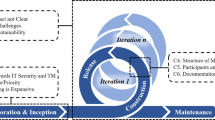
Abstract
Today, a central and critical aspect of cybersecurity problems is related to software problem. Software security is about the understanding of software-induced security risks and how to manage them. To manage software security effectively, we need to understand the process of designing, building, and testing software for security. The System Development Life Cycle (SDLC) process that is currently used to support software development does not address any security components until after the software is developed. From the perspective of software security, the Secure Software Development Life Cycle (SSDLC) is similar to the SDLC but includes security components in its phases. There have been many SSDLC models proposed that are primarily modified from preexisting SDLC models. A study was conducted to survey a selected group of SSDLC models and their effectiveness. The authors first identified four popular SSDLC models used in the IT industry and then analyzed their common characteristics to derive four sets of criteria for comparison. These criteria are Focus Areas of Application, Implementation of Model, Security Implementations and Enhancements, and Security Training and Staff. Overall, the comparison results demonstrate that the Rastogi and Jones model is considered to be an effective one for many IT projects, especially for Agile projects. However, it is worthy to mention that, because of the various types of IT projects, one specific model cannot be applied for use in all types of IT projects. For an IT project operated in Waterfall, the BSI Seven Touchpoints model can be an excellent alternative.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Identity Theft. https://www.usa.gov/identity-theft. Accessed 24 Feb 2020
Massive Smart Home Breach Leads To Consumer Security Concerns. https://www.idtheftcenter.org/massive-smart-home-breach-leads-to-consumer-security-concerns/. Accessed 24 Feb 2020
Ring Throws Customers Under The Bus After Data Breach. https://www.eff.org/deeplinks/2019/12/ring-throws-customers-under-bus-after-data-breach. Accessed 24 Feb 2020
H.D. Benington, Production of large computer programs, in Proceedings, ONR Symposium on Advanced Programming Methods for Digital Computers, (1956), pp. 15–27
W.W. Royce, Manage the development of large software systems, proceedings. IEEE WESCON 26, 1–9 (1970). http://www-scf.usc.edu/~csci201/lectures/Lecture11/royce1970.pdf. Accessed 24 Feb 2020
B.W. Boehm, A Spiral Model of Software Development and Enhancement, Computer (1988), pp. 61–72
The Scrum Guide, pp. 17. https://www.scrumguides.org/docs/scrumguide/v2016/2016-Scrum-Guide-US.pdf. Accessed 24 Mar 2020
K. Beck et al. Manifesto for Agile Software Development. https://Agilemanifesto.org/iso/en/manifesto.html. Accessed 24 Feb 2020
J.M. Kerr, R. Hunter, Inside RAD: How to Build a Fully Functional System in 90 Days or Less (McGraw-Hill, 1994)
Software Prototyping. https://www.ingsoftware.com/software-prototyping. Accessed 24 Mar 2020
I. Jacobson, G. Booch, J. Rumbaugh, The Unified Software Development Process (Addison-Wesley Professional, 1999)
K. Beck, Extreme Programming Explained: Embrace Change (Addison-Wesley, 2000)
European Commission, Special Eurobarometer 460, Attitudes towards the impact of digitisation and automation on daily life (2017). https://ec.europa.eu/commfrontoffice/publicopinion/index.cfm/Survey/getSurveyDetail/instruments/SPECIAL/surveyKy/2160. Accessed 24 Feb 2020
PwC Consumer Intelligence Series: Protect.me https://www.pwc.com/us/en/services/consulting/library/consumer-intelligence-series/cybersecurity-protect-me.html. Accessed 24 Feb 2020
R.L. Jones, A. Rastogi, Secure coding: Building security into the software development life cycle. 29-39. Inf. Syst. Secur. 13(5) (2004)
Keary, E., & Manico, J. (n.d.). Secure Development LifeCycle. https://www.owasp.org/images/7/76/Jim_Manico_(Hamburg)_-_Securiing_the_SDLC.pdf. Accessed 24 Feb 2020
S. Lipner, The trustworthy computing security development LifeCycle, in Proc. 20 th Annual Computer Security Applications Conference, Pp 2-15, Tucson, AZ, (2004)
G. McGraw, Software security. IEEE Secur. Priv. 2(2), 80–83 (2004)
Microsoft. (2012). Microsoft Security Development Lifecycle (SDL) – Version 5.2. https://docs.microsoft.com/en-us/previous-versions/windows/desktop/cc307748%28v%3dmsdn.10%29. Accessed 24 Feb 2020
M. Morana. Building Security into the Software Life Cycle, a Business Case (n.d.). https://www.blackhat.com/presentations/bh-usa-06/bh-us-06-Morana-R3.0.pdf. Accessed 24 Feb 2020
T. Ayalew, T. Kidane, B. Carlsson, Identification and evaluation of security activities in agile projects, in 2013 Nordic Conference on Secure IT Systems, (Ilulissat, Greenland, 2013), pp. 139–153
M.I. Daud, Secure software development model: A guide for secure software life cycle, in Proc. the International MultiConference of Engineerings and Computer Scientist 2010, Vol. I, Hongkong, (2010)
J. Gregoire, K. Buyens, B.D. Win, R. Scandariato, W. Joosen, On the secure software development process: CLASP and SDL compared, in Proc. 29 th International Conference on Software Engineering Workshops, 2007. https://www.researchgate.net/publication/4261954_On_the_Secure_Software_Development_Process_CLASP_and_SDL_Compared. Accessed 24 Feb 2020
K. Tiirik, Comparison of SDLC and Touchpoints. https://courses.cs.ut.ee/MTAT.03.246/2013_spring/uploads/Main/essay09.pdf. Accessed 24 Feb 2020
B.D. Win, R. Scandariato, K. Buyens, J. Gregoire, W. Joosen, On the secure software development process: CLASP, SDL and Touchpoints compared, information and software technology archive. 51(7), 1152–1117 (2009)
Microsoft, Security development Lifecycle for agile development, in Microsoft Security Development Lifecycle, (2009). https://www.blackhat.com/presentations/bh-dc-10/Sullivan_Bryan/BlackHat-DC-2010-Sullivan-SDL-Agile-wp.pdf. Accessed 24 Feb 2020
G. McGraw, Software Security, Building Security In. http://www.swsec.com/resources/touchpoints/. Accessed 3/24/2020
D. NooPur, Developing secure software, in secure software engineering. The DoD software Tech News 8(2), 3–7 (2005). http://www.sis.pitt.edu/jjoshi/devsec/securesoftware.pdf. Accessed 24 Feb 2020
J. W. Over. Team Software Software Process for Secure Software Development (2002) . https://resources.sei.cmu.edu/asset_files/Presentation/2002_017_001_24393.pdf. Accessed 24 Feb 2020
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Liou, JC., Duclervil, S.R. (2020). A Survey on the Effectiveness of the Secure Software Development Life Cycle Models. In: Daimi, K., Francia III, G. (eds) Innovations in Cybersecurity Education. Springer, Cham. https://doi.org/10.1007/978-3-030-50244-7_11
Download citation
DOI: https://doi.org/10.1007/978-3-030-50244-7_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-50243-0
Online ISBN: 978-3-030-50244-7
eBook Packages: EducationEducation (R0)