Abstract
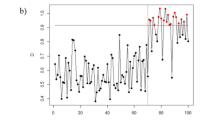
In this study, we propose a new approach to determine intrusions of network in real-time based on statistical process control technique and kernel null space method. The training samples in a class are mapped to a single point using the Kernel Null Foley-Sammon Transform. The Novelty Score are computed from testing samples in order to determine the threshold for the real-time detection of anomaly. The efficiency of the proposed method is illustrated over the KDD99 data set. The experimental results show that our new method outperforms the OCSVM and the original Kernel Null Space method by 1.53% and 3.86% respectively in terms of accuracy.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bodesheim, P., Freytag, A., Rodner, E., Denzler, J.: Local novelty detection in multi-class recognition problems. In: 2015 IEEE Winter Conference on Applications of Computer Vision (WACV), pp. 813–820. IEEE (2015)
Bodesheim, P., Freytag, A., Rodner, E., Kemmler, M., Denzler, J.: Kernel null space methods for novelty detection. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pp. 3374–3381 (2013)
Borkar, A., Donode, A., Kumari, A.: A survey on intrusion detection system (IDS) and internal intrusion detection and protection system (IIDPS). In: International Conference on Inventive Computing and Informatics (ICICI), pp. 949–953. IEEE (2017)
Liu, J., Lian, Z., Wang, Y., Xiao, J.: Incremental kernel null space discriminant analysis for novelty detection. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pp. 792–800 (2017)
Mercado, G.R., Conerly, M.D., Perry, M.B.: Phase i control chart based on a kernel estimator of the quantile function. Qual. Reliab. Eng. Int. 27(8), 1131–1144 (2011)
Nguyen, Q.T., Tran, K.P., Castagliola, P., Truong, T.H., Nguyen, M.K., Lardjane, S.: Nested one-class support vector machines for network intrusion detection. In: 2018 IEEE Seventh International Conference on Communications and Electronics (ICCE), pp. 7–12. IEEE (2018)
Park, Y., Baek, S.H., Kim, S.H., Tsui, K.L.: Statistical process control-based intrusion detection and monitoring. Qual. Reliab. Eng. Int. 30(2), 257–273 (2014)
Schölkopf, B., Platt, J.C., Shawe-Taylor, J., Smola, A.J., Williamson, R.C.: Estimating the support of a high-dimensional distribution. Neural Comput. 13(7), 1443–1471 (2001)
Sheather, S.J., Marron, J.S.: Kernel quantile estimators. J. Am. Stat. Assoc. 85(410), 410–416 (1990)
Tavallaee, M., Bagheri, E., Lu, W., Ghorbani, A.A.: A detailed analysis of the KDD cup 99 data set. In: 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, CISDA 2009, pp. 1–6. IEEE (2009)
Trinh, V.V., Tran, K.P., Huong, T.T.: Data driven hyperparameter optimization of one-class support vector machines for anomaly detection in wireless sensor networks. In: 2017 International Conference on Advanced Technologies for Communications (ATC), pp. 6–10, October 2017. https://doi.org/10.1109/ATC.2017.8167642
Wang, Y., Wong, J., Miner, A.: Anomaly intrusion detection using one class SVM. In: Information Assurance Workshop, pp. 358–364 (2004)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 ICST Institute for Computer Sciences, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Truong, T.H., Ta, P.B., Nguyen, Q.T., Du Nguyen, H., Tran, K.P. (2019). A Data-Driven Approach for Network Intrusion Detection and Monitoring Based on Kernel Null Space. In: Duong, T., Vo, NS., Nguyen, L., Vien, QT., Nguyen, VD. (eds) Industrial Networks and Intelligent Systems. INISCOM 2019. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 293. Springer, Cham. https://doi.org/10.1007/978-3-030-30149-1_11
Download citation
DOI: https://doi.org/10.1007/978-3-030-30149-1_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-30148-4
Online ISBN: 978-3-030-30149-1
eBook Packages: Computer ScienceComputer Science (R0)