Abstract
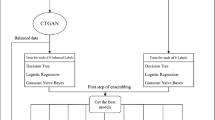
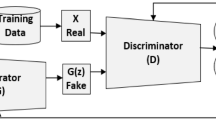
Intrusion detection systems (IDSs) investigate various attacks, identify malicious patterns, and implement effective control strategies. With the recent advances in machine learning and deep learning, designing an efficient IDS has become feasible. Existing Deep learning (DL) methods predominantly suffer from data loss or overfitting while handling class-imbalanced data. Generative adversarial networks (GANs) efficiently solve the overfitting class and overlap problems. However, GANs suffer from “instability” in the training process. Another issue also arises in GANs when the input data does not accurately reflect the actual distribution of the data, such that the generator would produce samples of one or a very small number of classes rather than generating samples for all minor classes at the same time; this behavior is called "mode collapse." To reduce the instability and mode collapse problems and improve the detection accuracy, we developed novel architectures for the generator and discriminator to improve the multi-attack detection problem with a stable training process using ensemble deep learning (EDL) models across various loss functions. To solve the mode collapse problem, we proposed multi-player GANs with teams of multiple generators and discriminators to optimize the learning process while minimizing the chance of mode collapsing. Experimental results over various benchmark datasets show that the developed ensemble-based multi-player GANs (EMP-GANs) outperform the existing methods in terms of quality while maintaining high training stability and minimal chances of mode collapse.



















Similar content being viewed by others
Data availability
The NSL-KDD and the UNSW-NB15 datasets generated during and/or analyzed during the current study are available in [73] and [74]. The NSL-KDD dataset [73] was constructed by Tavallaee et al. in 2009 using the KDD CUP 99 dataset to address redundancy problems. The UNSW-NB15 dataset [74] is generated at the Cyber Range Lab of the Australian Centre for Cybersecurity with Over 175,000 and 82,000 training and testing samples, respectively.
References
Lu K-D, Zeng G-Q, Luo X, Weng J, Luo W, Wu Y (2021) Evolutionary deep belief network for cyber-attack detection in industrial automation and control system. IEEE Trans Ind Inform 17(11):7618–7627. https://doi.org/10.1109/TII.2021.3053304
Alhajjar E, Maxwell P, Bastian N (2021) Adversarial machine learning in network intrusion detection systems. Expert Syst Appl 186:115782. https://doi.org/10.1016/j.eswa.2021.115782
Silva BR, Silveira RJ, da Neto MGS, Cortez PC, Gomes DG (2021) A comparative analysis of undersampling techniques for network intrusion detection systems design. J Commun Inf Syst. https://doi.org/10.14209/jcis.2021.3
Soleymanzadeh R, Kashef R (2022) The future roadmap for cyber-attack detection. In: 2022 6th international conference on cryptography, security and privacy (CSP), pp 66–70. https://doi.org/10.1109/CSP55486.2022.00021.
Ahmad Z, Shahid Khan A, Wai Shiang C, Abdullah J, Ahmad F (2021) Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans Emerg Telecommun Technol 32(1):4150. https://doi.org/10.1002/ett.4150
Goodfellow IJ et al (2014) Generative Adversarial Networks. ArXiv14062661 Cs Stat, http://arxiv.org/abs/1406.2661. Accessed Oct 20 2021 [Online]
Soleymanzadeh R, Kashef R (2022) A Stable generative adversarial network architecture for network intrusion detection, presented at the IEEE CSR
Zhang H, Goodfellow I, Metaxas D, Odena A (2019) Self-attention generative adversarial networks. In: Proceedings of the 36th international conference on machine learning, pp 7354–7363. https://proceedings.mlr.press/v97/zhang19d.html. Accessed Nov 02 2021 [Online].
Basati A, Faghih MM (2022) DFE: efficient IoT network intrusion detection using deep feature extraction. Neural Comput Appl 34(18):15175–15195. https://doi.org/10.1007/s00521-021-06826-6
Andresini G, Appice A, De Rose L, Malerba D (2021) GAN augmentation to deal with imbalance in imaging-based intrusion detection. Future Gener Comput Syst 123:108–127. https://doi.org/10.1016/j.future.2021.04.017
Ger S, Klabjan D (2020) Autoencoders and generative adversarial networks for imbalanced sequence Classification. ArXiv190102514 Cs Stat, http://arxiv.org/abs/1901.02514. Accessed Nov 19 2021 [Online]
Rashid M, Kamruzzaman J, Imam T, Kaisar S, Alam MJ (2020) Cyber attacks detection from smart city applications using artificial neural network. In: 2020 IEEE Asia-Pacific conference on computer science and data engineering (CSDE), Gold Coast, Australia, pp 1–6. https://doi.org/10.1109/CSDE50874.2020.9411606.
Buczak AL, Guven E (2016) A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun Surv Tutor 18(2):1153–1176. https://doi.org/10.1109/COMST.2015.2494502
Khan RU, Zhang X, Kumar R, Sharif A, Golilarz NA, Alazab M (2019) An adaptive multi-layer botnet detection technique using machine learning classifiers. Appl Sci. https://doi.org/10.3390/app9112375
Farid DMd, Zhang L, Rahman CM, Hossain MA, Strachan R (2014) Hybrid decision tree and naïve Bayes classifiers for multi-class classification tasks. Expert Syst Appl 41(4):1937–1946. https://doi.org/10.1016/j.eswa.2013.08.089
Han C et al (2019) Combining noise-to-image and image-to-image GANs: brain MR image augmentation for tumor detection. IEEE Access 7:156966–156977. https://doi.org/10.1109/ACCESS.2019.2947606
Wang Y, Wu C, Herranz L, van de Weijer J, Gonzalez-Garcia A, Raducanu B (2018) Transferring GANs: generating images from limited data In: presented at the proceedings of the european conference on computer vision (ECCV), pp 218–234. https://openaccess.thecvf.com/content_ECCV_2018/html/yaxing_wang_Transferring_GANs_generating_ECCV_2018_paper.html. Accessed Sep 25 2022 [Online]
Kazeminia S et al (2020) GANs for medical image analysis. Artif Intell Med 109:101938. https://doi.org/10.1016/j.artmed.2020.101938
Zhang C, Ruan F, Yin L, Chen X, Zhai L, Liu F (2019) A deep learning approach for network intrusion detection based on nsl-kdd dataset. In: 2019 IEEE 13th international conference on anti-counterfeiting, security, and identification (ASID), pp 41–45. https://doi.org/10.1109/ICASID.2019.8925239
Wang S, Xia C, Wang T (2019) A novel intrusion detector based on deep learning hybrid methods. In: 2019 IEEE 5th intl conference on big data security on cloud (BigDataSecurity), IEEE intl conference on high performance and smart computing, (HPSC) and IEEE intl conference on intelligent data and Security (IDS), Washington, DC, USA, pp 300–305. https://doi.org/10.1109/BigDataSecurity-HPSC-IDS.2019.00062
Zhe W, Wei C, Chunlin L (2020) DoS attack detection model of smart grid based on machine learning method. In: 2020 ieee international conference on power, intelligent computing and systems (ICPICS), pp. 735–738. https://doi.org/10.1109/ICPICS50287.2020.9202401.
Meira J Performance evaluation of unsupervised techniques in cyber-attack anomaly detection. p 13
Kumar P, Gupta GP, Tripathi R (2021) Toward design of an intelligent cyber attack detection system using hybrid feature reduced approach for IoT networks. Arab J Sci Eng 46(4):3749–3778. https://doi.org/10.1007/s13369-020-05181-3
Lin W-H, Lin H-C, Wang P, Wu B-H, Tsai J-Y (2018) Using convolutional neural networks to network intrusion detection for cyber threats. In: 2018 IEEE International conference on applied system invention (ICASI), Chiba, pp 1107–1110. https://doi.org/10.1109/ICASI.2018.8394474.
Nabil M, Mahmoud M, Ismail M, Serpedin E (2019) Deep recurrent electricity theft detection in ami networks with evolutionary hyper-parameter tuning. In: 2019 international conference on internet of things (ithings) and ieee green computing and communications (GreenCom) and IEEE Cyber, physical and social computing (CPSCom) and IEEE smart data (SmartData), Atlanta, GA, USA, pp 1002–1008. https://doi.org/10.1109/iThings/GreenCom/CPSCom/SmartData.2019.00175.
Sriram S, Vinayakumar R, Alazab M, Kp S (2020) Network flow based iot botnet attack detection using deep learning. In: IEEE INFOCOM 2020 - IEEE conference on computer communications workshops (INFOCOM WKSHPS), Toronto, ON, Canada, pp. 189–194. https://doi.org/10.1109/INFOCOMWKSHPS50562.2020.9162668.
McDermott CD, Majdani F, Petrovski AV (2018) Botnet detection in the internet of things using deep learning approaches. In: 2018 International joint conference on neural networks (IJCNN), pp. 1–8. https://doi.org/10.1109/IJCNN.2018.8489489.
Tama BA, Comuzzi M, Rhee K-H (2019) TSE-IDS: a two-stage classifier ensemble for intelligent anomaly-based intrusion detection system. IEEE Access 7:94497–94507. https://doi.org/10.1109/ACCESS.2019.2928048
Keserwani PK, Govil MC, Pilli ES, Govil P (2021) A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. J Reliab Intell Environ 7(1):3–21. https://doi.org/10.1007/s40860-020-00126-x
Jiang K, Wang W, Wang A, Wu H (2020) network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access 8:32464–32476. https://doi.org/10.1109/ACCESS.2020.2973730
Divekar A, Parekh M, Savla V, Mishra R, Shirole M (2018) Benchmarking datasets for Anomaly-based Network Intrusion Detection: KDD CUP 99 alternatives. In: 2018 IEEE 3rd international conference on computing, communication and security (ICCCS), pp. 1–8. https://doi.org/10.1109/CCCS.2018.8586840.
Hardy C, Le Merrer E, Sericola B (2019) MD-GAN: Multi-Discriminator Generative Adversarial Networks for Distributed Datasets. In: 2019 ieee international parallel and distributed processing symposium (IPDPS), pp 866–877. https://doi.org/10.1109/IPDPS.2019.00095.
Wei J, Liu M, Luo J, Zhu A, Davis J, Liu Y (2022) DuelGAN: a duel between two discriminators stabilizes the gan training. arXiv Mar. 20 2022. http://arxiv.org/abs/2101.07524. Accessed Jun 29 2022 [Online].
Chen H, Jiang L (2021) Efficient GAN-based method for cyber-intrusion detection. ArXiv190402426 Cs Stat, http://arxiv.org/abs/1904.02426. Accessed Oct 28 2021. [Online]
Hao et al X (2021) Producing more with less: a GAN-based network attack detection approach for imbalanced data. In: 2021 IEEE 24th international conference on computer supported cooperative work in design (CSCWD), pp. 384–390. https://doi.org/10.1109/CSCWD49262.2021.9437863.
Bourou S, El Saer A, Velivassaki T-H, Voulkidis A, Zahariadis T (2021) A review of tabular data synthesis using GANs on an IDS dataset. Information. https://doi.org/10.3390/info12090375
Kaur S, Singh M (2020) Hybrid intrusion detection and signature generation using deep recurrent neural networks. Neural Comput Appl 32(12):7859–7877. https://doi.org/10.1007/s00521-019-04187-9
Liu X, Li T, Zhang R, Wu D, Liu Y, Yang Z (2021) A GAN and feature selection-based oversampling technique for intrusion detection. Secur Commun Netw 2021:1–15. https://doi.org/10.1155/2021/9947059
Wang W, Chai Y, Li Y (2022) GAGIN: generative adversarial guider imputation network for missing data. Neural Comput Appl 34(10):7597–7610. https://doi.org/10.1007/s00521-021-06862-2
Qaddoura R, Al-Zoubi AM, Almomani I, Faris H (2021) a multi-stage classification approach for iot intrusion detection based on clustering with oversampling. Appl Sci. https://doi.org/10.3390/app11073022
Dlamini G, Fahim M (2021) DGM: a data generative model to improve minority class presence in anomaly detection domain. Neural Comput Appl 33(20):13635–13646. https://doi.org/10.1007/s00521-021-05993-w
Bagui S, Li K (2021) Resampling imbalanced data for network intrusion detection datasets. J Big Data 8(1):6. https://doi.org/10.1186/s40537-020-00390-x
Zuech R, Hancock J, Khoshgoftaar TM (2021) Detecting web attacks using random undersampling and ensemble learners. J Big Data 8(1):75. https://doi.org/10.1186/s40537-021-00460-8
Mukkamala S, Sung A, Abraham, A Cyber security challenges: designing efficient intrusion detection systems and antivirus tools. p 27
Kalnoor G, Gowrishankar S (2021) IoT-based smart environment using intelligent intrusion detection system. Soft Comput 25(17):11573–11588. https://doi.org/10.1007/s00500-021-06028-1
Devan P, Khare N (2020) An efficient XGBoost–DNN-based classification model for network intrusion detection system. Neural Comput Appl 32(16):12499–12514. https://doi.org/10.1007/s00521-020-04708-x
Soe YN, Feng Y, Santosa PI, Hartanto R, Sakurai K (2020) Towards a lightweight detection system for cyber attacks in the iot environment using corresponding features. Electronics. https://doi.org/10.3390/electronics9010144
Schmidhuber J (2015) Deep learning in neural networks: an overview. Neural Netw 61:85–117. https://doi.org/10.1016/j.neunet.2014.09.003
Ghanem K, Aparicio-Navarro FJ, Kyriakopoulos KG, Lambotharan S, Chambers JA Support Vector Machine for Network Intrusion and Cyber-Attack Detection. p 5
Hasan M, Islam MdM, Zarif MII, Hashem MMA (2019) Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 7:100059. https://doi.org/10.1016/j.iot.2019.100059
Xin Y et al (2018) Machine learning and deep learning methods for cybersecurity. IEEE Access 6:35365–35381. https://doi.org/10.1109/ACCESS.2018.2836950
Ledig C et al (2017) Photo-realistic single image super-resolution using a generative adversarial network. In: 2017 IEEE conference on computer vision and pattern recognition (CVPR), pp 105–114. https://doi.org/10.1109/CVPR.2017.19.
Mohammed AHK, Jebamikyous H-H, Nawara D, Kashef R (2021) IoT text analytics in smart education and beyond. J Comput High Educ. https://doi.org/10.1007/s12528-021-09295-x
Rajadurai H, Gandhi UD (2022) A stacked ensemble learning model for intrusion detection in wireless network. Neural Comput Appl 34(18):15387–15395. https://doi.org/10.1007/s00521-020-04986-5
Niraja KS, Srinivasa Rao S (2021) A hybrid algorithm design for near real time detection cyber attacks from compromised devices to enhance IoT security. Today Proc Mater. https://doi.org/10.1016/j.matpr.2021.01.751
Salimans T et al. (2016) "Improved Techniques for Training GANs," in Advances in Neural Information Processing Systems, vol. 29. https://proceedings.neurips.cc/paper/2016/hash/8a3363abe792db2d8761d6403605aeb7-Abstract.html. Accessed Nov 02 2021 [Online]
Karras T, Laine S, Aila T A Style-Based generator architecture for generative adversarial networks. p 10.
Yilmaz I, Masum R, Siraj A, (2020) Addressing Imbalanced data problem with generative adversarial network for intrusion detection. In: 2020 IEEE 21st international conference on information reuse and integration for data science (IRI), pp 25–30. https://doi.org/10.1109/IRI49571.2020.00012.
Zhang X, Sun Y, Liu L (2021) An improved generative adversarial network for translating clothes from the human body to tiled image. Neural Comput Appl 33(14):8445–8457. https://doi.org/10.1007/s00521-020-05598-9
Wang X, Chen X, Wang Y (2021) Small vehicle classification in the wild using generative adversarial network. Neural Comput Appl 33(10):5369–5379. https://doi.org/10.1007/s00521-020-05331-6
Li W, Fan L, Wang Z, Ma C, Cui X (2021) Tackling mode collapse in multi-generator GANs with orthogonal vectors. Pattern Recognit 110:107646. https://doi.org/10.1016/j.patcog.2020.107646
Shi H, Wang L, Zheng N, Hua G, Tang W (2022) Loss functions for pose guided person image generation,". Pattern Recognit. 122:108351. https://doi.org/10.1016/j.patcog.2021.108351
Kong F, Li J, Jiang B, Wang H, Song H (2021) Integrated generative model for industrial anomaly detection via Bi-directional LSTM and attention mechanis. IEEE Trans Ind Inform. https://doi.org/10.1109/TII.2021.3078192
Huang G, Jafari AH (2021) Enhanced balancing GAN: minority-class image generation. Neural Comput Appl. https://doi.org/10.1007/s00521-021-06163-8
Hong S, Kim S, Kang S (2019) Game sprite generator using a multi discriminator GAN. KSII Trans Internet Inf Syst. https://doi.org/10.3837/tiis.2019.08.025
Durugkar I, Gemp I, Mahadevan S (2017) Generative multi-adversarial networks. Arxiv Mar. 02, 2017. Available: http://arxiv.org/abs/1611.01673. Accessed Jul 5 2022, [Online]
Soleymanzadeh R, Kashef R The analysis of the generator architectures and loss functions in improving the stability of GANs training towards efficient intrusion detection, presented at the India International Congress on Computational Intelligence (IICCI), p. 7.
Ho Y, Wookey S (2020) The real-world-weight cross-entropy loss function: modeling the costs of mislabeling. IEEE Access 8:4806–4813. https://doi.org/10.1109/ACCESS.2019.2962617
Arjovsky M, Chintala S, Bottou L (2017) Wasserstein GAN. ArXiv170107875 Cs Stat, http://arxiv.org/abs/1701.07875. Accessed Nov 02 2021,[Online]
Stanczuk J, Etmann C, Kreusser LM, Schönlieb C-B Wasserstein GANs Work Because They Fail (to Approximate the Wasserstein Distance). arXiv, Oct. 05, 2021. http://arxiv.org/abs/2103.01678. Accessed Oct 26 2022 [Online]
Borji A (2018) Pros and cons of GAN evaluation measures. ArXiv180203446 Cs. [Online]. Available: http://arxiv.org/abs/1802.03446. Accessed Nov 2 2021
Moustafa N, Turnbull B, Choo K-KR (2019) An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of internet of things. IEEE Internet Things J 6(3):4815–4830. https://doi.org/10.1109/JIOT.2018.2871719
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set, In: 2009 IEEE symposium on computational intelligence for security and defense applications, pp. 1–6. https://doi.org/10.1109/CISDA.2009.5356528.
Moustafa N,. Slay J (2015) UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set)," In: 2015 military communications and information systems conference (MilCIS), pp. 1–6. https://doi.org/10.1109/MilCIS.2015.7348942.
Tesfahun A, Bhaskari DL (2013) Intrusion detection using random forests classifier with SMOTE and feature reduction. In: 2013 International conference on cloud & ubiquitous computing & emerging technologies, pp 127–132. https://doi.org/10.1109/CUBE.2013.31.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Soleymanzadeh, R., Kashef, R. Efficient intrusion detection using multi-player generative adversarial networks (GANs): an ensemble-based deep learning architecture. Neural Comput & Applic 35, 12545–12563 (2023). https://doi.org/10.1007/s00521-023-08398-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-023-08398-z