Abstract
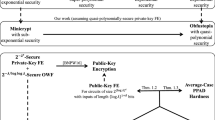
Functional encryption lies at the frontiers of the current research in cryptography; some variants have been shown sufficiently powerful to yield indistinguishability obfuscation (IO), while other variants have been constructed from standard assumptions such as LWE. Indeed, most variants have been classified as belonging to either the former or the latter category. However, one mystery that has remained is the case of secret-key functional encryption with an unbounded number of keys and ciphertexts. On the one hand, this primitive is not known to imply anything outside of minicrypt, the land of secret-key cryptography, but, on the other hand, we do no know how to construct it without the heavy hammers in obfustopia. In this work, we show that (subexponentially secure) secret-key functional encryption is powerful enough to construct indistinguishability obfuscation if we additionally assume the existence of (subexponentially secure) plain public-key encryption. In other words, secret-key functional encryption provides a bridge from cryptomania to obfustopia. On the technical side, our result relies on two main components. As our first contribution, we show how to use secret-key functional encryption to get “exponentially efficient indistinguishability obfuscation” (XIO), a notion recently introduced by Lin et al. (PKC’16) as a relaxation of IO. Lin et al. show how to use XIO and the LWE assumption to build IO. As our second contribution, we improve on this result by replacing its reliance on the LWE assumption with any plain public-key encryption scheme. Lastly, we ask whether secret-key functional encryption can be used to construct public-key encryption itself and therefore take us all the way from minicrypt to obfustopia. A result of Asharov and Segev (FOCS’15) shows that this is not the case under black-box constructions, even for exponentially secure functional encryption. We show, through a non-black-box construction, that subexponentially secure-key functional encryption indeed leads to public-key encryption. The resulting public-key encryption scheme, however, is at most quasi-polynomially secure, which is insufficient to take us to obfustopia.













Similar content being viewed by others
Notes
The above is a slightly oversimplified account of [51]. They also rely on LWE to deduce the existence of puncturable PRFs in \(\text {NC}^1\) and show their transformation starting from weakly succinct PKFE for functions in \(\text {NC}^1\). We avoid the reliance on puncturable PRFs in \(\text {NC}^1\) by constructing weakly succinct PKFE for functions with no depth restriction, at the expense of allowing the complexity of encryption to scale polynomially in the depth. This is still sufficient for [22, Section 3.2].
Extending this to functions with multi-bit output is then done, based on SXIO, using a transformation of [51]. Concretely, given an m-bit output function f(x) we consider a new single bit function \(g_f(x,i)\) that returns the ith bit of f(x). The function key is then derived for the boolean function \(g_f\). The new encryption algorithm, for message x, produces an \(\text {SXIO}\) obfuscation of a circuit that given \(i\in [m]\) uses the old encryption scheme to encrypt (m, i), deriving randomness using a puncturable PRF. The security of the construction is proven as in [51] based on a probabilistic IO argument [25]. (Mild) efficiency of the encryption then follows from the mild efficiency of the \(\text {SXIO}\) and \(\text {PKFE}\) with related (constant) compression factors.
Their aim was proving adaptive security, which is completely orthogonal to our aim. However, for entirely different reasons, the above goal is useful in both their work and ours.
Indeed, if the gates \(1,\ldots ,L\) are topologically sorted so that L is the output gate, then the pebbling can be made to place gray pebbles in according to this ordering, meaning that the first gray pebble is placed on gate \(L-1\) and then \(L-2\) and finally continuing down to 1. One minor difference between our version and the one in [39] is that the latter allows replacing a black pebble with a gray pebble at the output gate, whereas our does not. This only requires us to slightly modify the pebbling strategy to keep the pebble at the output gate black.
The restriction regarding fan-out is not stated explicitly in [24], but can always be achieved by blowing up the size and depth by a factor of at most O(1).
References
P. Ananth, Z. Brakerski, G. Segev, V. Vaikuntanathan, From selective to adaptive security in functional encryption, in R. Gennaro, M.J.B. Robshaw, editors, Advances in Cryptology – CRYPTO 2015, Part II, Santa Barbara, CA, USA, August 16–20, 2015. LNCS, vol. 9216 (Springer, Heidelberg, Germany, 2015), pp. 657–677
S. Agrawal, S. Gorbunov, V. Vaikuntanathan, H. Wee, Functional encryption: new perspectives and lower bounds, in R. Canetti, J.A. Garay, editors, Advances in Cryptology – CRYPTO 2013, Part II, Santa Barbara, CA, USA, August 18–22, 2013. LNCS, vol. 8043 (Springer, Heidelberg, Germany, 2013), pp. 500–518
P. Ananth, A. Jain, Indistinguishability obfuscation from compact functional encryption, in R. Gennaro, M.J.B. Robshaw, editors, Advances in Cryptology – CRYPTO 2015, Part I, Santa Barbara, CA, USA, August 16–20, 2015. LNCS, vol. 9215 (Springer, Heidelberg, Germany, 2015), pp. 308–326
P. Ananth, A. Jain, A. Sahai, Indistinguishability obfuscation from functional encryption for simple functions. Cryptology ePrint Archive, Report 2015/730 (2015). http://eprint.iacr.org/2015/730.
P.V. Ananth, A. Sahai, Functional encryption for turing machines, in E. Kushilevitz, T. Malkin, editors, TCC 2016-A: 13th Theory of Cryptography Conference, Part I, Tel Aviv, Israel. LNCS, vol. 9562 (Springer, Heidelberg, Germany, January 10–13, 2016), pp. 125–153
G. Asharov, G. Segev, Limits on the power of indistinguishability obfuscation and functional encryption. SIAM J. Comput.45(6), 2117–2176 (2016)
P. Ananth, A. Sahai, Projective arithmetic functional encryption and indistinguishability obfuscation from degree-5 multilinear maps, in J.-S. Coron, J.B. Nielsen, editors, Advances in Cryptology – EUROCRYPT 2017, Part I, Paris, France, May 8–12, 2017. LNCS, vol. 10210 (Springer, Heidelberg, Germany), pp. 152–181
N. Bitansky, R. Canetti, S. Garg, J. Holmgren, A. Jain, H. Lin, R. Pass, S. Telang, V. Vaikuntanathan, Indistinguishability obfuscation for RAM programs and succinct randomized encodings. SIAM J. Comput.47(3), 1123–1210 (2018)
D. Boneh, C. Gentry, S. Gorbunov, S. Halevi, V/ Nikolaenko, G. Segev, V. Vaikuntanathan, D. Vinayagamurthy, Fully key-homomorphic encryption, arithmetic circuit ABE and compact garbled circuits, in P.Q. Nguyen, E. Oswald, editors, Advances in Cryptology – EUROCRYPT 2014, Copenhagen, Denmark, May 11–15, 2014. LNCS, vol. 8441 (Springer, Heidelberg, Germany, 2014), pp. 533–556
B. Barak, O. Goldreich, R. Impagliazzo, S. Rudich, A. Sahai, S/P. Vadhan, K. Yang. On the (im)possibility of obfuscating programs. JACM59(2), 6 (2012)
E. Boyle, S. Goldwasser, I. Ivan, Functional signatures and pseudorandom functions, in H. Krawczyk, editor, PKC 2014: 17th International Conference on Theory and Practice of Public Key Cryptography, Buenos Aires, Argentina, March 26–28, 2014. LNCS, vol. 8383 (Springer, Heidelberg, Germany, 2014), pp. 501–519
S. Badrinarayanan, D. Gupta, A. Jain, A. Sahai, Multi-input functional encryption for unbounded arity functions, in T. Iwata and J.H. Cheon, editors, Advances in Cryptology – ASIACRYPT 2015, Part I, Auckland, New Zealand, November 30–December 3, 2015. LNCS, vol. 9452 (Springer, Heidelberg, Germany, 2015), pp. 27–51
N. Bitansky, S. Garg, H. Lin, R. Pass, S. Telang, Succinct randomized encodings and their applications, in R.A. Servedio, R. Rubinfeld, editors, 47th Annual ACM Symposium on Theory of Computing, Portland, OR, USA, June 14–17, 2015. (ACM Press, 2015), pp. 439–448
M. Bellare, V.T. Hoang, P. Rogaway. Foundations of garbled circuits, in T. Yu, G. Danezis, V.D. Gligor, editors, ACM CCS 12: 19th Conference on Computer and Communications Security, Raleigh, NC, USA, October 16–18, 2012 (ACM Press, 2012), pp. 784–796
Z. Brakerski, A. Jain, I. Komargodski, A. Passelègue, D. Wichs, Non-trivial witness encryption and null-iO from standard assumptions, in SCN 18: 11th International Conference on Security in Communication Networks. LNCS (Springer, Heidelberg, Germany, 2018), pp. 425–441
Z. Brakerski, I. Komargodski, G. Segev, Multi-input functional encryption in the private-key setting: stronger security from weaker assumptions. J. Cryptol.31(2), 434–520 (April 2018)
N. Bitansky, H. Lin, O. Paneth, On removing graded encodings from functional encryption, in J.-S. Coron, J.B. Nielsen, editors, Advances in Cryptology – EUROCRYPT 2017, Part II, Paris, France, 2017, May 8–12, 2017. LNCS, vol. 10211 (Springer, Heidelberg, Germany, 2017), pp. 3–29
D. Boneh, K. Lewi, M. Raykova, A. Sahai, M. Zhandry, J. Zimmerman, Semantically secure order-revealing encryption: multi-input functional encryption without obfuscation, in E. Oswald, M. Fischlin, editors, Advances in Cryptology – EUROCRYPT 2015, Part II, Sofia, Bulgaria, April 26–30, 2015. LNCS, vol. 9057 (Springer, Heidelberg, Germany, 2015), pp. 563–594
M. Bellare, A. O’Neill, Semantically-secure functional encryption: Possibility results, impossibility results and the quest for a general definition, in M. Abdalla, C. Nita-Rotaru, R. Dahab, editors, CANS 13: 12th International Conference on Cryptology and Network Security, Paraty, Brazil, November 20–22, 2013. LNCS, vol. 8257 (Springer, Heidelberg, Germany, 2013), pp. 218–234
Z. Brakerski, G. Segev, Function-private functional encryption in the private-key setting. J. Cryptol.31(1), 202–225 (January 2018)
D. Boneh, A. Sahai, B. Waters, Functional encryption: definitions and challenges, in Y. Ishai, editor, TCC 2011: 8th Theory of Cryptography Conference, Providence, RI, USA, March 28–30, 2011. LNCS, vol. 6597 (Springer, Heidelberg, Germany, 2011), pp. 253–273
N. Bitansky, V. Vaikuntanathan, Indistinguishability obfuscation from functional encryption. JACM65(6), 39:1–39:37 (2018)
D. Boneh, B. Waters, Constrained pseudorandom functions and their applications, in K. Sako, P. Sarkar, editors, Advances in Cryptology – ASIACRYPT 2013, Part II, Bengalore, India, December 1–5, 2013. LNCS, vol. 8270 (Springer, Heidelberg, Germany, 2013), pp. 280–300
S.A. Cook, H. James Hoover, A depth-universal circuit. SIAM J. Comput.14(4), 833–839 (1985)
R. Canetti, H. Lin, S. Tessaro, V. Vaikuntanathan, Obfuscation of probabilistic circuits and applications, in Y. Dodis, J.B. Nielsen, editors, TCC 2015: 12th Theory of Cryptography Conference, Part II, Warsaw, Poland, March 23–25, 2015. LNCS, vol. 9015 (Springer, Heidelberg, Germany, 2015), pp. 468–497
A. De Caro, V. Iovino, A. Jain, A. O’Neill, O. Paneth, G. Persiano, On the achievability of simulation-based security for functional encryption, in R. Canetti, J.A. Garay, editors, Advances in Cryptology – CRYPTO 2013, Part II, Santa Barbara, CA, USA, August 18–22, 2013. LNCS, vol. 8043 (Springer, Heidelberg, Germany, 2013), pp. 519–535
S. Goldwasser, S. Dov Gordon, V. Goyal, A. Jain, J. Katz, F.-H. Liu, A. Sahai, E. Shi, H.-S. Zhou, Multi-input functional encryption, in P.Q. Nguyen, E. Oswald, editors, Advances in Cryptology – EUROCRYPT 2014, Copenhagen, Denmark, May 11–15, 2014. LNCS, vol. 8441 (Springer, Heidelberg, Germany, 2014), pp. 578–602
S. Garg, C. Gentry, S. Halevi, M. Raykova, A. Sahai, B. Waters, Candidate indistinguishability obfuscation and functional encryption for all circuits. SIAM J. Comput.45(3), 882–929 (2016)
S. Garg, C. Gentry, S. Halevi, M. Zhandry, Functional encryption without obfuscation, in E. Kushilevitz and T. Malkin, editors, TCC 2016-A: 13th Theory of Cryptography Conference, Part II, Tel Aviv, Israel, January 10–13, 2016, LNCS, vol. 9563 (Springer, Heidelberg, Germany, 2016), pp. 480–511
O. Goldreich, S. Goldwasser, S. Micali, How to construct random functions. JACM33(4), 792–807 (1986)
S. Garg, C. Gentry, A. Sahai, B. Waters, Witness encryption and its applications, in D. Boneh, T. Roughgarden, J. Feigenbaum, editors, 45th Annual ACM Symposium on Theory of Computing, Palo Alto, CA, USA, June 1–4, 2013 (ACM Press, 2013), pp. 467–476
V. Goyal, A. Jain, V. Koppula, A. Sahai, Functional encryption for randomized functionalities, in Y. Dodis and J.B. Nielsen, editors, TCC 2015: 12th Theory of Cryptography Conference, Part II, Warsaw, Poland, March 23–25, 2015. LNCS, vol. 9015 (Springer, Heidelberg, Germany, 2015), pp. 325–351
S. Goldwasser, Y.T. Kalai, R.A. Popa, V. Vaikuntanathan, N. Zeldovich, Reusable garbled circuits and succinct functional encryption, in D. Boneh, T. Roughgarden, J. Feigenbaum, editors, 45th Annual ACM Symposium on Theory of Computing, Palo Alto, CA, USA, June 1–4, 2013 (ACM Press, 2013), pp. 555–564
S. Garg, O. Pandey, A. Srinivasan, Revisiting the cryptographic hardness of finding a nash equilibrium, in M. Robshaw. J. Katz, editors, Advances in Cryptology – CRYPTO 2016, Part II, Santa Barbara, CA, USA, August 14–18, 2016. LNCS, vol. 9815 (Springer, Heidelberg, Germany, 2016), pp. 579–604
S. Garg, O. Pandey, A. Srinivasan, M. Zhandry. Breaking the sub-exponential barrier in obfustopia, in J.-S. Coron, J.B. Nielsen, editors, Advances in Cryptology – EUROCRYPT 2017, Part II, Paris, France, May 8–12, 2017. LNCS, vol. 10211 (Springer, Heidelberg, Germany, 2017), pp. 156–181
S. Garg, A. Srinivasan, Single-key to multi-key functional encryption with polynomial loss, in M. Hirt, A.D. Smith, editors, TCC 2016-B: 14th Theory of Cryptography Conference, Part II. Beijing, China, October 31–November 3, 2016. LNCS, vol. 9986 (Springer, Heidelberg, Germany, 2016), pp. 419–442
S. Gorbunov, V. Vaikuntanathan, H. Wee, Functional encryption with bounded collusions via multi-party computation, in R. Safavi-Naini, R. Canetti, editors, Advances in Cryptology – CRYPTO 2012, Santa Barbara, CA, USA, August 19–23, 2012. LNCS, vol. 7417 (Springer, Heidelberg, Germany, 2012), pp. 162–179
S. Gorbunov, V. Vaikuntanathan, H. Wee, Predicate encryption for circuits from LWE, in R. Gennaro, M.J.B. Robshaw, editors, Advances in Cryptology – CRYPTO 2015, Part II, Santa Barbara, CA, USA, August 16–20, 2015. LNCS, vol. 9216 (Springer, Heidelberg, Germany, 2015), pp. 503–523
B. Hemenway, Z. Jafargholi, R. Ostrovsky, A. Scafuro, D. Wichs, Adaptively secure garbled circuits from one-way functions, in M. Robshaw, J. Katz, editors, Advances in Cryptology – CRYPTO 2016, Part III, Santa Barbara, CA, USA, August 14–18, 2016. LNCS, vol. 9816 (Springer, Heidelberg, Germany, 2016), pp. 149–178
R. Impagliazzo, A personal view of average-case complexity, in Proceedings of the Tenth Annual Structure in Complexity Theory Conference, Minneapolis, Minnesota, USA, June 19–22, 1995 (IEEE Computer Society, 1995), pp. 134–147
F. Kitagawa, Ryo Nishimaki, Keisuke Tanaka, From single-key to collusion-resistant secret-key functional encryption by leveraging succinctness. Cryptology ePrint Archive, Report 2017/638 (2017). http://eprint.iacr.org/2017/638.
F. Kitagawa, R. Nishimaki, K. Tanaka, Indistinguishability obfuscation for all circuits from secret-key functional encryption. Cryptology ePrint Archive, Report 2017/361 (2017). http://eprint.iacr.org/2017/361.
F. Kitagawa, R. Nishimaki, K. Tanaka, Obfustopia built on secret-key functional encryption, in J.B. Nielsen, V. Rijmen, editors, Advances in Cryptology – EUROCRYPT 2018, Part II. LNCS, vol. 10821 (Springer, Heidelberg, Germany, 2018), pp. 603–648
F. Kitagawa, R. Nishimaki, K. Tanaka, Simple and generic constructions of succinct functional encryption, in M. Abdalla, R. Dahab, editors, Advances in Cryptology – PKC 2018, Part II. LNCS, vol. 10770 (Springer, Heidelberg, Germany, 2018), pp. 187–217
A. Kiayias, S. Papadopoulos, N. Triandopoulos, T. Zacharias, Delegatable pseudorandom functions and applications, in A.-R. Sadeghi, V.D. Gligor, M. Yung, editors, ACM CCS 13: 20th Conference on Computer and Communications Security, Berlin, Germany, November 4–8, 2013 (ACM Press, 2013), pp. 669–684
I. Komargodski, G. Segev, From minicrypt to obfustopia via private-key functional encryption, in J.-S. Coron, J. B. Nielsen, editors, Advances in Cryptology – EUROCRYPT 2017, Part I, Paris, France, May 8–12, 2017. LNCS, vol. 10210 (Springer, Heidelberg, Germany, 2017), pp. 122–151
I. Komargodski, G. Segev, E. Yogev. Functional encryption for randomized functionalities in the private-key setting from minimal assumptions. Journal of Cryptology31(1), 60–100 (2018)
H. Lin, Indistinguishability obfuscation from constant-degree graded encoding schemes, in M. Fischlin, J.-S. Coron, editors, Advances in Cryptology – EUROCRYPT 2016, Part I, Vienna, Austria, May 8–12, 2016. LNCS, vol. 9665 (Springer, Heidelberg, Germany, 2016), pp. 28–57
H. Lin, Indistinguishability obfuscation from SXDH on 5-linear maps and locality-5 PRGs, in J. Katz, H. Shacham, editors, Advances in Cryptology – CRYPTO 2017, Part I, Santa Barbara, CA, USA, August 20–24, 2017. LNCS, vol. 10401 (Springer, Heidelberg, Germany, 2017), pp. 599–629
B. Li, D. Micciancio, Compactness vs collusion resistance in functional encryption, in Martin Hirt and Adam D. Smith, editors, TCC 2016-B: 14th Theory of Cryptography Conference, Part II, Beijing, China, October 31–November 3, 2016. LNCS, vol. 9986 (Springer, Heidelberg, Germany, 2016), pp. 443–468
H. Lin, R. Pass, K. Seth, S. Telang, Indistinguishability obfuscation with non-trivial efficiency, in C.-M. Cheng, K.-M. Chung, G. Persiano, B.-Y. Yang, editors, PKC 2016: 19th International Conference on Theory and Practice of Public Key Cryptography, Part II, Taipei, Taiwan, March 6–9, 2016. LNCS, vol. 9615 (Springer, Heidelberg, Germany, 2016), pp. 447–462
H. Lin, R. Pass, K. Seth, S. Telang, Output-compressing randomized encodings and applications, in E. Kushilevitz, T. Malkin, editors, TCC 2016-A: 13th Theory of Cryptography Conference, Part I, Tel Aviv, Israel, January 10–13, 2016. LNCS, vol. 9562 (Springer, Heidelberg, Germany, 2016), pp. 96–124
H. Lin, S. Tessaro. Indistinguishability obfuscation from trilinear maps and block-wise local PRGs, in J. Katz, H. Shacham, editors, Advances in Cryptology – CRYPTO 2017, Part I, Santa Barbara, CA, USA, August 20–24, 2017. LNCS, vol. 10401 (Springer, Heidelberg, Germany, 2017), pp. 630–660
H. Lin, V. Vaikuntanathan, Indistinguishability obfuscation from DDH-like assumptions on constant-degree graded encodings, in I. Dinur, editor, 57th Annual Symposium on Foundations of Computer Science, New Brunswick, NJ, USA, October 9–11, 2016 (IEEE Computer Society Press, 2016), pp. 11–20
A. O’Neill, Definitional issues in functional encryption. Cryptology ePrint Archive, Report 2010/556 (2010). http://eprint.iacr.org/2010/556
O. Regev, On lattices, learning with errors, random linear codes, and cryptography. JACM56(6), 34:1–34:40 (2009)
A. Shamir, Identity-based cryptosystems and signature schemes, in G. R. Blakley and David Chaum, editors, Advances in Cryptology – CRYPTO’84, Santa Barbara, CA, USA, August 19–23, 1984. LNCS, vol. 196 (Springer, Heidelberg, Germany, 1984), pp. 47–53
A. Sahai, H. Seyalioglu, Worry-free encryption: functional encryption with public keys, in E. Al-Shaer, A.D. Keromytis, V. Shmatikov, editors, ACM CCS 10: 17th Conference on Computer and Communications Security, Chicago, Illinois, USA, October 4–8, 2010 (ACM Press, 2010), pp. 463–472
A. Sahai, B. Waters, How to use indistinguishability obfuscation: deniable encryption, and more, in D.B. Shmoys, editor, 46th Annual ACM Symposium on Theory of Computing, New York, NY, USA, May 31–June 3, 2014 (ACM Press, 2014), pp. 475–484
B. Waters, A punctured programming approach to adaptively secure functional encryption, in R. Gennaro, M.J.B. Robshaw, editors, Advances in Cryptology – CRYPTO 2015, Part II, Santa Barbara, CA, USA, August 16–20, 2015. LNCS, vol. 9216 (Springer, Heidelberg, Germany, 2015), pp. 678–697
A.C.-C. Yao, Protocols for secure computations (extended abstract), in 23rd Annual Symposium on Foundations of Computer Science, Chicago, Illinois, November 3–5, 1982 (IEEE Computer Society Press, 1982) pp. 160–164
Acknowledgements
We thank Vinod Vaikuntanathan and Hoeteck Wee for valuable discussions.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Manoj Prabhakaran.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Nir Bitansky: Member of the Check Point Institute of Information Security. Supported by the Alon Young Faculty Fellowship, by Len Blavatnik and the Blavatnik Family foundation, and an ISF Grant 18/484. This work was done in part while the author was at MIT and was supported by the DARPA and ARO under Contract No. W911NF-15-C-0236. Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the DARPA and ARO.
Ryo Nishimaki: This work was done in part while the author was visiting Northeastern University.
Alain Passelègue: This work was done in part while the author was visiting Northeastern University. Research supported in part from a DARPA/ARL SAFEWARE award, NSF Frontier Award 1413955, NSF Grants 1619348, 1228984, 1136174, and 1065276, BSF Grant 2012378, a Xerox Faculty Research Award, a Google Faculty Research Award, an equipment grant from Intel, and an Okawa Foundation Research Grant. This material is based upon work supported by the Defense Advanced Research Projects Agency through the ARL under Contract W911NF-15-C-0205. The views expressed are those of the authors and do not reflect the official policy or position of the Department of Defense, the National Science Foundation, or the U.S. Government.
Daniel Wichs: Supported in part by NSF Grants CNS-1347350, CNS-1314722, CNS-1413964.
Rights and permissions
About this article
Cite this article
Bitansky, N., Nishimaki, R., Passelègue, A. et al. From Cryptomania to Obfustopia Through Secret-Key Functional Encryption. J Cryptol 33, 357–405 (2020). https://doi.org/10.1007/s00145-019-09337-9
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00145-019-09337-9