Abstract
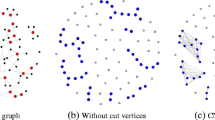
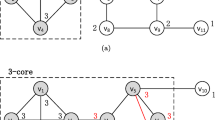
Identifying critical nodes in complex networks aims to fragment a graph \(G = (V, E)\) by removing a set of vertices R with cardinality \(\left| R \right| \le \) k, such that the residual graph has minimum pairwise connectivity. Existing optimization algorithms are incapable of finding a good set R in complex networks. By investigating the role of nodes, a minimum dominating set approach is considered in controlling a network. This paper presents an algorithmic procedure to compute the critical nodes using a novel minimum connected dominating set, in which the critical nodes are identified based on the number of close subsequences. Through experimental verification on some randomly generated networks and comparing with the similar algorithms, the results showed that the proposed algorithm has high capability of identifying the critical nodes and low time complexity.










Similar content being viewed by others
References
Agrawal D, Budak C, Abbadi AE (2011) Information diffusion in social networks: observing and influencing societal interests. In: 2011 Proceedings of the VLDB endowment. IEEE, pp 1512–1518
Balaji S, Revathi N (2012) An efficient heuristic for the minimum connected dominating set problem on ad hoc wireless networks. World Acad Sci Eng Technol 6(9):8–22
Barabsi A-L, Bonabeau E (2003) Scale-free networks. Sci Am 6(9):50–59
Callaway DS, Newman MEJ, Strogatz SH, Watts DJ (2000) Network robustness and fragility: percolation on random graphs. Phys Rev Lett 85(25):5468–5471
Cao YJ, Ding LJ, Wang GZ, Bao ZJ, Han ZX (2009) Analysis on cascading failure and self-organized criticality in evolving power grids. Autom Electr Power Syst 33(5):1–6
Chakradhar P, Yogesh P (2014) Energy efficient minimum connected dominating set algorithm for manets. Int Conf Recent Trends Inf Technol 7(9):270–282
Chamodrakas I, Martakos D (2015) An improved algorithm for minimum connected dominating sets in ad hoc networks. ICIC Express Lett 13(5):202–209
Chen H, Xu J, Wang G, Qin Y, Chau M, Chung W (2004) Crime data mining: a general framework and some examples. Computer 4(37):50–56
Dan X, Xiao-Fan W, Xiang L (2010) An investigation on local area control of virus spreading in complex networks. Acta Phys 13(3):1313–1317
Ding D (2012) Identification of crucial nodes in biological networks. Netw Biol 15(3):118–127
Firmani D, Italiano GF, Laura L (2015) The (not so) critical nodes of criminal networks. Soc Inf 8(3):87–96
Freeman LC (1998) Centrality in social networks. Soc Netw 14(7):1170–1182
Girvan M, Newman MEJ (2006) Community structure in social and biological networks. PhysRevE 8(4):147–160
Kinney R, Albert R, Latora V, Crucitti P (2005) Modeling cascading failures in the North American power grid. Eur Phys J B 46(9):101–107
Li J, Li M, Li J, Chen X (2014) Secure deduplication with efficient and reliable convergent key management. IEEE Trans Parallel Distrib Syst 25(6):1615–1625. doi:10.1109/TPDS.2013.284
Lu TYXWYHSB, Piao XF (2012) Energy efficient minimum connected dominating set algorithm for manets. Acta Phys 61(9):170–179
Nguyen DT, Shen Y, Thai MT (2013) Detecting critical nodes in interdependent power networks for vulnerability assessment. IEEE Trans Smart Grid 11(9):151–159
Shen Y, Nguyen NP, Xuan Y, Thai MT (2014) On the discovery of critical links and nodes for assessing network vulnerability. IEEE/ACM Trans Netw 21(3):963–973
Sweet N, Kanefsky S (2013) The c2 constellation air force network centric warfare program. In: 2013 Command and control research and technology symposium. IEEE, pp 563–571
Ventresca M, Aleman D (2015) Efficiently identifying critical nodes in large complex networks. Comput Soc Netw 6(2):179–188
Ventresca M, Ombuki-Berman BM, Harrison KR (2015) An experimental evaluation of multi-objective evolutionary algorithms for detecting critical nodes in complex networks. Appl Evol Comput 7(3):164–176
Veremyev A, Pasiliao EL, Boginski V (2014) Exact identification of critical nodes in sparse networks via new compact formulations. Optim Lett 8(5):1245–1259
Vida R, Cuenda S, Galeano J (2013) Identifying critical nodes in multi-layered networks under multi-vector malware attack. Int J Complex Syst Sci 3(5):97–105
Wang XG (2014) An algorithm for critical nodes problem in social networks based on owen value. Sci World J 15(10):72–82
Wang P, Lu J, Yu X (2014) Identification of important nodes in artificial bio-molecular networks. In: 2014 IEEE international symposium on circuits and systems. IEEE, pp 1267–1276
Xu J, Chen H (2005) Criminal network analysis and visualization. Commun ACM 48(6):100–107
Xu Y, Gao Z, Xiao B, Meng F, Lin Z (2013) key nodes evaluation with multi-criteria in complex networks based on ahp analysis. In: Proceedings of IEEE IC-BNMT2013. IEEE, pp 175–182
Yan-Chao Z, Hai-Feng Z, Hui C, Fei X, Yun L (2011) The research of information dissemination model on online social network. Acta Phys 60(16):171–179
Yan R, Tang J, Liu X, Shan D, Li X (2012) Citation count prediction: learning to estimate future citations for literature. In: Proceedings of the 20th ACM international conference on Information and knowledge management. IEEE, pp 1247–1252
Yong XXH (2015) Research on the dynamics of opinion spread based on social network services. Acta Phys 15(9):973–979
Yu G (2011) Novel connected dominating set algorithm based on minimum spanning tree. J Comput Appl 26(9):327–335
Zachary WW (1977) An information flow model for conflict and fission in small groups. J Anthropol Res 11(2):452–473
Zhongtai C, Xiaohuan W, Ning M, Xiuqing S (2015) Key nodes identify in the peasants social network based on structural hole theory. Int J Hybrid Inf Technol 8(2):251–258
Zhu J, Yang XJ (2015) Recognizing key nodes in area communication network. Electron Inf Warf Technol 64(7):46–52
Acknowledgments
This research is supported by the financial support from Zhejiang Provincial Natural Science Foundation of China under Grant Nos. LY16F020027, LZ15F030004 and LY15F020040, Zhejiang Provincial Education Department Research Foundation of China under Grant No.Y201533771, Humanity and Social Science Youth foundation of Ministry of Education of China under Grant No. 15YJCZH088, National Nature Science Foundation of China under Grant Nos. 61272020 and 61370185, and Natural Science Foundation of Jiangxi Province under Grant No. 20151BAB217008.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical standards
All procedures performed in studies involving human participants were in accordance with the ethical standards of the institutional and/or national research committee and with the 1964 Helsinki Declaration and its later amendments or comparable ethical standards.
Human and animal rights statement
This article does not contain any studies with animals performed by any of the authors
Informed consent
Informed consent was obtained from all individual participants included in the study.
Additional information
Communicated by A. Di Nola.
Rights and permissions
About this article
Cite this article
Yu, F., Xia, X., Li, W. et al. Critical node identification for complex network based on a novel minimum connected dominating set. Soft Comput 21, 5621–5629 (2017). https://doi.org/10.1007/s00500-016-2303-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-016-2303-y