Abstract
Secure software leasing (SSL) is a quantum cryptographic primitive that enables an authority to lease software to a user by encoding it into a quantum state. SSL prevents users from generating authenticated pirated copies of leased software, where authenticated copies indicate those run on legitimate platforms. Although SSL is a relaxed variant of quantum copy protection that prevents users from generating any copy of leased softwares, it is still meaningful and attractive. Recently, Ananth and La Placa proposed the first SSL scheme. It satisfies a strong security notion called infinite-term security. On the other hand, it has a drawback that it is based on public key quantum money, which is not instantiated with standard cryptographic assumptions so far. Moreover, their scheme only supports a subclass of evasive functions.
In this work, we present SSL schemes that satisfy a security notion called finite-term security based on the learning with errors assumption (LWE). Finite-term security is weaker than infinite-term security, but it still provides a reasonable security guarantee. Specifically, our contributions consist of the following.
-
We construct a finite-term secure SSL scheme for pseudorandom functions from the LWE assumption against quantum adversaries.
-
We construct a finite-term secure SSL scheme for a subclass of evasive functions from the LWE assumption against sub-exponential quantum adversaries.
-
We construct finite-term secure SSL schemes for the functionalities above with classical communication from the LWE assumption against (sub-exponential) quantum adversaries.
SSL with classical communication means that entities exchange only classical information though they run quantum computation locally.
Our crucial tool is two-tier quantum lightning, which is introduced in this work and a relaxed version of quantum lighting. In two-tier quantum lightning schemes, we have a public verification algorithm called semi-verification and a private verification algorithm called full-verification. An adversary cannot generate possibly entangled two quantum states whose serial numbers are the same such that one passes the semi-verification, and the other also passes the full-verification. We show that we can construct a two-tier quantum lightning scheme from the LWE assumption.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Software is modeled as (Boolean) circuits or functions.
- 2.
We will refer to a few concurrent works in Sect. 1.4.
- 3.
Their constructions need heuristic assumptions related to randomness leakage and circular security [BDGM20, GP21], a heuristic construction of oblivious LWE sampling [WW21], a heuristic construction of noisy linear functional encryption [AP20], or an idealized model [BGMZ18, CHVW19]. Some heuristic assumptions [GP21, WW21, BDGM20] were found to be false [HJL21].
- 4.
In the actual syntax, it also outputs a software, which is negligibly close to a software given as input.
- 5.
A compute-and-compare circuit is specified by a circuit C and a target value \(\alpha \) and outputs 1 on input x if and only if \(C(x)=\alpha \).
- 6.
In the original construction in [AL21], seNIZK also proves that \(\mathsf {pk}\) and \(\widetilde{C}\) was honestly generated. However, we found that this is redundant, and essentially the same security proof works even if it only proves the knowledge of an accepting input of \(\widetilde{C}\). We note that it is important to include \(\mathsf {pk}\) in the statement to bind a proof to \(\mathsf {pk}\) even though the knowledge proven by the seNIZK has nothing to do with \(\mathsf {pk}\). In fact, this observation is essential to give our simplified construction of SSL.
- 7.
Note that Ananth and La Placa proved that the construction in fact satisfies infinite-term security that is stronger than finite-term security. For ease of exposition of our ideas, we explain why the construction satisfies finite-term security.
- 8.
This approach was also discussed in the introduction of [Zha21].
- 9.
Strictly speaking, our construction additionally uses message authentication code (MAC).
- 10.
Strictly speaking, we need to assume the key-injectiveness for the PRF. See the full version of this paper [KNY20] for the definition.
- 11.
More precisely, they prove an analogous property for a family of noisy trapdoor claw-free permutations.
- 12.
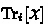 is the partial trace of
is the partial trace of 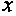 where the i-th register is traced out.
where the i-th register is traced out. - 13.
[RS19] proved essentially the same lemma through an abstraction which they call 1-of-2 puzzle.
- 14.
Of course, such a replacement cannot be done efficiently. We consider such an experiment only as a proof tool.
References
Aaronson, S.: Limitations of quantum advice and one-way communication. Theory Comput. 1(1), 1–28 (2005)
Aaronson, S.: Quantum copy-protection and quantum money. In: Proceedings of the 24th Annual IEEE Conference on Computational Complexity, CCC 2009, pp. 229–242 (2009)
Aaronson, S., Christiano, P.: Quantum money from hidden subspaces. In: 44th ACM STOC, pp. 41–60 (2012)
Amos, R., Georgiou, M., Kiayias, A., Zhandry, M.: One-shot signatures and applications to hybrid quantum/classical authentication. In: 52nd ACM STOC, pp. 255–268 (2020)
Ananth, P., La Placa, R.L.: Secure software leasing. In: Canteaut, A., Standaert, F.-X. (eds.) EUROCRYPT 2021. LNCS, vol. 12697, pp. 501–530. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-77886-6_17
Aaronson, S., Liu, J., Liu, Q., Zhandry, M., Zhang, R.: New approaches for quantum copy-protection. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12825, pp. 526–555. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84242-0_19
Aaronson, S., Liu, J., Zhang, R.: Quantum copy-protection from hidden subspaces (2020). CoRR, abs/2004.09674, version v5 or older
Agrawal, S., Pellet-Mary, A.: Indistinguishability obfuscation without maps: attacks and fixes for noisy linear FE. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020. LNCS, vol. 12105, pp. 110–140. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-45721-1_5
Brakerski, Z., Christiano, P., Mahadev, U., Vazirani, U.V., Vidick, T.: A cryptographic test of quantumness and certifiable randomness from a single quantum device. In: 59th FOCS, pp. 320–331 (2018)
Brakerski, Z., Döttling, N., Garg, S., Malavolta, G.: Factoring and pairings are not necessary for iO: circular-secure LWE suffices. Cryptology ePrint Archive, Report 2020/1024 (2020). https://eprint.iacr.org/2020/1024
Barak, B., et al.: On the (im)possibility of obfuscating programs. J. ACM 59(2), 6:1-6:48 (2012)
Bartusek, J., Guan, J., Ma, F., Zhandry, M.: Return of GGH15: provable security against zeroizing attacks. In: Beimel, A., Dziembowski, S. (eds.) TCC 2018. LNCS, vol. 11240, pp. 544–574. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03810-6_20
Broadbent, A., Jeffery, S., Lord, S., Podder, S., Sundaram, A.: Secure Software Leasing Without Assumptions (2021)
Cohen, A., Holmgren, J., Nishimaki, R., Vaikuntanathan, V., Wichs, D.: Watermarking cryptographic capabilities. SIAM J. Comput. 47(6), 2157–2202 (2018)
Canetti, R., Halevi, S., Steiner, M.: Hardness amplification of weakly verifiable puzzles. In: Kilian, J. (ed.) TCC 2005. LNCS, vol. 3378, pp. 17–33. Springer, Heidelberg (2005). https://doi.org/10.1007/978-3-540-30576-7_2
Chen, Y., Hhan, M., Vaikuntanathan, V., Wee, H.: Matrix PRFs: constructions, attacks, and applications to obfuscation. In: Hofheinz, D., Rosen, A. (eds.) TCC 2019. LNCS, vol. 11891, pp. 55–80. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-36030-6_3
Coladangelo, A., Majenz, C., Poremba, A.: Quantum copy-protection of compute-and-compare programs in the quantum random oracle model (2020)
Coladangelo, A., Sattath, O.: A quantum money solution to the blockchain scalability problem. CoRR, abs/2002.11998 (2020)
Farhi, E., Gosset, D., Hassidim, A., Lutomirski, A., Shor, P.W.: Quantum money from knots. In: ITCS 2012, pp. 276–289 (2012)
Goyal, R., Kim, S., Manohar, N., Waters, B., Wu, D.J.: Watermarking public-key cryptographic primitives. In: Boldyreva, A., Micciancio, D. (eds.) CRYPTO 2019. LNCS, vol. 11694, pp. 367–398. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-26954-8_12
Gay, R., Pass, R.: Indistinguishability obfuscation from circular security. In: STOC ’21: 53rd Annual ACM SIGACT Symposium on Theory of Computing, Virtual Event, Italy, 21–25 June 2021, pp. 736–749 (2021)
Georgiou, M., Zhandry, M.: Unclonable decryption keys. IACR Cryptol. ePrint Arch. 2020, 877 (2020)
Hopkins, S., Jain, A., Lin, H.: Counterexamples to new circular security assumptions underlying iO. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12826, pp. 673–700. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84245-1_23
Kitagawa, F., Nishimaki, R., Yamakawa, T.: Secure Software Leasing from Standard Assumptions. Cryptology ePrint Archive, Report 2020/1314 (2020). https://eprint.iacr.org/2020/1314
Peikert, C., Shiehian, S.: Noninteractive zero knowledge for np from (plain) learning with errors. In: Boldyreva, A., Micciancio, D. (eds.) CRYPTO 2019. LNCS, vol. 11692, pp. 89–114. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-26948-7_4
Peikert, C., Waters, B.: Lossy trapdoor functions and their applications. SIAM J. Comput. 40(6), 1803–1844 (2011)
Radian, R., Sattath, O.: Semi-quantum money. In: Proceedings of the 1st ACM Conference on Advances in Financial Technologies, AFT 2019, pp. 132–146 (2019)
Roberts, B., Zhandry, M.: Franchised quantum money. In: Asiacrypt 2021 (to appear) (2021). https://www.cs.princeton.edu/~mzhandry/docs/papers/Z21b.pdf
Wee, H., Wichs, D.: Candidate obfuscation via oblivious LWE sampling. In: Canteaut, A., Standaert, F.-X. (eds.) EUROCRYPT 2021. LNCS, vol. 12698, pp. 127–156. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-77883-5_5
Zhandry, M.: Quantum lightning never strikes the same state twice. or: quantum money from cryptographic assumptions. J. Cryptol. 34(1), 1–56 (2021). https://doi.org/10.1007/s00145-020-09372-x
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 International Association for Cryptologic Research
About this paper
Cite this paper
Kitagawa, F., Nishimaki, R., Yamakawa, T. (2021). Secure Software Leasing from Standard Assumptions. In: Nissim, K., Waters, B. (eds) Theory of Cryptography. TCC 2021. Lecture Notes in Computer Science(), vol 13042. Springer, Cham. https://doi.org/10.1007/978-3-030-90459-3_2
Download citation
DOI: https://doi.org/10.1007/978-3-030-90459-3_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-90458-6
Online ISBN: 978-3-030-90459-3
eBook Packages: Computer ScienceComputer Science (R0)





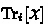 is the partial trace of
is the partial trace of 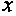 where the i-th register is traced out.
where the i-th register is traced out.