Abstract
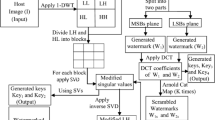
Digital watermarking techniques have been developed to protect the copyright of multimedia objects such as text, audio, video. In this paper, we propose a digital watermarking algorithm with a gray image based on two dimensions discrete cosine transform (DCT) and singular value decomposition (SVD) for robust watermarking of digital images in order to protect digital media copyright. The performance of hybrid watermarking technique has presented, including imperceptibility (such as PSNR, NC) and robustness (such as Filtering, Gaussian noise, Rotation and Salt and Pepper). Experimental results demonstrate that the proposed scheme shows superior performance in the presence of signal processing attracks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Rey, C., Dugelay, J.-L.: A Survey of Watermarking Algorithms for Image Authentication. EURASIP Journal on Applied Signal Processing 2000(6), 613–621 (2002)
Voyatzis, G., Nikolaidis, N., Pitas, I.: Digital watermarking: An overview. In: Ninth European Signal Processing Conference, Rhodes, Greece, September 8-11, pp. 9–12. Typorama Editions (1998)
Potdar, V., Han, S., Chang, E.: A survey of digital image watermarking techniques. In: Proceeding of 3rd IEEE-International Conference on Industrial Informatics, Frontier Technologies for the Future of Industry and Business, Perth, WA, pp. 709–716 (August 10, 2005)
Harish, N.J., Kumar, B.B.S., Kusagur, A.: Hybrid Robust Watermarking Technique Based on DWT, DCT and SVD. International Journal of Advanced Electrical and Electronics Engineering 2(5) (2013)
Cox, I.J., Kilian, J., Leighton, F.T., Shamoon, T.: Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Processing 6, 1673–1687 (1997)
Nikolaidis, N., Pitas, I.: Copyright protection of images using robust digital signatures. In: Proc. ICASSP, vol. 4, pp. 2168–2171 (May 1996)
Nikolaids, N., Pitas, I.: Robust image watermarking in the spatial domain. Signal Process 66(3), 385–403 (1998)
Barni, M., Bartolini, F., Cappellini, V., Piva, A.: A DCT-domain system for robust image watermarking. Signal Process. 66(3), 357–372 (1998)
Zhao, J., Koch, E., Luo, C.: Digital watermarking in business today and tomorrow. Commun. ACM 41(7), 67–72 (1998)
Zeng, W.: Digital watermarking and data hiding: Technologies and applications. In: Proc. ICISAS, vol. 3, pp. 223–229 (1998)
Craver, S., Memon, N., Yeo, B.L., Yeung, M.M.: Resolving rightful ownerships with invisible watermarking techniques: Limitations, attacks and implications. IEEE J. Select. Areas Commun. 16(4), 573–586 (1998)
Qiao, L.T., Nahrstedt, K.: Watermarking schemes and protocols for protecting rightful ownership and customer’s rights. J. Vis. Commun. Image Represent. 9(3), 194–210 (1998)
Xie, L., Arce, G.R., Bash, A., Basch, E.B.: Image enhancement toward soft image authentication. In: Proc. IEEE Int. Cof. Mutimedea and Expo. (ICME), vol. 1, pp. 497–500 (2000)
Fridirich, J.: Image watermarking for tamper detection. In: Proc. IEEE Int. Conf. Image Processing (ICIP), vol. 2(2), pp. 404–408 (1998)
Lin, C.-Y., Chang, S.-F.: Seme-fragile watermarking for authenticating JPEG visual content. In: Proc. SPIE Int. Conf. Security and Watermarking of Multimedia Contents II, vol. 397(l), pp. 140–151 (2000)
Miller, M.L., Cox, I.J., Linnartz, J.P., Kalker, T.: A Review of Watermarking Principles and Practices. In: Parhi, K.K., Nishitani, T. (eds.) Digital Signal Processing in Multimedia Systems. Marcell Dekker Inc. (1999)
Wu, M., Liu, B.: Watermarking for image authentication. In: Proc. IEEE Int. Conf. Image Processing (ICIP), vol. 2, pp. 437–441 (2000)
Kundur, D., Hatzinakos, D.: Digital watermarking for telltale tamper proofing and authentication. Proc. IEEE 87, 1 167–1 180 (1999)
Sun, R., Sun, H., Yao, T.: A SVD and quantization based semi-fragile watermarking for image authentication. In: Proc. Int. Conf. Signal Processing (ICSP), vol. 2, pp. 26–30 (2002)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Islam, M.S., Chong, U. (2015). Performance of a Hybrid DCT SVD Visually Imperceptible Digital Watermarking against Signal Processing Attacks. In: Park, J., Stojmenovic, I., Jeong, H., Yi, G. (eds) Computer Science and its Applications. Lecture Notes in Electrical Engineering, vol 330. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-45402-2_2
Download citation
DOI: https://doi.org/10.1007/978-3-662-45402-2_2
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-662-45401-5
Online ISBN: 978-3-662-45402-2
eBook Packages: EngineeringEngineering (R0)