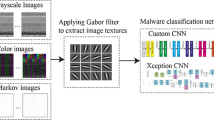
Abstract
Rapid advancement in the sophistication of malware has posed a serious impact on the device connected over the Internet. Malware writing is driven by economic benefits; thus, an alarming increase in malware variants is witnessed. Recently, a large volume of malware attacks are reported on Internet of Things (IoT) networks; as these devices are exposed to insecure segments, further IoT devices reported have hardcoded credentials. To combat malware attacks on mobile devices and desktops, deep learning-based detection approaches have been attempted to detect malware variants. The existing solutions require large computational overhead and also have limited accuracy. In this paper, we visualize malware as Markov images to preserve semantic information of consecutive pixels. We further extract textures from Markov images using Gabor filter (named as Gabor images), and subsequently develop models using VGG-3 and Densely Connected Network (DenseNet). To encourage real-time malware detection and classification, we fine-tune Densely Connected Network. These models are trained and evaluated on two datasets namely Malimg and BIG2015. In our experimental evaluations, we found that DenseNet identifies Malimg and BIG2015 samples with accuracies of 99.94% and 98.98%, respectively. Additionally, the performance of our proposed method in classifying malware files to their respective families is superior compared to the state-of-the approach calibrated using prediction time, F1-score, and accuracy.













Similar content being viewed by others
References
BBC N Cyber-attack: Europol says it was unprecedented in scale. http://www.bbc.com/news/world-europe-39907965
https://blog.logsign.com/the-biggest-cyber-attacks-in-2019/ (accessed Jan 1, 2021)
Internet security threat report 2021, https://www.sophos.com/en-us/medialibrary/pdfs/technical-papers/sophos-2021-threat-report.pdf
https://crowdresearchpartners.com/portfolio/byod-mobile-security-report/(accessed Jan.1, 2021)
AV-Test Threat Report: https://www.av-test.org/de/statistiken/malware/ (accessed Jan 1, 2020)
Kang H, Jang J, Mohaisen A, Kim H K (2015) Detecting and Classifying Android Malware Using Static Analysis along with Creator Information. Int J Distrib Sens Netw 11(6)
Han W, Xue J, Wang Y, Huang L, Kong Z, Mao L (2019) MalDAE: Detecting and explaining malware based on correlation and fusion of static and dynamic characteristics. Comput Secur 83:208–233
Pascanu R, Stokes J W, Sanossian H, Marinescu M, Thomas A (2015) Malware classification with recurrent networks. In: Proc. IEEE Int. Conf. Acoust., Speech Signal Process. (ICASSP), pp 1916–1920.
Vinayakumar R, Alazab M, Soman K P, Poornachandran P, Venkatraman S (2019) Robust Intelligent Malware Detection Using Deep Learning. IEEE Access 7:46717–46738
Nataraj L, Karthikeyan S, Jacob G, Manjunath BS (2011) Malware Images: Visualization and Automatic Classification. In: Proc. 8th International Symposium, Visualization for Cyber Security, VizSec
Fu J, Xue J, Wang Y, Liu Z, Shan C (2018) Malware Visualization for Fine-Grained Classification. IEEE Access 6:14510–14523
Zhong W, Gu F (2019) A Multi-Level deep learning system for malware detection. Expert Syst Appl 133:151–162
Hazra A, Choudhary P, Sheetal Singh M (2021) Recent Advances in Deep Learning Techniques and Its Applications: An Overview. In: Rizvanov A.A, Singh B.K, Ganasala P (eds) Advances in Biomedical Engineering and Technology, Lecture Notes in Bioengineering. Springer, Singapore, pp 103–122
Gibert D, Mateu C, Planes J, Vicens R (2018) Classification of malware by using structural entropy on convolutional neural networks the thirtieth. AAAI conference on innovative applications of artificial intelligence (IAAI-18)
Agarap A F, Pepito F J H (2017) Towards building an intelligent anti-malware system: A deep learning approach using support vector machine (SVM) for malware classification, [online] Available: https://arxiv.org/abs/1801.003181801.00318
Le Q, Boydell O, Namee BM, Scanlon M (2018) Deep learning at the shallow end: Malware classification for non-domain experts. Digit Invest 26(Supplement):S118–S126
Jain A, Phanishayee A, Mars J, Tang L, Pekhimenko G (2018) Gist: Efficient Data Encoding for Deep Neural Network Training. ACM/IEEE 45th Annual International Symposium on Computer Architecture (ISCA), Los Angeles, pp 776–789
Zhang J, Qin Z, Yin H, Ou L, Zhang K (2019) A feature-hybrid malware variants detection using CNN based opcode embedding and BPNN based API embedding. Comput Secur 84:376– 392
Kim T, Kang B, Rho M, Sezer S, Im E G (2019) A multimodal deep learning method for android malware detection using various features. IEEE Trans Inf Forensic Secur 14(3):773–788
Nezhadkamali M, Soltani S, Seno S A H (2017) Android malware detection based on overlapping of static features. 7th International Conference on Computer and Knowledge Engineering (ICCKE)
Vasan D, Alazab M, Wassan S, Naeem H, Safaei B, Zheng Q (2020) IMCFN: Image-Based Malware Classification using Fine-tuned Convolutional Neural Network Architecture. Comput Netw 171
Shezan F H, Afroze SF, Iqbal A (2017) Vulnerability detectio n in recent Android apps: An empirical study. 2017 International Conference on Networking, Systems and Security (NSysS)
Xue D, Li J, Lv T, Wu W, Wang J (2019) Malware Classification Using Probability Scoring and Machine Learning. IEEE Access 7:91641–91656
Yoo S, Kim S, Kim S, Kang B B (2020) AI-hydra: Advanced hybrid approach using random forest and deep learning for malware classification. Inf Sci 546:420–435
Zhao Y-l, Qian Q (2018) Android Malware Identification Through Visual Exploration of Disassembly Files. Int J Netw Secur 20(6):1061–1073
Han K, Kang B, Im E G (2014) Malware analysis using visualized image matrices. Sci World J:1–15
Yuan B, Wang J, Liu D, Guo W, Wua P, Bao X (2020) Byte-level Malware Classification Based on Markov Images and Deep Learning. Comput Secur 92
Kalash M, Rochan M, Mohammed N, Bruce NDB, Wang Y, Iqbal F (2018) Malware Classification with Deep Convolutional Neural Networks. 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, pp 1–5
Roseline S A, Geetha S, Kadry S, Nam Y (2020) Intelligent Vision-Based Malware Detection and Classification Using Deep Random Forest Paradigm. IEEE Access 8:206303–206324
Gibert D, Mateu C, Planes J, Vicens R (2019) Using convolutional neural networks for classification of malware represented as images. J Comput Virol Hacking Techn 15(1):15–28
Khan RU, Zhang X, Kumar R (2019) Analysis of ResNet and GoogleNet models for malware detection. J Comput Virol Hacking Techn 15(1):29–37
Naeem H, Ullah F, Naeem M R, Khalid S, Vasan D, Jabbar S, Saeed S (2020) Malware detection in industrial internet of things based on hybrid image visualization and deep learning model. Ad Hoc Netw 10:102154
Tuncer T, Ertam F, Dogan S (2021) Automated malware identification method using image descriptors and singular value decomposition. Multimed Tools Appl:1–20
Çayır A, Unal U, Dağ H (2021) Random CapsNet forest model for imbalanced malware type classification task. Comput Secur 102:102133
Sun G, Qian Q (2021) Deep Learning and Visualization for Identifying Malware Families. IEEE Trans Depend Sec Comput 18(1):283–295
Feng R, Chen S, Xie X, Meng G, Lin S-W, Liu Y (2021) A Performance-Sensitive Malware Detection System Using Deep Learning on Mobile Devices. IEEE Trans Inf Forensic Secur 16:1563–1578
Cui Z, Xue F, Cai X, Cao Y, Wang G-g, Chen J (2018) Detection of Malicious Code Variants Based on Deep Learning. IEEE Trans Ind Inform 14(7)
Portable freeware collection, https://www.portablefreeware.com/ (accessed Feb 1, 2020)
Softonic, https://en.softonic.com/windows (accessed March 1, 2020)
Sourceforge https://sourceforge.net/ (accessed March 1, 2020)
DriverPack solution, https://drp.su/en (accessed February 18, 2020)
Ronen R, Radu M, Feuerstein C, Yom-Tov E, Ahmadi M (2018) Microsoft Malware Classification Challenge, arXiv:1802.10135
Yajamanam S, Selvin VRS (2018) Fabio di troia and Mark Stamp. Deep Learning versus Gist Descriptors for Image-based Malware Classification. 4th International Conference on Information Systems Security and Privacy, pp 553–561
Huang G, Liu Z, van der ML, Weinberger K Q (2017) Densely connected convolutional networks 2017. IEEE conference on computer vision and pattern recognition (CVPR)
Hussain M, Jordan J, Bird J J, Faria D R (2018) A Study on CNN Transfer Learning for Image Classification. Proceedings of 18th Annual UK Workshop on Computational Intelligence Nottingham
Rezende E, Ruppert G, Carvalho T, Theophilo A, Ramos F, de Geus P (2018) Malicious software classification using VGG16 deep neural network’s bottleneck features. In: Information Technology-New Generations. Springer, Cham, pp 51–59
Hazra A (2021) A comprehensive survey on chest diseases analysis: technique, challenges and future research directions. International Journal of Multimedia Information Retrieval
Choudhary P, Hazra A (2019) Chest disease radiography in twofold: using convolutional neural networks and transfer learning. Evolving Systems
C2LOP: https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Trojan:Win32/C2Lop.gen!M(Accessed on 2-December,2020)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Anandhi, V., Vinod, P. & Menon, V.G. Malware visualization and detection using DenseNets. Pers Ubiquit Comput 28, 153–169 (2024). https://doi.org/10.1007/s00779-021-01581-w
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00779-021-01581-w