Abstract
Quantum cryptography is known for enabling functionalities that are unattainable using classical information alone. Recently, Secure Software Leasing (SSL) has emerged as one of these areas of interest. Given a target circuit C from a circuit class, SSL produces an encoding of C that enables a recipient to evaluate C, and also enables the originator of the software to verify that the software has been returned—meaning that the recipient has relinquished the possibility of any further use of the software. Clearly, such a functionality is unachievable using classical information alone, since it is impossible to prevent a user from keeping a copy of the software. Recent results have shown the achievability of SSL using quantum information for a class of functions called compute-and-compare (these are a generalization of the well-known point functions). These prior works, however all make use of setup or computational assumptions. Here, we show that SSL is achievable for compute-and-compare circuits without any assumptions.
Our technique involves the study of quantum copy protection, which is a notion related to SSL, but where the encoding procedure inherently prevents a would-be quantum software pirate from splitting a single copy of an encoding for C into two parts, each of which enables a user to evaluate C. We show that point functions can be copy-protected without any assumptions, for a novel security definition involving one honest and one malicious evaluator; this is achieved by showing that from any quantum message authentication code, we can derive such an honest-malicious copy protection scheme. We then show that a generic honest-malicious copy protection scheme implies SSL; by prior work, this yields SSL for compute-and-compare functions.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
This is an improvement, as a QROM does not depend on the circuit to be computed.
- 2.
Two notions are actually introduced in [5]: finite-term and infinite-term SSL. In this work, SSL refers to finite-term SSL. Furthermore, in [5] all the evaluators in the security game are assumed to behave honestly. In this work, we do not make this assumption and our SSL evaluators can behave maliciously.
- 3.
A circuit class \(\mathcal {C}\) is a compute-and-compare circuit class if for every circuit in \(\mathcal {C}\), there is an associated circuit C and string \(\alpha \) such that on input x, the circuit outputs 1 if and only if \(C(x) = \alpha \). Searchability refers to the fact that there is an efficient algorithm that, on input \(C \in \mathcal {C}\), outputs an x such that \(C(x)=\alpha \). From this point on, searchability is an implicit assumption throughout this work.
- 4.
Informally, evasive functions are the class of functions such that it is hard to find an accepting input, given only black-box access to a functions. Note that compute-and-compare functions are evasive.
- 5.
This notion is weaker than the more common notion of correctness that holds for all inputs. However, in Sect. 4, we give evidence that achieving this stronger notion of correctness may be possible, by showing that for the standard notion of copy protection (against two malicious evaluators), correctness in expectation implies worst-case correctness, which would then imply worst-case correctness for SSL.
- 6.
- 7.
- 8.
The full version is available at: arXiv:2101.12739.
- 9.
There are other trivial strategies, \(e.g. ,\) where Charlie gets an intact program register and Bob does not, but this is a more restricted trivial strategy, since Bob is constrained to evaluate the program honestly.
- 10.
The winning probability may be less than this. By the union bound, even though Bob’s and Charlie’s inputs are not independent, the overall success probability will be at least \(p^{\text {marg}}-\eta \), and we will be considering situations where \(\eta \) is small.
- 11.
This follows from correctness, since for every state
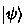 , we necessarily have
, we necessarily have  for some state
for some state  , and by the fact that \(V_kA_k\) must preserve inner products, we necessarily have
, and by the fact that \(V_kA_k\) must preserve inner products, we necessarily have 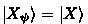 independent of
independent of 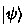 . Thus, we can let
. Thus, we can let 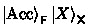 be the accepting state on \(\textsf {FX}\).
be the accepting state on \(\textsf {FX}\).
References
Aaronson, S.: Quantum copy-protection and quantum money. In: 24th Annual Conference on Computational Complexity–CCC 2009, pp. 229–242 (2009). https://doi.org/10.1109/CCC.2009.42
Aaronson, S., Christiano, P.: Quantum money from hidden subspaces. In: 44th Annual ACM Symposium on Theory of Computing–STOC 2012, pp. 41–60 (2012). https://doi.org/10.1145/2213977.2213983
Aaronson, S., Liu, J., Liu, Q., Zhandry, M., Zhang, R.: New approaches for quantum copy-protection. In: Advances in Cryptology–CRYPTO 2021, vol. 1, pp. 526–555 (2021). https://doi.org/10.1007/978-3-030-84242-0_19
Alagic, G., Majenz, C.: Quantum non-malleability and authentication. In: Advances in Cryptology–CRYPTO 2017, vol. 2, pp. 310–341 (2017). https://doi.org/10.1007/978-3-319-63715-0_11
Ananth, P., La Placa, R.L.: Secure software leasing. In: Advances in Cryptology–EUROCRYPT 2021, vol. 2, pp. 501–530 (2021). https://doi.org/10.1007/978-3-030-77886-6_17
Barnum, H., Crépeau, C., Gottesman, D., Smith, A., Tapp, A.: Authentication of quantum messages. In: 43rd Annual Symposium on Foundations of Computer Science–FOCS 2002, pp. 449–485 (2002). https://doi.org/10.1109/SFCS.2002.1181969
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: International Conference on Computers, Systems and Signal Processing, pp. 175–179 (1984)
Broadbent, A., Lord, S.: Uncloneable Quantum Encryption via Oracles. In: 15th Conference on the Theory of Quantum Computation, Communication and Cryptography–TQC 2020, pp. 4:1–4:22 (2020). https://doi.org/10.4230/LIPIcs.TQC.2020.4
Broadbent, A., Schaffner, C.: Quantum cryptography beyond quantum key distribution. Des. Codes Crypt. 78(1), 351–382 (2016). https://doi.org/10.1007/s10623-015-0157-4
Cleve, R., Leung, D., Liu, L., Wang, C.: Near-linear constructions of exact unitary 2-designs. Quantum Inf. Comput. 16(9–10), 721–756 (2016). https://doi.org/10.26421/QIC16.9-10-1
Coladangelo, A., Majenz, C., Poremba, A.: Quantum copy-protection of compute-and-compare programs in the quantum random oracle model. arXiv preprint arXiv:2009.13865 (2020)
Dankert, C., Cleve, R., Emerson, J., Livine, E.: Exact and approximate unitary 2-designs and their application to fidelity estimation. Phys. Rev. A 80, 012304 (2009). https://doi.org/10.1103/PhysRevA.80.012304
Dieks, D.: Communication by EPR devices. Phys. Lett. A 92(6), 271–272 (1982). https://doi.org/10.1016/0375-9601(82)90084-6
Dulek, Y., Speelman, F.: Quantum ciphertext authentication and key recycling with the trap code. In: 13th Conference on the Theory of Quantum Computation, Communication and Cryptography–TQC 2018. pp. 1:1–1:17 (2018). https://doi.org/10.4230/LIPIcs.TQC.2018.1
Dupuis, F., Nielsen, J.B., Salvail, L.: Actively secure two-party evaluation of any quantum operation. In: Advances in Cryptology–CRYPTO 2012, pp. 794–811 (2012). https://doi.org/10.1007/978-3-642-32009-5_46
Gao, J.: Quantum union bounds for sequential projective measurements. Phys. Rev. A 92(5), 052331 (2015). https://doi.org/10.1103/PhysRevA.92.052331
Garg, S., Yuen, H., Zhandry, M.: New security notions and feasibility results for authentication of quantum data. In: Advances in Cryptology–CRYPTO 2017, vol. 2, pp. 342–371 (2017). https://doi.org/10.1007/978-3-319-63715-0_12
Gottesman, D.: Uncloneable encryption. Quantum Inf. Comput. 3(6), 581–602 (2003). https://doi.org/10.26421/QIC3.6-2
Kitagawa, F., Nishimaki, R., Yamakawa, T.: Secure software leasing from standard assumptions. arXiv preprint arXiv:2010.11186 (2020)
Mosca, M., Stebila, D.: Quantum coins. In: Error-Correcting Codes, Finite Geometries and Cryptography, pp. 35–47 (2010)
Naor, M., Reingold, O.: On the construction of pseudorandom permutations: Luby–Rackoff revisited. J. Cryptology 12(1), 29–66 (1999). https://doi.org/10.1007/PL00003817
Park, J.L.: The concept of transition in quantum mechanics. Found. Phys. 1(1), 23–33 (1970). https://doi.org/10.1007/BF00708652
Watrous, J.: The Theory of Quantum Information. 1st edn, Cambridge University Press, Cambridge (2018)
Wiesner, S.: Conjugate coding. ACM SIGACT News 15(1), 78–88 (1983). https://doi.org/10.1145/1008908.1008920
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299, 802–803 (1982). https://doi.org/10.1038/299802a0
Acknowledgements
We would like to thank Christian Majenz and Martti Karvonen for related discussions. This material is based upon work supported by the Air Force Office of Scientific Research under award number FA9550-17-1-0083, Canada’s NFRF and NSERC, an Ontario ERA, and the University of Ottawa’s Research Chairs program. SJ is a CIFAR Fellow in the Quantum Information Science program.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 International Association for Cryptologic Research
About this paper
Cite this paper
Broadbent, A., Jeffery, S., Lord, S., Podder, S., Sundaram, A. (2021). Secure Software Leasing Without Assumptions. In: Nissim, K., Waters, B. (eds) Theory of Cryptography. TCC 2021. Lecture Notes in Computer Science(), vol 13042. Springer, Cham. https://doi.org/10.1007/978-3-030-90459-3_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-90459-3_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-90458-6
Online ISBN: 978-3-030-90459-3
eBook Packages: Computer ScienceComputer Science (R0)


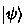 , we necessarily have
, we necessarily have  for some state
for some state  , and by the fact that
, and by the fact that 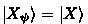 independent of
independent of 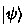 . Thus, we can let
. Thus, we can let 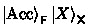 be the accepting state on
be the accepting state on 