Abstract
In contrast to classical signature schemes, such as RSA or ECDSA signatures, the lattice-based signature scheme ring-TESLA is expected to be resistant even against quantum adversaries. Due to a recent key recovery from a lattice-based implementation, it becomes clear that cache side channels are a serious threat for lattice-based implementations. In this article, we analyze an existing implementation of ring-TESLA against cache side channels. To reduce the effort for manual code inspection, we selectively employ automated program analysis. The leakage bounds we compute with program analysis are sound overapproximations of cache-side-channel leakage. We detect four cache-side-channel vulnerabilities in the implementation of ring-TESLA. Since two vulnerabilities occur in implementations of techniques common to lattice-based schemes, they are also interesting beyond ring-TESLA. Finally, we show how the detected vulnerabilities can be mitigated effectively.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
We analyze an implementation of ring-TESLA despite an error that was detected in its security reduction, since we expect that reductions given for its predecessor TESLA [14, 15] will be applicable to ring-TESLA as well. Hence, we consider it to be a good candidate for practical applications that require post-quantum signatures.
- 2.
Security properties of schemes over standard lattices (like TESLA) often hold for corresponding schemes over ideal lattices (like ring-TESLA), e.g., the security reduction from [11] holds for the standard-lattice variant and for the ideal-lattice variant.
- 3.
The instructions 0xF7/3 and 0x99 were integrated independently but concurrently into a different version of CacheAudit by Doychev [27].
- 4.
We also investigated FIFO (first in first out) replacement. The leakage bounds (on the unmitigated implementation) are less than 10 bit lower than under LRU.
- 5.
Treating the message as secret is overly conservative in a signature scenario. We investigated the effect of fixing the message to all ‘0’s and obtained the same leakage bounds as for an uninitialized message in the unmitigated implementation.
- 6.
Throughout the article, we round bounds up to one decimal place and truncate the bounds to \(3*\text {PARAM\_N}*32\text {bit}=49152\text {bit}\), i.e., the maximum size of the key.
- 7.
The analysis of the other subroutines of
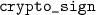 can be found in the corresponding technical report under http://eprint.iacr.org/2017/951.
can be found in the corresponding technical report under http://eprint.iacr.org/2017/951. - 8.
To simplify our explanation we assume that the corresponding cache line starts with
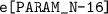 and ends with
and ends with  .
. - 9.
Our arguments hold also true if we assume that
 is not loaded in the cache. In the ring-TESLA implementation, it is already loaded in line 18 in Listing 3.1.
is not loaded in the cache. In the ring-TESLA implementation, it is already loaded in line 18 in Listing 3.1.
References
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
National Institute of Standards and Technology (NIST): Post-quantum project (2016). https://pqcrypto2016.jp/data/pqc2016_nist_announcement.pdf. Accessed 23 May 2017
Yarom, Y., Genkin, D., Heninger, N.: CacheBleed: a timing attack on OpenSSL constant time RSA. In: Gierlichs, B., Poschmann, A.Y. (eds.) CHES 2016. LNCS, vol. 9813, pp. 346–367. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53140-2_17
Acıiçmez, O., Koç, Ç.K.: Trace-driven cache attacks on AES. Cryptology ePrint Archive, Report 2006/138
Osvik, D.A., Shamir, A., Tromer, E.: Cache attacks and countermeasures: the case of AES. In: Pointcheval, D. (ed.) CT-RSA 2006. LNCS, vol. 3860, pp. 1–20. Springer, Heidelberg (2006). https://doi.org/10.1007/11605805_1
Bernstein, D.J.: Cache-timing attacks on AES. Technical report, University of Illinois at Chicago (2005)
Oder, T., Schneider, T., Pöppelmann, T., Güneysu, T.: Practical CCA2-secure and masked ring-LWE implementation. Cryptology ePrint Archive, Report 2016/1109 (2016)
Pessl, P.: Analyzing the shuffling side-channel countermeasure for lattice-based signatures. In: Dunkelman, O., Sanadhya, S.K. (eds.) INDOCRYPT 2016. LNCS, vol. 10095, pp. 153–170. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-49890-4_9
Saarinen, M.J.O.: Arithmetic coding and blinding countermeasures for lattice signatures. Cryptology ePrint Archive, Report 2016/276 (2016)
Reparaz, O., Roy, S.S., Vercauteren, F., Verbauwhede, I.: A masked ring-LWE implementation. Cryptology ePrint Archive, Report 2015/724 (2015)
Ducas, L., Durmus, A., Lepoint, T., Lyubashevsky, V.: Lattice signatures and bimodal Gaussians. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8042, pp. 40–56. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40041-4_3
Groot Bruinderink, L., Hülsing, A., Lange, T., Yarom, Y.: Flush, gauss, and reload - a cache attack on the BLISS lattice-based signature scheme. In: CHES, pp. 323–345 (2016)
Akleylek, S., Bindel, N., Buchmann, J., Krämer, J., Marson, G.A.: An efficient lattice-based signature scheme with provably secure instantiation. In: Pointcheval, D., Nitaj, A., Rachidi, T. (eds.) AFRICACRYPT 2016. LNCS, vol. 9646, pp. 44–60. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-31517-1_3
Alkim, E., Bindel, N., Buchmann, J., Dagdelen, Ö., Eaton, E., Gutoski, G., Krämer, J., Pawlega, F.: Revisiting TESLA in the quantum random oracle model. In: PQCrypto, pp. 143–162 (2017)
Bai, S., Galbraith, S.D.: An improved compression technique for signatures based on learning with errors. In: Benaloh, J. (ed.) CT-RSA 2014. LNCS, vol. 8366, pp. 28–47. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-04852-9_2
Doychev, G., Köpf, B., Mauborgne, L., Reineke, J.: CacheAudit: a tool for the static analysis of cache side channels. ACM TISSEC 18(1), 4:1–4:32 (2015)
Mantel, H., Weber, A., Köpf, B.: A systematic study of cache side channels across AES implementations. In: ESSoS, pp. 213–230 (2017)
Doychev, G., Köpf, B.: Rigorous analysis of software countermeasures against cache attacks. In: PLDI, pp. 406–421 (2017)
Barreto, P.S.L.M., Longa, P., Naehrig, M., Ricardini, J.E., Zanon, G.: Sharper ring-LWE signatures. Cryptology ePrint Archive, Report 2016/1026 (2016)
Abel, A., Reineke, J.: Reverse engineering of cache replacement policies in Intel microprocessors and their evaluation. In: ISPASS, pp. 141–142 (2014)
Smith, G.: On the foundations of quantitative information flow. In: de Alfaro, L. (ed.) FoSSaCS 2009. LNCS, vol. 5504, pp. 288–302. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-00596-1_21
Shannon, C.E.: A mathematical theory of communication. Bell Syst. Tech. J. 27(3), 379–423, 623–656 (1948)
Köpf, B., Smith, G.: Vulnerability bounds and leakage resilience of blinded cryptography under timing attacks. In: CSF, pp. 44–56 (2010)
Alvim, M.S., Chatzikokolakis, K., Palamidessi, C., Smith, G.: Measuring information leakage using generalized gain functions. In: CSF, pp. 265–279 (2012)
Yarom, Y., Falkner, K.: FLUSH+RELOAD: a high resolution, low noise, L3 cache side-channel attack. In: USENIX Security, pp. 719–732 (2014)
Cousot, P., Cousot, R.: Abstract interpretation: a unified lattice model for static analysis of programs by construction or approximation of fixpoints. In: POPL, pp. 238–252 (1977)
Doychev, G.: Commit f063813faa548da9bfb11dea9ff6fe39c0f11626: adding support for CDQ and NEG instructions. https://github.com/cacheaudit/cacheaudit/commit/f063813faa548da9bfb11dea9ff6fe39c0f11626 (2016). Accessed 23 May 2017
Degenbaev, U.: Formal specification of the x86 instruction set architecture. Ph.D. thesis, Universität des Saarlandes (2012)
Intel Corporation: Intel® 64 and IA-32 Architectures Optimization Reference Manual. Order Number: 248966–032 (2016)
Ducas, L., Nguyen, P.Q.: Learning a zonotope and more: cryptanalysis of NTRUsign countermeasures. In: Wang, X., Sako, K. (eds.) ASIACRYPT 2012. LNCS, vol. 7658, pp. 433–450. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34961-4_27
Nguyen, P.Q., Regev, O.: Learning a parallelepiped: cryptanalysis of GGH and NTRU signatures. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 271–288. Springer, Heidelberg (2006). https://doi.org/10.1007/11761679_17
Molnar, D., Piotrowski, M., Schultz, D., Wagner, D.: The program counter security model: automatic detection and removal of control-flow side channel attacks. In: Won, D.H., Kim, S. (eds.) ICISC 2005. LNCS, vol. 3935, pp. 156–168. Springer, Heidelberg (2006). https://doi.org/10.1007/11734727_14
Mantel, H., Starostin, A.: Transforming out timing leaks, more or less. In: Pernul, G., Ryan, P.Y.A., Weippl, E. (eds.) ESORICS 2015. LNCS, vol. 9326, pp. 447–467. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-24174-6_23
Zhang, J., Zhang, Z., Ding, J., Snook, M., Dagdelen, Ö.: Authenticated key exchange from ideal lattices. In: EUROCRYPT, pp. 719–751 (2015)
Buchmann, J., Göpfert, F., Güneysu, T., Oder, T., Pöppelmann, T.: High-performance and lightweight lattice-based public-key encryption. In: IoTPTS, pp. 2–9 (2016)
Acknowledgements
We thank the anonymous reviewers for their helpful suggestions and Sedat Akleylek for contributing to our modifications of the original ring-TESLA implementation. This work has been partially funded by the DFG as part of projects P1 and E3 within the CRC 1119 CROSSING.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this paper
Cite this paper
Bindel, N., Buchmann, J., Krämer, J., Mantel, H., Schickel, J., Weber, A. (2018). Bounding the Cache-Side-Channel Leakage of Lattice-Based Signature Schemes Using Program Semantics. In: Imine, A., Fernandez, J., Marion, JY., Logrippo, L., Garcia-Alfaro, J. (eds) Foundations and Practice of Security. FPS 2017. Lecture Notes in Computer Science(), vol 10723. Springer, Cham. https://doi.org/10.1007/978-3-319-75650-9_15
Download citation
DOI: https://doi.org/10.1007/978-3-319-75650-9_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-75649-3
Online ISBN: 978-3-319-75650-9
eBook Packages: Computer ScienceComputer Science (R0)


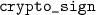 can be found in the corresponding technical report under
can be found in the corresponding technical report under 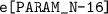 and ends with
and ends with  .
. is not loaded in the cache. In the ring-TESLA implementation, it is already loaded in line 18 in Listing 3.1.
is not loaded in the cache. In the ring-TESLA implementation, it is already loaded in line 18 in Listing 3.1.