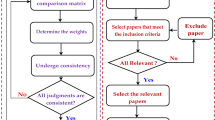
Abstract
Literature on business process compliance (BPC) has predominantly focused on the alignment of the regulatory rules with the design, verification and validation of business processes. Previously, surveys on BPC have been conducted with specific context in mind; however, the literature on BPC management research is largely sparse and does not accumulate a detailed understanding on existing literature and related issues faced by the domain. This survey provides a holistic view of the literature on existing BPC management approaches and categorises them based on different compliance management strategies in the context of formulated research questions. A systematic literature approach is used where search terms pertaining keywords were used to identify literature related to the research questions from scholarly databases. From initially 183 papers, we selected 79 papers related to the themes of this survey published between 2000 and 2015. The survey results reveal that mostly compliance management approaches centre around three distinct categories, namely design-time (\(28\%\)), run-time (\(32\%\)) and auditing (\(10\%\)). Also, organisational and internal control-based compliance management frameworks (\(21\%\)) and hybrid approaches make (\(9\%\)) of the surveyed approaches. Furthermore, open research challenges and gaps are identified and discussed with respect to the compliance problem.




Similar content being viewed by others
Notes
SpringerLink http://www.springerlink.com.
ScienceDirect http://www.sciencedirect.com/.
ACM Digital Library http://dl.acm.org.
Web of Science http://www.webofscience.com/.
EbscoHost https://www.ebscohost.com/.
IEEEXplore http://ieeexplore.ieee.org/.
Free Search Database DBLP http://dblp.uni-trier.de/.
It might be possible that there are papers on compliance management written in other languages such as German and French, and we exclude such papers from this survey, see Sect. 9.3.
There are other sources of citation measurements and academic search engines, e.g. Microsoft Academic Search, Scopus, Semantic Scholars, see Wouters and Costas [195] for detailed listing.
This is not an exhaustive list of all represented frameworks in their respective category.
OCEG: Open Compliance Ethics Group, available at: http://www.oceg.org/ (retrieved: 8 May 2017).
Semantic Constraints in Process Management Systems, available at: https://www.uni-ulm.de/in/iui-dbis/forschung/abgeschlossene-projekte/seaflows/ (retrieved: 8 May, 2017).
Web Ontology Language http://www.w3.org/TR/owl-features/.
Semantics Web Rule Language https://www.w3.org/Submission/SWRL/.
The Hazard Analysis Critical Control Point System, available at: http://www.standards.org/standards/listing/haccp (retrieved: 8 May 2017).
Regorous Compliance Checker: https://www.regorous.com/ (retrieved: 10 Oct 2013).
PROPOLS is an ontology-based property specification language based on PPS to specify service composition properties.
Internal control, an integrated framework: the committee of sponsoring organisations of the treadway commission [39].
SPIN model checker, available at: http://spinroot.com/spin/whatispin.html.
NuSMV: symbolic model verification, available at: http://nusmv.fbk.eu/.
UPAAL: Uppsala—Aalborg model checker, available at:http://www.uppaal.org/.
The W3C standard: http://www.w3.org/standards/.
Unified modelling language: http://www.omg.org/spec/UML/.
Object constraint language: http://www.omg.org/spec/OCL/.
process mining: http://www.processmining.org.
Eudralex, available at: http://ec.europa.eu/health/documents/eudralex/index_en.htm (retrieved: 25th October 2012).
Colombo Tosatto and colleagues [36] formally proved that checking whether a business process is partially compliant is an NP-complete, and the complexity of checking whether a business process is either fully compliant or not compliant is coNP-complete problem.
References
Abdullah NS, Sadiq S, Indulska M (2010) Emerging challenges in information systems research for regulatory compliance management. In: Proceedings of CAiSE’10. Springer, pp 251–265
Achimugu P, Selamat A, Ibrahim R, Mahrin MN (2014) A systematic literature review of software requirements prioritization research. Inf Softw Technol 56(6):568–585
Ågotnes T, van der Hoek W, Rodríguez-Aguilar JA, Sierra C, Wooldridge M (2007) On the Logic of Normative Systems. In: Proceedings of the 20th international joint conference on artificial intelligence. AAAI Press, Menlo Park, pp 1175–1180
Ågotnes T, Van der Hoek W, Wooldridge M (2010) Robust normative systems and a logic of norm compliance. J Log 18(1):4–30
Agrawal R, Bayardo R, Faloutsos C, Kiernan J, Rantzau R, Srikant R (2004) Auditing compliance with a hippocratic database. In: Proceedings of the thirtieth international conference on very large data bases, vol 30, VLDB Endowment, VLDB ’04, pp 516–527
Agrawal R, Johnson C, Kiernan J, Leymann F (2006) Taming compliance with Sarbanes–Oxley internal controls using database technology. In: Proceedings of the 22nd international IEEE conference on data engineering, p 92
Ahmed A, Sakr S (2010) Querying graph-based repositories of business process models. In: DASFAA workshops, pp 33–44
Alberti M, Chesani F, Gavanelli M, Lamma E, Mello P, Montali M, Torroni P (2007) Expressing and verifying business contracts with abductive. In: Boella G, van der Torre L, Verhagen H (eds) Normative multi-agent systems, Internationales Begegnungs- und Forschungszentrum für Informatik (IBFI), Schloss Dagstuhl, Germany, Dagstuhl, Germany, No. 07122 in Dagstuhl seminar proceedings
Antón AI, Bertino E, Li N, Yu T (2007) A roadmap for comprehensive online privacy policy management. Commun ACM 50(7):109–116
Arbab F, Kokash N, Meng S (2008) Towards using REO for compliance-aware business process modeling. In: Margaria T, Steffen B (eds) ISoLA’08, vol 17. Springer, Berlin, pp 108–123
Arya A, van Dongen B, van der Aalst W (2010) Towards robust conformance checking. In: BPM workshops’10, pp 122–133
Ashby S (2008) Operational risk: lessons from non-financial organisations. J Risk Manag Financ Inst 1:406–415
Awad A (2010) A compliance management framework for business process models. Ph.D. thesis, Hasso Plattner Institut, Potsdam University, Germany
Awad A, Weske M (2009) Visualisation of compliance violations in business process models. In: 5th Workshop on business process intelligence, vol 9, pp 182–193
Awad A, Decker G, Weske M (2008) Efficient compliance checking using BPMN-Q and temporal logic. In: Proceedings of the 6th international conference on business process management (BPM 2008). Springer, Milano, pp 326–341
Awad A, Smirnov S, Weske M (2009) Towards resolving compliance violations in business process models. In: Sadiq S, Indulska M, zur Muehlen M, Dubois E, Johannesson P (eds) Proceedings of the 2nd international workshop on governance risk and compliance GRCIS, pp 18–33
Awad A, Weidlich M, Weske M (2009) Specification, verification and explanation of violation for data aware compliance rules. In: Baresi L, Chi CH, Suzuki J (eds) Proceedings of the 7th international joint conference on service-oriented computing (ICSOC-Service Wave 2009). Springer, Stockholm, pp 500–515
Bai X, Liu Y, Wang L, Tsai WT, Zhong P (2009) Model-based monitoring and policy enforcement of services. In: Proceedings of the 2009 world conference on services, vol I, pp 789 –796
Barnawi A, Awad A, Elgammal A, Elshawi R, Almalaise A, Sakr S (2016) An anti-pattern-based runtime business process compliance monitoring framework. Int J Adv Comput Sci Appl (IJACSA) 7(2):551–572
Bartolini R, Lenci A, Montemagni S, Pirrelli V, Soria C (2004) Semantic mark-up of Italian legal texts through NLP-based techniques. In: Proceedings of the fourth international conference on language resources and evaluation (LREC 2004), Lisbon, Portugal
BCBS (2013) Basel III: The liquidity coverage ratio and liquidity risk monitoring tools. http://www.bis.org/publ/bcbs238.pdf
Beach T, Rezgui Y, Li H, Kasim T (2015) A rule-based semantic approach for automated regulatory compliance in the construction sector. Expert Syst Appl 42(12):5219–5231
Becker J, Delfmann P, Eggert M, Schwittay S (2012) Generalizability and applicability of model-based business process compliance-checking approaches–a state-of-the-art analysis and research roadmap. BuR Bus Res J 5(2):221–247
Bench-Capon T, Gordon TF (2009) Isomorphism and argumentation. In: Proceedings of the 12th international conference on artificial intelligence and law, ACM, NY, USA. ICAIL’09, pp 11–20
Bench-Capon TJM, Coenen FP (1992) Isomorphism and legal knowledge based systems. Artif Intell Law 1(1):65–86
Bérard B, Bidoit M, Finkel A, Laroussinie F, Petit A, Petrucci L, Schnoebelen P (2001) System and software verification–model checking techniques and tools. Springer, Berlin
Bernstein S, Falcione A (2015) Moving beyond the baseline Leveraging the compliance function to gain a competitive edge: state of compliance survey 2015. Survey report, Pricewaterhousecoopers
Bhattacharya K, Gerede C, Hull R, Liu R, Su J (2007) Towards formal analysis of artifact-centric business process models. In: Alonso G, Dadam P, Rosemann M (eds) Proceedings of the 5th international conference on business process management (BPM 2007). Springer, Berlin, pp 288–304
Biagioli C, Francesconi E, Passerini A, Montemagni S, Soria C (2005) Automatic semantics extraction in law documents. In: Proceedings of the 10th international conference on artificial intelligence and law, ACM, New York, NY, USA, ICAIL’05, pp 133–140
Birukou A, D’Andrea V, Leymann F, Serafinski J, Silveira P, Strauch S, Tluczek M (2010) An integrated solution for runtime compliance Governance in SOA. In: Proceeding of international conference on service-oriented computing (ICSOC), pp 122–136
Bonatti PA, Shahmehri N, Duma C, Olmedilla D, Nejdl W, Baldoni M, Baroglio C, Martelli A, Coraggio P, Antoniou G, Peer J, Fuchs NE (2004) Rule-based policy specification: state of the art and future work. Rewerse project report-i2-d1, Universitá di Napoli Fedrecio II
Bonazzi R, Pigneur Y (2009) Compliance management in multi-actor contexts. In: Proceedings of international workshop on governance, risk and compliance (GRCIS), An ancillary meeting of CAISE
Brighi R, Palmirani M (2009) Legal text analysis of the modification provisions: a pattern oriented approach. In: Proceedings of the 12th international conference on artificial intelligence and law (ICAIL’09), ACM, New York, NY, USA, pp 238–239
Cabanillas C, Resinas M, Ruiz-Cortés A (2010) On the identification of data-related compliance problems in business processes. In: Jornadas Científico-Técnicas En Servicios Web Y SOA (JSWEB’10), Valencia, España, vol 1, pp 89–102
COBIT (2007) Control objectives for information related technology—COBIT 4.1. http://www.isaca.org/Knowledge-Center/cobit/Pages/Downloads.aspx
Colombo Tosatto S, Governatori G, Kelsen P (2015) Business process regulatory compliance is hard. IEEE Trans Serv Comput 8(6):958–970
COMPAS-Project (2008) D2.1 state-of-the-art in the field of compliance languages—compliance-driven models, languages, and architectures for services. Deliverable D2.1v1.0, Tilburg University, The Netherlands
Cooper HM (1988) Organizing knowledge syntheses: a taxonomy of literature reviews. Knowl Soc 1(1):104–126
COSO (1994) Internal control–integrated framework. http://www.coso.org/
Cunningham H, Maynard D, Tablan V, Ursu C, Bontcheva K (2001) Developing language processing components with GATE: a user guide. https://gate.ac.uk/sale/tao/tao.pdf
d Araujo DA, Rigo SJ, Muller C, Chishman R (2013) Automatic information extraction from texts with inference and linguistic knowledge acquisition rules. In: 2013 IEEE/WIC/ACM international joint conferences on web intelligence (WI) and intelligent agent technologies (IAT), vol 3, pp 151–154
D’Aprile D, Giordano L, Gliozzi V, Martelli A, Pozzato G, Theseider Dupré D (2010) Verifying business process compliance by reasoning about actions. In: Dix J, Leite Ja, Governatori G, Jamroga W (eds) Proceeding of the 11th international workshop on computational logic in multi-agent systems (CLIMA XI). Springer, Berlin, pp 99–116
de Maat E, Winkels R (2010) Suggesting model fragments for sentences in Dutch Laws. In: Proceedings of legal ontologies and artificial intelligence techniques, pp 19–28
de Moura Araujo B, Schmitz EA, Correa AL, Alencar AJ (2010) A method for validating the compliance of business processes to business rules. In: Proceedings of SAC’10, ACM, pp 145–149
Doganata Y, Curbera F (2009) Effect of using automated auditing tools on detecting compliance failures in unmanaged processes. In: Proceedings of the 7th international conference on business process management (BPM 2009), Ulm, Germany, pp 310–326
El Kharbili M (2012) Business process regulatory compliance management solution frameworks: a comparative evaluation. In: Ghose A, Ferrarotti F (eds) Proceedings of the 8th Asia-Pacific Conference on Conceptual Modelling (APCCM 2012). ACS, Inc., Melbourne, Australia, pp 23–32
El Kharbili M, Stein S (2008) Policy-based semantic compliance checking for business process management. MobIS workshops, CEUR workshops 420:178–192
El Kharbili M, Stein S, Markovic I, Pulvermüller E (2008) Towards a framework for semantic business process compliance management. Banking 08(i):1–15
Elgammal A (2012) Towards a comprehensive framewcompliacbusiness process compliance. Ph.D. thesis, Tiburg Universtity
Elgammal A, Türetken O, van den Heuvel WJ, Papazoglou MP (2010) Root-cause analysis of design-time compliance violations on the basis of property patterns. In: Proceedings of the 8th international conference on service-oriented computing (ICSOC 2010), San Francisco, CA, USA, pp 17–31
Elgammal A, Turetken O, van den Heuvel WJ, Papazoglou M (2011) On the formal specification of regulatory compliance: a comparative analysis. In: Proceedings of ICSOC’10, pp 27–38
Elgammal A, Turetken O, van den Heuvel WJ, Papazoglou M (2016) Formalizing and applying compliance patterns for business process compliance. Softw Syst Model 15(1):119–146
Eshuis R (2006) Symbolic model checking of UML activity diagrams. ACM Trans Softw Eng Methodol 15(1):1–38
Evans GP (2014) Managing risk with an end-to-end process view: adopting a process-based approach to risk management. BPTrends article. https://www.bptrends.com/managing-risks-with-an-end-to-end-processview/
Fellmann M, Zasada A (2014) state-of-the-art of business process compliance approaches. In: Proceedings of European conference on information system (ECIS’14), Tel Aviv, Israel
Fongon P, Grillo K (2004) Corporate implications of Sarbanes–Oxley Act: a public policy. http://www.global-trade.law.com/ITRN711
Förster A, Engels G, Schattkowsky T (2005) Activity diagram patterns for modeling quality constraints in business processes. In: Proceedings of MoDELS’05, pp 2–16
Förster A, Engels G, Schattkowsky T, Straeten RVD (2006) A pattern-driven development process for quality standard-conforming business process models. Proceedings of VL/HCC 2006:135–142
Francesconi E (2010) legal rules learning based on a semantic model for legislation. In: Proceedings of SPLeT workshop
Ghanavati S, Amyot D, Peyton L (2007) Towards a framework for tracking legal compliance in healthcare. In: Proceedings of CAiSE’07, pp 218–232
Ghose A, Koliadis G (2007) Auditing business process compliance. In: Krämer B, Lin KJ, Narasimhan P (eds) Collection of ICSOC 2007. Springer, Berlin, pp 169–180
Giblin C, Liu AY, Müller S, Pfitzmann B, Zhou X (2005) Regulations expressed as logical models (REALM). In: Proceeding of JURIX 2005, IOS Press, pp 37–48
Gilliot M, Accorsi R (2009) Runtime predictions of policy violations in automated buisness processes. Extended abstract: presented at prime life/IFIP Summer School Program, Sept 7–11, Nice/France
Goedertier S, Vanthienen J (2006) Business rules for compliant business process models. In: Proceeding of BIS 2006, Gesellschaft für Informatik, pp 558–579
Goedertier S, Vanthienen J (2006) Designing compliant business processes with obligations and permissions. In: Eder J, Dustdar S (eds) Business process management workshops 2006. Springer, Berlin, pp 5–14
Goedertier S, Vanthienen J, Caron F (2015) Declarative business process modelling: principles and modelling languages. Enterp Inf Syst 9(9):161–185
Gogolla M, Bttner F, Richters M (2007) USE: a UML-based specification environment for validating UML and OCL. Sci Comput Program 69(1–3):27–34 (special issue on experimental software and toolkits)
Gómez-López M, Gasca R, Rinderle-Ma S (2013) Explaining the incorrect temporal events during business process monitoring by means of compliance rules and model-based diagnosis. In: Proceeding of EDOCW’13, pp 163–172
Gómez-López MT, Gasca RM, Pérez-Álvarez JM (2015) Compliance validation and diagnosis of business data constraints in business process at runtime. Inf Syst 48:26–43
Governatori G (2005) Representing business contracts in RuleML. Int J Coop Inf Syst 14(2–3):181–216
Governatori G, Hashmi M (2015) No time for compliance. In: Proceedings of EDOC15, Adelaide, Australia, pp 9–18
Governatori G, Milosevic Z (2005) Dealing with contract violations: formalism and domain specific language. In: Proceedings of EDOC 2005. IEEE Computer Society, pp 46–57
Governatori G, Rotolo A (2006) Logic of violations: a Gentzen system for reasoning with contrary-to-duty obligation. Aust J Log 4:193–215
Governatori G, Rotolo A (2008) An algorithm for business process compliance. In: Proceedings Jurix 2008. IOS Press, pp 186–191
Governatori G, Rotolo A (2010) A conceptually rich model of business process compliance. In: Proceedings of APCCM’10, vol 110, pp 3–12
Governatori G, Rotolo A (2010) Norm compliance in business process modeling. In: Proceedings of RuleML 2010. Springer, pp 194–209
Governatori G, Sadiq S (2009) The journey to business process compliance. In: Handbook of research on BPM, IGI Global, pp 426–454
Governatori G, Shek S (2013) Regorous: a business process compliance checker. In: Proceedings of ICAIL’13, ACM, Rome, pp 245–246
Governatori G, Milosevic Z, Sadiq S (2006) Compliance checking between business processes and business contracts. In: Proceeding of EDOC’06, pp 221–232
Han J, Jin Y, Li Z, Phan T, Yu J (2007) Guiding the service composition process with temporal business rules. In: Web Services 2007
Hashmi M (2015) A methodology for extracting legal norms from regulatory documents. In: Proceedings of EDOCW’15. IEEE Computer Society, pp 41–50
Hashmi M, Governatori G (2017) Norms modeling constructs of business process compliance management frameworks: a conceptual evaluation. Artif Intell Law. https://doi.org/10.1007/s10506-017-9215-8
Hashmi M, Governatori G, Wynn MT (2013) Normative requirements for business process compliance. In: Service research and innovation–third Australian symposium, ASSRI 2013, Sydney, NSW, Australia, Nov 27–29, 2013. Revised selected papers, pp 100–116. https://doi.org/10.1007/978-3-319-07950-9_8
Hashmi M, Governatori G, Wynn MT (2014) Modeling obligations with event-calculus. In: Proceedings of RuleML’14, Czech Republic, pp 296–310
Hashmi M, Governatori G, Wynn M (2015) Normative requirements for regulatory compliance: an abstract formal framework. Inf Syst Front 18(3):429–455
Hassan W, Logrippo L (2008) Requirements and compliance in legal systems: a logic approach. In: Proceedings of RELAW’08, Barcelona, Spain, pp 40–44
Herrestad H (1991) Norms and formalization. In: ICAIL’91, ACM, pp 175–184
Herther NK (2009) Research evaluation and citation analysis: key issues and implications. Electron Libr 27(3):361–375
Hinge K, Ghose A, Koliadis G (2009) Process SEER: a tool for semantic effect annotation of business process models. In: Proceedings of EDOC ’09, pp 54–63
HIPAA TUG (1996) The US Health Insurance Portability and Accountability Act of 1996
Hoffmann J, Weber I, Governatori G (2009) On compliance checking for clausal constraints in annotated process models. Inf Syst Front 14(2):155–177
IFRS (2014) IFRS 7 international financial reporting standards: financial instruments disclosures. http://www.ifrs.org/IFRSs/Pages/IFRS.aspx
Ingolfo S, Jureta I, Siena A, Perini A, Susi A (2014) Nómos 3: legal compliance of roles and requirements. In: Yu E, Dobbie G, Jarke M, Purao S (eds) Conceptual modeling, vol 8824. lecture notes in computer science. Springer, Berlin, pp 275–288
Jackson D (2006) Software abstractions: logic, language, and analysis. The MIT Press, Cambridge
James E, Jonathan S (2011) The benefits of static compliance testing for SCA next. In: Proceedings of the SDR’11, The Wireless Innovation Forum, Inc
Jiang J, Virginia D, Huib A, Frank D, Yao-Hua T (2013) Norm compliance checking. In: Proceedings of AAMAS’13, Saint Paul, USA, pp 1121–1122
Jiang J, Aldewereld H, Dignum V, Wang S, Baida Z (2014) Regulatory compliance of business processes. AI & Society, Heidelberg, pp 1–10
Johnson C, Grandison T (2007) Compliance with data protection laws using Hippocratic Database active enforcement and auditing. IBM Syst J 46(2):255–264
Johnson CM, Grandison TWA (2007) Compliance with data protection laws using Hippocratic Database active enforcement and auditing. IBM Syst J 46(2):255–264
Kabilan V, Johannesson P, Rugaimukamu D (2003) Business contract obligation monitoring through use of multi-tier contract ontology. In: Meersman R, Tari Z (eds) On The Move (OTM) workshops to meaningful internet systems. Springer, Berlin, pp 690–702
Kabilan V, Johannesson P, Rugaimukamu DM (2003) An ontological approach to unified contract management. In: Proceedings of 13th European Japanese conference on information modelling and knowlege bases, pp 106–110
Kähmer M, Gilliot M, Müller G (2008) Automating privacy compliance with ExPDT. In: Proceedings of the 10th IEEE conference on e-commerce technology and 5th conference on enterprise computing, pp 87–94
Karagiannis D, Mylopoulos J, Schwab M (2007) Business process-based regulation compliance: the case of the Sarbanes–Oxley Act. In: 15th IEEE international requirements engineering conference (RE 2007) pp 315–321
Kazmierczak P, Pedersen T, Ågotnes T (2012) NORMC: a norm compliance temporal logic model checker. STAIRS, frontiers in artificial intelligence and applications 241:168–179
Keller A, Ludwig K (2002) Defining and monitoring service-level agreements for dynamic e-business. In: Proceedings of the 16th USENIX conference on system administration, USENIX Association, Berkeley, USA, pp 189–204
Kharbili ME, Medeiros AKAD, Stein S, van der Aalst W (2008) Business process compliance checking: current state and future challenges. In: Modellierung Betrieblicher Informationssyteme, MobIS, pp 107–113
Kitchenham B (2004) Procedure for performing systematic reviews. Technical Report TR/SE-0401, Software Engineering Group, Department of Computer Science, Keele University, Keele, UK
Kitchenham B, Charters S (2007) Guidelines for performing systematic literature reviews in software engineering. Technical Report EBSE 2007-001, Keele University and Durham University Joint Report
Kiyavitskaya N, Zeni N, Breaux TD, Antón AI, Cordy JR, Mich L, Mylopoulos J (2008) Automating the extraction of rights and obligations for regulatory compliance. In: Li Q, Spaccapietra S, Yu E, Olivé A (eds) Proceedings of the 27th international conference on conceptual modeling (ER 2008). Springer, Berlin, pp 154–168
Knuplesch D, Ly L, Rinderle-Ma S, Pfeifer H, Dadam P (2010) On enabling data-aware compliance checking of business process models. In: Parsons J, Saeki M, Shoval P, Woo C, Wand Y (eds) Proceedings of the 29th international conference on conceptual modeling (ER 2010). Springer, Berlin, pp 332–346
Knuplesch D, Reichert M, Ly LT, Kumar A, Rinderle-Ma S (2013) Visual modeling of business process compliance rules with the support of multiple perspectives. In: Proceedings of the 32th international conference on conceptual modeling (ER 2013), Hong-Kong, pp 106–120
Knuplesch D, Reichert M, Kumar A (2015) Visually monitoring multiple perspectives of business process compliance. In: Proceedings of the 13th international conference on business process management (BPM 2015), Innsbruck, Austria, pp 263–279
Kowalski R, Sergot M (1989) A logic-based calculus of events. In: Schmidt J, Thanos C (eds) Foundations of knowledge base management, topics in information systems. Springer, Berlin, pp 23–55
KPMG (2013) A survey of fraud, bribery, and corruption in Australia and New Zealand. Survey series: issues and insights, KPMG Forensic. https://www.kpmg.com/AU/IssuesAndInsights/ArticlesPublications/Fraud-Survey/FDocuments/fraud-bribery-corruption-survey-2012v2.pdf
Küster JM, Ryndina K, Gall H (2007) Generation of business process models for object life cycle compliance. In: Proceedings of the 5th international conference on business process management (BPM 2007), Brisbane, Australia, pp 165–181
Lam HP, Governatori G (2009) The making of SPINdle. In: Governatori G, Hall J, Paschke A (eds) Proceedings of the 2009 international symposium on rule interchange and applications (RuleML 2009). Springer, Las Vegas, pp 315–322
Lam HP, Hashmi M, Scofield B (2016) Enabling reasoning with LegalRuleML. In: Alferes JJ, Bertossi L, Governatori G, Fodor P, Roman D (eds) Proceedings of the 10th international web rule symposium (RuleML 2016). Springer, Stony Brook, pp 241–257
LeFevre K, Agrawal R, Ercegovac V, Ramakrishnan R, Xu Y, DeWitt D (2004) Limiting disclosure in hippocratic databases. In: Proceedings of the thirtieth international conference on very large data bases, vol 30, VLDB endowment, VLDB ’04, pp 108–119
Leitner M, Rinderle-Ma S (2014) A systematic review on security in process-aware information systems? Constitution, challenges, and future directions. Inf Softw Technol 56(3):273–293
Leitner P, Wetzstein B, Rosenberg F, Michlmayr A, Dustdar S, Leymann F (2009) Runtime prediction of service level agreement violations for composite services. In: Proceedings of the 3rd workshop on non-functional properties and SLA management in service oriented computing. Springer, Heidelberg, pp 176–186
Leitner P, Michlmayr A, Rosenberg F, Dustdar S (2010) Monitoring, prediction and prevention of SLA violations in composite services. In: Proceedings of ICWS’10, pp 369–376
Letia IA, Groza A (2013) Compliance checking of integrated business processes. Data Knowl Eng 87:1–18
Liu Y, Müller S, Xu K (2007) A static compliance-checking framework for business process models. IBM Syst J 46(2):335–361
Lomuscio A, Qu H, Solanki M (2008) Towards verifying contract regulated service composition. In: Proceedings of ICWS’08, pp 254 –261
Ly LT (2012) SeaFlows—a compliance checking framework for supporting the process lifecycle. Ph.D. Thesis, University of Ulm, Osnabrck, Germany
Ly LT, Rinderle-Ma S, Göser K, Dadam P (2012) On enabling integrated process compliance with semantic constraints in process management systems. Inf Syst Front 14(2):195–219
Ly LT, Maggi FM, Montali M, Rinderle S, van der Aalst W (2013) A framework for the systematic comparison and evaluation of compliance monitoring approaches. In: Proceeding of EDOC’13. IEEE Computer Society
Ly LT, Maggi FM, Montali M, Rinderle-Ma S, van der Aalst WM (2015) Compliance monitoring in business processes: functionalities, application, and tool-support. Inf Syst 54:209–234
Maggi F, Montali M, Westergaard M, van der Aalst W (2011) Monitoring business constraints with linear temporal logic: an approach based on colored automata. In: Proceedings of the 9th international conference on business process management (BPM 2011). Springer, pp 132–147
Maggi F, Montali M, van der Aalst W (2012) An operational decision support framework for monitoring business constraints. In: de Lara J, Zisman A (eds) Fundamental approaches to software engineering. Springer, Berlin, pp 146–162
Mateescu R, Sighireanu M (2003) Efficient on-the-fly model-checking ror regular alternation-free Mu-calculus. Sci Comput Program 46(3):255–281 (special issue on formal methods for industrial critical systems)
McIntyre SR (2008) Integrated governance, risk and compliance: improve performance and enhance productivity in federal agencies. Technical reports, PricewaterhouseCoopers
Meho LI, Tibbo HR (2003) Modeling the information-seeking behavior of social scientists: Ellis’s study revisited. J Am Soc Inf Sci Technol 54(6):570–587
Milosevic Z, Jösang A, Dimitrakos T, Patton MA (2002) Discretionary enforcement of electronic contracts. In: Proceedings of EDOC’02. IEEE Computer Society, Washington, DC, USA, pp 39–50
Milosevic Z, Sadiq S, Orlowska M (2006) Towards a methodology for deriving contract-compliant business processes. In: Dustdar S, Fiadeiro J, Sheth A (eds) Proceedings of the 4th international conference on business process management (BPM 2006). Springer, Vienna, pp 395–400
Milosevic Z, Sadiq S, Orlowska M (2006) Translating business contract into compliant business processes. In: Proceedings of EDOC’06. IEEE Computer Society, pp 211–220
Monakova G, Kopp O, Leymann F, Moser S, Schäfers K (2009) Verifying business rules using an SMT solver for BPEL processes. In: Business process, services computing and intelligent service management, Leipzig, Germany, pp 81–94. http://subs.emis.de/LNI/Proceedings/Proceedings147/article2475.html
Montali M, Maggi FM, Chesani F, Mello P, Aalst WMPvd (2014) Monitoring business constraints with the event calculus. ACM Trans Intell Syst Technol 5(1):17:1–17:30
Namiri K, Stojanovic N (2007) Pattern-based design and validation of business process compliance. In: Proceedings of CoopIS’07. Springer, Berlin, pp 59–76
Namiri K, Stojanovic N (2007) Using control patterns in business processes compliance. In: Proceedings of WISE’07, Springer, pp 178–190
Namiri K, Stojanovic N (2008) Towards a formal framework for business process compliance. In: Proceedings of MKWI’08, München
Namiri K, Stojanovic N (2008) Towards a formal framework for business process compliance. In: Multikonferenz Wirtschaftsinformatik (MKWI 2008), Germany, pp 1185–1196
Nishizaki S, Ohata T (2013) Real-time model checking for regulatory compliance. In: Das V, Chaba Y (eds) Mobile communication and power engineering, communications in computer and information science, vol 296. Springer, Berlin, pp 70–77
Nute D (ed) (1997) Defeasible deontic logic, synthese library, vol 263. Academic Publishers, Dordrecht
Nute D (2003) Defeasible logic. In: Bartenstein O, Geske U, Hannebauer M, Yoshie O (eds) Web knowledge management and decision support. Springer, Berlin, pp 151–169
OASIS LegalRuleML Technical Committee (2015) LegalRuleML technical committee specifications. https://www.oasis-open.org/committees/legalruleml/charter.php, Retrieved 12 March 2016
OCEG (2012) Governance, Risk and Compliance Capability Model. https://www.oceg.org/about/what-is-grc/
Ochsenschläger P, Repp J, Rieke R, Nitsche U (1998) The SH-verification tool–abstraction-based verification of co-operating systems. J Form Asp Comput 10(4):381–404
Olivieri F (2014) Compliance by design. Synthesis of business processes by declarative specifications. Ph.D. Thesis, Dipartimento di Informatica, Università digli Studi di Verona, Italy and Institute for Integrated and Intelligent Systems, Griffith University, Australia
OMG (2010) Business Process Model Notation (BPMN). Standard. http://www.omg.org/spec/BPMN/2.0/
OMG (2011) Unified Modeling Language (UML 2.0). http://www.omg.org/spec/UML/2.0/
O’Neill A (2014) An Action framework for compliance and governance. Int J Clin Gov 19(4):342–359
Otto PN, Anton AI (2007) Addressing legal requirements in requirements engineering. In: Proceedings of the 15th IEEE international requirements engineering conference (RE 2007). IEEE Computer Society, pp 5–14
Pattersson P, Larson K (2000) UPPAAL 2K. Bull Eur Assoc Theor Comput Sci 70:40–44
Pershkow BI (2002) Sarbanes-Oxley: investment company compliance. J Invest Compliance 3(4):16–30
Pesic M, Schonenberg H, van der Aalst W (2007) DECLARE: full support for loosely-structured processes. In: Proceedings of 11th IEEE international conference on enterprise distributed object computing (EDOC’07), pp 287–287
Prakken H, Sergot M (1997) Dyadic denontic logic and contrary-to-duty obligations. In: [151], pp 223–262
Ramezani E, Fahland D, van der Aalst W (2012) Where did i misbehave? Diagnostic information in compliance checking. In: Proceedings of the 10th international conference on Business Process Management (BPM 2012), Tallinn, Estonia, pp 262–278
Ramezani E, Fahland D, van Dongen BF, van der Aalst W (2013) Diagnostic information for compliance checking of temporal compliance requirements. In: Proceedings of the 25th international conference on advanced information systems engineering (CAiSE 2013), Valencia, Spain, pp 304–320
Rangan RM, Rohde SM, Peak R, Chadha B, Bliznakov P (2005) Streamlining product lifecycle processes: a survey of product lifecycle management implementations, directions, and challenges. J Comput Inf Sci Eng 5(3):227–237
Rieke R, Repp J, Zhdanova M, Eichler J (2014) Monitoring security compliance of critical processes. 2014 22nd Euromicro international conference on parallel, distributed, and network-based processing (PDP 2014). Italy, Torino, pp 552–560
Rifaut A, Dubois E (2008) Using goal-oriented requirements engineering for improving the quality of ISO/IEC 15504 based compliance assessment frameworks. In: Proceedings of the 16th IEEE international requirements engineering conference (RE 2008), pp 33–42
Rikhardsson P, Best PJ, Green P, Rosemann M (2006) Business process risk management and internal control: a proposed research agenda in the context of compliance and ERP systems. In: Second Asia/Pacific research symposium on accounting information systems, Melbourne
Rinderle-Ma S, Mangler J (2011) Integration of process constraints from heterogeneous sources in process-aware information systems. International workshop on enterprise modelling and information systems architectures (EMISA 20110). Hamburg, Germany, pp 51–64
Roddick JF, Al-Jadir L, Bertossi L, Dumas M, Estrella F, Gregersen H, Hornsby K, Lufter J, Mandreoli F, Männistö T, Mayol E, Wedemeijer L (2000) Evolution and change in data management–issues and directions. SIGMOD Rec 29(1):21–25
Rosemann M, zur Muehlen M (2005) Integrating risks in business process models. In: Proceedings of ACIS’05
Sadiq S, Governatori G, Namiri K (2007) Modeling control objectives for business process compliance. In: Proceedings of BPM’07. Springer, pp 149–164
Salnitri M, Dalpiaz F, Giorgini P (2014) Modeling and verifying security policies in business processes. In: Bider I, Gaaloul K, Krogstie J, Nurcan S, Proper HA, Schmidt R, Soffer P (eds) Proceedings of the 15th international conference on business process modeling, development and support (BPMDS 2014). Springer, Berlin, pp 232–249
Sapkota K, Aldea A, Duce DA, Younas M, Bañares Alcántara R (2011) Towards semantic methodologies for automatic regulatory compliance support. In: Proceedings of PIKM’11, pp 83–86
Scannapieco S, Governatori G, Olivieri F, Cristani M (2011) Designing for compliance: norms and goal. In: The 5th international symposium on rules: research based and industry focused (RuleML 2011), Ft Lauderdale
Schleicher D, Anstett T, Leymann F, Mietzner R (2009) Maintaining compliance in customizable process models. In: Meersman R, Dillon T, Herrero P (eds) On the move to meaningful internet systems: OTM 2009. Springer, Heidelberg, pp 60–75
Schmidt R, Bartsch C, Oberhauser R (2007) Ontology-based representation of compliance requirements for service processes. In: Proceedings of the workshop on semantic business process and product lifecycle management, pp 28–39
Schrefl M, Stumptner M (2002) Behavior-consistent specialization of object life cycles. ACM Trans Softw Eng Methodol 11(1):92–148
Schumm D, Turetken O, Kokash N, Elgammal A, Leymann F, Heuvel WJVD (2010) Business process compliance through reusable units of compliant processes. In: Proceedings of the 10th international conference on current trends in web engineering. Springer, Vienna, Austria, pp 325–337
Semmelrodt F, Knuplesch D, Reichert M (2014) Modeling the resource perspective of business process compliance rules with the extended compliance rule graph. Proceeding of the 15th international conference on enterprise. Business-process and information systems modeling, Thessaloniki, Greece, pp 48–63
Spira LF, Page M (2003) Risk management: the reinvention of internal control and the changing role of internal audit. Account Audit Account J 16(4):640–661
Strecker S, Heise D, Frank U (2011) RiskM: a multi-perspective modeling method for IT risk assessment. Inf Syst Front 13(4):595–611
Stumptner M, Schrefl M (2000) Behavior consistent inheritance in UML. In: Laender AHF, Liddle SW, Storey VC (eds) Proceedings of the 19th international conference on conceptual modeling (ER 2000). Springer, Berlin, pp 527–542
Suriadi S, Weiß B, Winkelmann A, ter Hofstede AHM, Adams M, Conforti R, Fidge C, La Rosa M, Ouyang C, Pika A, Rosemann M, Wynn M (2014) Current research in risk-aware business process management–overview, comparison, and gap analysis. Commun Assoc Inf Syst 34(1):933–984
Teresa M, Gómez-López Gasca RM, Pérez-Álvarez JM (2015) Compliance validation and diagnosis of business data constraints in business processes at runtime. Inf Syst 48:26–43
The Basel Committee on Banking Supervision (2004) BASEL II accord - the international convergence of capital measurement and capital standards: a revised framework. https://www.bis.org/publ/bcbsca.htm
Trčka N, van der Aalst WMP, Sidorova N (2009) Data-flow anti-patterns: discovering data-flow errors in workflows. In: van Eck P, Gordijn J, Wieringa R (eds) Proceedings of the 21st international conference on advanced information systems engineering (CAiSE 2009). Springer, Berlin, pp 425–439
Turki S, Marija BO (2010) Compliance in e-government service engineering: state-of-the-art. 1st International conference on exploring services science (IESS (2010) Springer. Switzerland, Geneva, pp 270–275
US-Government (2002) Public Company Accounting Reforms and Investor Protection Act (Sarbanes-Oxley Act), Public Law 107–204, 116 Stat. 745
van der Aalst WM, Basten T (2001) Identifying commonalities and differences in object life cycles using behavioral inheritance. In: Colom JM, Koutny M (eds) Proceedings of the 22nd international conference on application and theory of Petri nets (ICATPN 2001). Springer, Berlin, pp 32–52
van der Aalst WMP, de Medeiros AKA (2005) Process mining and security: detecting anomalous process executions and checking process conformance. Electron Notes Theor Comput Sci 121(Suppl C):3–21. https://doi.org/10.1016/j.entcs.2004.10.013
van der Aalst W, de Beer HT, van Dongen BT (2005) Process mining and verification of properties: an approach based on temporal logic. In: Robert Meersman ZT (ed) CoopIS’05. Springer, Berlin, pp 130–147
van der Aalst W, van Hee KM, van Werf JM, Verdonk M, (2010) Auditing 2.0: using process mining to support tomorrow’s auditor. Computer 43(3):90–93
van der Aalst W, van Hee K, van der Werf JM, Kumar A, Verdonk M (2011) Conceptual model for online auditing. Decis Support Syst 50(3):636–647
van der Aalst W, Adriansyah A, van Dongen B (2012) Replaying history on process models for conformance checking and performance analysis. Wiley Interdiscip Rev Data Min Knowl Discov 2(2):182–192
Vázquez-Salceda J, Aldewereld H, Grossi D, Dignum F (2008) From human regulations to regulated software agents’ behavior. Artif Intell Law 16(1):73–87
Vicente P, Mira da Silva M (2011) A conceptual model for integrated governance, risk and compliance. In: Mouratidis H, Rolland C (eds) Advanced information systems engineering. Springer, Berlin, pp 199–213
Wang Z, ter Hofstede AH, Ouyang C, Wynn M, Wang J, Zhu X (2014) How to guarantee compliance between workflows and product lifecycles? Inf Syst 42:195–215
Ward M (1995) Principles and applications of electrochemical quartz crystal microbalance. Physical electrochemistry: principles, methods and applications. Marcel Dekker Inc, New York, pp 293–338
Wouters P, Costas R (2012) Users, narcissism and control ? tracking the impact of scholarly publications in the 21st century. Technical reports, SURFfoundation, Utrecht, The Netherland
Yip F, Parameswaran N, Ray P (2007) Rules and ontology in compliance management. In: Proceedings of EDOC’07, Washington, DC, USA, p 435
Yu J, Manh T, Han J, Jin Y, Han Y, Wang J (2006) Pattern based property specification and verification for service composition. In: Proceedings of WISE 2006. Springer, pp 156–168
Yu J, Han YB, Han J, Jin Y, Falcarin P, Morisio M (2008) Synthesizing service composition models on the basis of temporal business rules. J Comput Sci Technol 23:885–894
Zeni N, Kiyavitskaya N, Mich L, Cordy JR, Mylopoulos J (2013) GaiusT: supporting the extraction of rights and obligations for regulatory compliance. Requir Eng 20(1):1–22
Acknowledgements
We thank Régis Riveret for his valuable discussions and suggestions and anonymous reviewers for their many valuable comments and suggestions.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hashmi, M., Governatori, G., Lam, HP. et al. Are we done with business process compliance: state of the art and challenges ahead. Knowl Inf Syst 57, 79–133 (2018). https://doi.org/10.1007/s10115-017-1142-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10115-017-1142-1