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst. J. 9(3), 805–815 (2015)
Lee, J.S., Su, Y.W., Shen,C.C.: A comparative study of wireless protocols: Bluetooth, UWB, ZigBee, and Wi-Fi. In: Industrial Electronics Society, 2007. IECON 2007. 33rd Annual Conference of the IEEE, pp. 46–51. IEEE, 2007
Shen, H., Xu, C.: Locality-aware and churn-resilient load-balancing algorithms in structured peer-to-peer networks. IEEE Trans. Parallel Distrib. Syst. 18(6), 849–862 (2007)
Manku, G.: Balanced binary trees for ID management and load balance in distributed hash tables. In: Proceedings of the 23rd Annual ACM Symposium on Principles of Distributed Computing, pp. 197–205. ACM, 2004
Xue, K., Hong, P.: A dynamic secure group sharing framework in public cloud computing. IEEE Trans. Cloud Comput. 2(4), 459–470 (2014)
Xiong, J., Liu, X., Yao, Z., Ma, J., Li, Q., Geng, K.: A secure data self-destructing scheme in cloud computing. IEEE Trans. Cloud Comput 2(4), 448–458 (2014)
Al-Abdallah, A., Al-Emadi, A., Al-Ansari, M., Mohandes, N., Malluhi, Q.: Real-time traffic surveillance using ZigBee. In: 2010 International Conference on Computer Design and Applications (ICCDA), vol. 1, pp. 550–554 (2010)
Zhang, F., Cao, J., Hwang, K.: Adaptive workflow scheduling on cloud computing platforms with iterative ordinal optimization. In: IEEE Transactions on Cloud Computing, vol. 3, No. 2 (2015)
Khanafer, M., Guennoun, M., Mouftah, H.: WSN architectures for intelligent transportation systems. In: 2009 3rd International Conference on New Technologies, Mobility and Security (NTMS), pp. 1–8 (2009)
Author information
Authors and Affiliations
Corresponding author
Additional information
This article has been retracted. Please see the retraction notice for more detail:https://doi.org/10.1007/s10586-022-03885-9
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Vijayaraj, A., Suresh, R.M. & Poonkuzhali, S. RETRACTED ARTICLE: Node discovery with development of routing tree in wireless networks. Cluster Comput 22 (Suppl 5), 10861–10871 (2019). https://doi.org/10.1007/s10586-017-1211-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-017-1211-y