Abstract
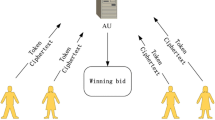
Due to the popularity of auction mechanisms in real-world applications and the increase in the awareness of securing private information, auctions are in dire need of bid-privacy protection. In this paper, we deliberately design a secure multi-unit sealed-bid first-price auction scheme, in which the auction is processed on the bidders’ encrypted bids by the server and the final output is only known by the auctioneer. As a result, neither the auctioneer nor the server can obtain the full information of the bidders. What’s more, the auctioneer can verify whether a winner pays its full payment in the auction. Finally, a comprehensive analysis on the performance of our auction mechanism is conducted.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Ausubel, L.M.: Auction theory for the new economy. In: Jones, D. (ed.) New Economy Handbook, ch. 6. Academic Press, San Diego (2003)
Chen, Z., Huang, L., Li, L., Yang, W., Miao, H., Tian, M., Wang, F.: Ps-trust: Provably secure solution for truthful double spectrum auctions. In: IEEE INFOCOM, pp. 1249–1257 (2014)
Hu, C., Liao, X., Cheng, X.: Verifiable multi-secret sharing based on LFSR sequences. Theor. Comput. Sci. 445, 52–62 (2012)
Hu, C., Liao, X., Xiao, D.: Secret image sharing based on chaotic map and chinese remainder theorem. Int. J. Wavelets Multiresolut. Inf. Process. 10(03), 1250023(1–18) (2012)
Hu, C., Zhang, F., Cheng, X., Liao, X., Chen, D.: Securing communications between external users and wireless body area networks. In: Proceedings of the 2nd ACM Workshop on Hot Topics on Wireless Network Security and Privacy, pp. 31–36. ACM (2013)
Hu, C., Zhang, F., Xiang, T., Li, H., Xiao, X., Huang, G.: A practically optimized implementation of attribute based cryptosystems. In: 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), pp. 197–204. IEEE (2014)
Hu, C., Zhang, N., Li, H., Cheng, X., Liao, X.: Body area network security: a fuzzy attribute-based signcryption scheme. IEEE J. Sel. Areas Commun. 31(9), 37–46 (2013)
Huang, Q., Tao, Y., Wu, F.: Spring: a strategy-proof and privacy preserving spectrum auction mechanism. In: IEEE INFOCOM, pp. 851–859, Turin, Italy, April 2013
Jing, T., Zhang, F., Ma, L., Li, W., Chen, X., Huo, Y.: Truthful online reverse auction with flexible preemption for access permission transaction in macro-femtocell networks. In: Ren, K., Liu, X., Liang, W., Xu, M., Jia, X., Xing, K. (eds.) WASA 2013. LNCS, vol. 7992, pp. 512–523. Springer, Heidelberg (2013)
Jing, T., Zhao, C., Xing, X., Huo, Y., Li, W., Cheng, X.: A multi-unit truthful double auction framework for secondary market. In: IEEE ICC (2013)
Kikuchi, H.: (M+1)st-price auction protocol. In: Syverson, P.F. (ed.) FC 2001. LNCS, vol. 2339, pp. 351–363. Springer, Heidelberg (2002)
Krishna, V.: Auction Theory, 2nd edn. Elsevier, Burlington (2010)
Larson, M., Hu, C., Li, R., Li, W., Cheng, X.: Secure auctions without an auctioneer via verifiable secret sharing. In: Workshop on Privacy-Aware Mobile Computing (PAMCO), 2015 In conjunction with ACM MobiHoc 2015. ACM (2015)
Larson, M., Li, R., Hu, C., Li, W., Cheng, X.: A bidder-oriented privacy-preserving vcg auction scheme using homomorphic encryption. In: Xu, K., Zhu, H., Yu, J. (eds.) WASA 2015. LNCS, vol. 9204, pp. 284–294. Springer, Heidelberg (2015)
Li, W., Cheng, X., Bie, R., Zhao, F.: An extensible and flexible truthful auction framework for heterogeneous spectrum markets. In: ACM MobiHoc, Philadelphia, USA, pp. 175–184, August 2014
Li, W., Wang, S., Cheng, X., Bie, R.: Truthful multi-attribute auction with discriminatory pricing in cognitive radio networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 18(1), 3–13 (2014)
Naor, M., Pinkas, B., Sumner, R.: Privacy preserving auctions and mechanism design. In: The 1st ACM Conference on Electronic Commerce, pp. 129–139 (1999)
Nojoumian, M., Stinson, D.R.: Efficient sealed-bid auction protocols using verifiable secret sharing. Inf. Secur. Experience 8434, 302–317 (2014)
Paillier, P.: Public-key cryptosystems based on composite degree residuosity classes. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 223–238. Springer, Heidelberg (1999)
Pan, M., Sun, J., Fang, Y.: Purging the back-room dealing: Secure spectrum auction leveraging paillier cryptosystem. IEEE J. Sel. Areas Commun. 29(4), 866–876 (2011)
Pan, M., Zhu, X., Fang, Y.: Using homomorphic encryption to secure the combinatorial spectrum auction without the trustworthy auctioneer. Wirel. Netw. 18(2), 113–128 (2012)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Suzuki, K., Yokoo, M.: Secure combinatorial auctions by dynamic programming with polynomial secret sharing. In: Blaze, M. (ed.) FC 2002. LNCS, vol. 2357, pp. 44–56. Springer, Heidelberg (2003)
Acknowledgment
The authors would like to thank all the reviewers for their helpful comments. This project was supported by the US National Science Foundation (ECCS-1407986, AST-1443858, CNS-1265311, and CNS-1162057), and the National Natural Science Foundation of China (61171014).
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Larson, M., Li, W., Hu, C., Li, R., Cheng, X., Bie, R. (2015). A Secure Multi-unit Sealed First-Price Auction Mechanism. In: Xu, K., Zhu, H. (eds) Wireless Algorithms, Systems, and Applications. WASA 2015. Lecture Notes in Computer Science(), vol 9204. Springer, Cham. https://doi.org/10.1007/978-3-319-21837-3_29
Download citation
DOI: https://doi.org/10.1007/978-3-319-21837-3_29
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-21836-6
Online ISBN: 978-3-319-21837-3
eBook Packages: Computer ScienceComputer Science (R0)