Abstract
Fraud detection and prevention is a big data challenge, especially as business moves online. Patterns of internal or external fraud often lie in the massive amounts of unstructured machine data and log files generated by business applications and systems. Traditional fraud detection techniques rely on data collected from the user’s machine to ensure that transactions are originating from a trusted source. Such data can be altered and spoofed to fool the server and execute unauthorized transactions. Behavioral biometrics such as touch, keystroke, and mouse dynamics use measurements based on human action. Such measurements could be used to enrich the device/context signature used for fraud detection.
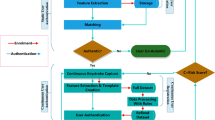
In this chapter, we propose a new framework for fraud detection based on behavioral biometric factors. The proposed model works on both of the security and performance factors. It increases the security of existing models by targeting man-in-the-middle and replay attacks and enhances the performance by incorporating mode data in the decision-making analysis.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Ahmed AAE, Traore I (2007) A new biometric technology based on mouse dynamics. IEEE Trans Dependable Secure Comput 4(3):165–179
Ahmed A, Traore I (2011) Dynamic sample size detection in continuous authentication using sequential sampling. In: Proceedings of annual computer security applications conference (ACSAC), 5–9 December 2011, Orlando, FL, USA
Ahmed AAE, Traore I (2014) Free text recognition of keystrokes. IEEE Trans Cybern 44(4):458–472
Bo C, Zhang L, Jung T, Han J, Li X, Wang Y (2014) Continuous user identification via touch and movement behavioral biometrics. In: IEEE international performance computing and communications conference (IPCCC), December 2014, pp 1–8
Deshmukh SP, Patil SH (2014) Credit card fraud detection using iris biometrics technique. Int J Sci Eng Res 5(7):131–137
Dowland P, Furnell S, Papadaki M (2002) Keystroke analysis as a method of advanced user authentication and response. In: Proceedings of the IFIP TC11 17th international conference on information security: visions and perspectives, 7–9 May 2002, pp 215–226
Frank M, Biedert R, Ma E, Martinovic I, Song D (2013) Touch analytics: on the applicability of touchscreen input as a behavioral biometric for continuous authentication. IEEE Trans Inf Forensics Secur 8(1):136–148
Gaurav J, Tyagi S, Ranjan J (2012) Smart card fraud prevention scheme using fingerprinting authentication. Int J Comput Sci Inf Technol 3:3059–3062
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this chapter
Cite this chapter
Awad, A. (2017). Collective Framework for Fraud Detection Using Behavioral Biometrics. In: Traoré, I., Awad, A., Woungang, I. (eds) Information Security Practices. Springer, Cham. https://doi.org/10.1007/978-3-319-48947-6_3
Download citation
DOI: https://doi.org/10.1007/978-3-319-48947-6_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-48946-9
Online ISBN: 978-3-319-48947-6
eBook Packages: EngineeringEngineering (R0)