Abstract
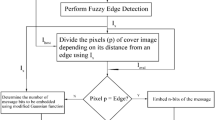
The identification of correct edge location is an important step in edge based image steganography. The edge pixels in an image are characterized by sudden sharp change in intensity; changes made at these locations are inconspicuous to the human eye making it optimal for modification. In this paper, use of Fuzzy inference system to identify the correct edges have been extended to perform edge image steganography, that hides secret message using a hybrid LSB technique. The aim of the proposed hybrid LSB method is to achieve high payload embedding that ensures statistical resemblance between the cover and the generated stego image. It embeds two message bits in the seventh and eighth edge bit using LSB-Matching (LSBM) and LSB-Replacement (LSBR). The performance of our method shows substantial improvement in terms of security and image quality compared to existing edge based image steganography approaches. The experimental analysis shows that the stego image achieves high PSNR of 61 dB and SSIM of 0.99 with minimum level of distortion at high embedding rate observed by gradually increasing % pixels modifications. The method is validated to be secure against RS analysis and Pixel-wise Histogram steganalysis, tested with 2000 grayscale images from BOSSBase 1.0 database.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Laishram, D., Tuithung, T.: A survey on digital image steganography: current trends and challenges. SSRN Electron. J. (2018). https://doi.org/10.2139/ssrn.3171494
Subhedar, M., Mankar, V.: Current status and key issues in image steganography: a survey. Comput. Sci. Rev. 13–14 (2014). https://doi.org/10.1016/j.cosrev.2014.09.001
Islam, S., Modi, M., Gupta, P.: Edge-based image steganography. EURASIP J. Inf. Secur. 8 (2014). https://doi.org/10.1186/1687-417X-2014-8
Chan, C.-K., Cheng, L.M.: Hiding data in images by simple LSB substitution. Pattern Recogn. 37, 469–474 (2004). https://doi.org/10.1016/j.patcog.2003.08.007
Ker, A.: Steganalysis of LSB matching in grayscale images. IEEE Sig. Process. Lett. 12, 441–444 (2005). https://doi.org/10.1109/LSP.2005.847889
Li, B., He, J., Huang, J., Shi, Y.Q.: A survey on image steganography and steganalysis. J. Inf. Hiding Multimed. Sig. Process. 2, 142–172 (2011)
Jung, K.-H.: Comparative histogram analysis of LSB-based image steganography. WSEAS Trans. Syst. Control 13, 103–112 (2018)
Li, X., Zeng, T., Yang, B.: A further study on steganalysis of LSB matching by calibration, pp. 2072–2075 (2008). https://doi.org/10.1109/ICIP.2008.4712194
Mielikainen, J.: LSB matching revisited. IEEE Sig. Process. Lett. 13, 285–287 (2006). https://doi.org/10.1109/LSP.2006.870357
Tseng, H.-W., Leng, H.-S.: A steganographic method based on pixel-value differencing and the perfect square number. J. Appl. Math. (2013). https://doi.org/10.1155/2013/189706
Chang, K.-C., Chang, C.-P., Huang, P., Tu, T.-M.: A novel image steganographic method using tri-way pixel-value differencing. J. Multimed. 3 (2008). https://doi.org/10.4304/jmm.3.2.37-44
Al-Dmour, H., Al-Ani, A.: A steganography embedding method based on edge identification and XOR coding. Expert Syst. Appl. 46 (2015). https://doi.org/10.1016/j.eswa.2015.10.024
Dhargupta, S., Chakraborty, A., Ghosal, S., Saha, S., Sarkar, R.: Fuzzy edge detection based steganography using modified Gaussian distribution. Multimed. Tools Appl. https://doi.org/10.1007/s11042-018-7123-x
Luo, W., Huang, F., Huang, J.: Edge adaptive image steganography based on LSB matching revisited. IEEE Trans. Inf. Forensics Secur. 5, 201–214 (2010). https://doi.org/10.1109/TIFS.2010.2041812
Hiary, H., Sabri, K.E., Mohammed, M., Al-Dhamari, A.: A hybrid steganography system based on LSB matching and replacement. Int. J. Adv. Comput. Sci. Appl. 7 (2016)
Kumar, S., Singh, A., Kumar, M.: Information hiding with adaptive steganography based on Novel Fuzzy edge identification. Defense Technol. 15, 162–169 (2019)
http://in.mathworks.com/help/fuzzy/fuzzy-logic-image-processing.html
http://in.mathworks.com/matlabcentral/fileexchange/image-quality-measures
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Laishram, D., Tuithung, T., Jeneetaa, T. (2021). Fuzzy Edge Image Steganography Using Hybrid LSB Method. In: Misra, R., Kesswani, N., Rajarajan, M., Bharadwaj, V., Patel, A. (eds) Internet of Things and Connected Technologies. ICIoTCT 2020. Advances in Intelligent Systems and Computing, vol 1382. Springer, Cham. https://doi.org/10.1007/978-3-030-76736-5_23
Download citation
DOI: https://doi.org/10.1007/978-3-030-76736-5_23
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-76735-8
Online ISBN: 978-3-030-76736-5
eBook Packages: EngineeringEngineering (R0)