Abstract
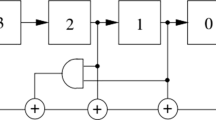
The increasing importance of security of multimedia data has prompted greater attention towards secure image encryption algorithms. In this paper, the authors propose a highly secure encryption algorithm with permutation-substitution architecture. In the permutation step, image pixels of the plain image are shuffled using Linear Feedback Shift Register (LFSR). The output of this step is an intermediary cipher image which is of the same size as that of the plain image. In the substitution step, sequence of random numbers is generated using the RC4 key stream generator which is XORed with the pixel value of the intermediary cipher image to produce the final cipher image. Experimental results and security analysis of the proposed scheme show that the proposed scheme is efficient and secure.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Ayinala, M., Parhi, K.K.: High-speed parallel architectures for linear feedback shift registers. IEEE Trans. Sig. Process. 59(9), 4459–4469 (2011)
Fu, C., Chen, J.J., Zou, H., Meng, W.H., Zhan, Y.F., Yu, Y.W.: A chaos-based digital image encryption scheme with an improved diffusion strategy. Opt. Express 20(3), 2363–2378 (2012)
Kwok, S.H.M., Lam, E.Y.: Effective uses of fpgas for brute-force attack on rc4 ciphers. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 16(8), 1096–1100 (2008)
Lamba, C.S.: Design and analysis of stream cipher for network security. In: Communication Software and Networks, 2010. ICCSN’10. Second International Conference on, pp. 562–567 (2010)
Lima, J.B., Lima, E.A.O., Madeiro, F.: Image encryption based on the finite field cosine transform. Sig. Process. Image Commun. 28(10), 1537–1547 (2013)
Mirzaei, O., Yaghoobi, M., Irani, H.: A new image encryption method: parallel sub-image encryption with hyper chaos. Nonlinear Dyn. 67(1), 557–566 (2012)
Mondal, B., Priyadarshi, A., Hariharan, D.: An improved cryptography scheme for secure image communication. Int. J. Comput. Appl. 67(18), 23–27 (2013). Published by Foundation of Computer Science, New York, USA
Mondal, B., Singh, S.K.: A highly secure steganography scheme for secure communication. Int. Conf. Comput. Commun. Adv. (IC3A), (2013)
Tawalbeh, L., Mowafi, M., Aljoby, W.: Use of elliptic curve cryptography for multimedia encryption. IET Inf. Secur. 7(2), 67–74 (2013)
Wang, L.-T., McCluskey, E.J.: Linear feedback shift register design using cyclic codes. IEEE Trans. Comput. 37(10), 1302–1306 (1988)
Wang, X.-Y., Wang, T.: A novel algorithm for image encryption based on couple chaotic systems. Int. J. Mod. Phys. B 26(30), 1250175 (2012)
Wang, Y., Wong, K.-W., Liao, X., Chen, G.: A new chaos-based fast image encryption algorithm. Appl. Soft Comput. 11(1), 514–522 (2011)
Weerasinghe, T.D.B.: An effective RC4 stream cipher. In: Industrial and Information Systems (ICIIS), 2013 8th IEEE International Conference on, pp. 69–74, Dec 2013
Wong, K.-W., Kwok, B.S.-H., Law, W.-S.: A fast image encryption scheme based on chaotic standard map. Phys. Lett. A 372(15), 2645–2652 (2008)
Ye, G.: Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recogn. Lett. 31(5), 347–354 (2010)
Zadeh, A.A., Heys, H.M.: Simple power analysis applied to nonlinear feedback shift registers. IET Inf. Secur. 8(3), 188–198 (2014)
Zhu, C.: A novel image encryption scheme based on improved hyperchaotic sequences. Opt. Commun. 285(1), 29–37 (2012)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer India
About this paper
Cite this paper
Mondal, B., Sinha, N., Mandal, T. (2016). A Secure Image Encryption Algorithm Using LFSR and RC4 Key Stream Generator. In: Nagar, A., Mohapatra, D., Chaki, N. (eds) Proceedings of 3rd International Conference on Advanced Computing, Networking and Informatics. Smart Innovation, Systems and Technologies, vol 43. Springer, New Delhi. https://doi.org/10.1007/978-81-322-2538-6_24
Download citation
DOI: https://doi.org/10.1007/978-81-322-2538-6_24
Published:
Publisher Name: Springer, New Delhi
Print ISBN: 978-81-322-2537-9
Online ISBN: 978-81-322-2538-6
eBook Packages: EngineeringEngineering (R0)