Abstract
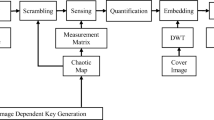
The traditional image encryption method is to encrypt the plain image (PLI) into a noise-like encrypted image (EI), which can hide the information of the PLI well. However, when the EI is transmitted over the Internet, it is easy to attract the attention of hackers due to its special appearance, and the probability of EI being attacked is also greatly improved. To solve this problem, a visually secure image encryption scheme (VSIES) is proposed in this paper by using the newly designed one-dimensional sinusoidal chaotic (1-DSC) map, P-tensor product compressive sensing and discrete U transform (DUT). First, a key generation mechanism is designed where the secure hash algorithm SHA-512 is used to generate the key parameters. Then, this key is used to control the 1-DSC map to generate a measurement matrix, and the sparse coefficient matrix of the PLI is measured. Next, a double zigzag confusion method is designed to scramble the measurement values and the obtained image is diffused to find the secret image (SE). Finally, in order to randomly embed SE into a carrier image to obtain a cipher image with visually meaningful, a DUT-based embedding technique is proposed. The experimental results show that the information entropy value of the SE generated by the encryption scheme is close to 8, which proves that our encryption scheme has a good encryption effect. The visual security (VIS) of our encrypted images is 10–15 dB higher than some existing VSIES, which fully proves that our proposed encryption scheme has high VIS.














Similar content being viewed by others
Availability of data and material
The authors declare that data and material will be made available on reasonable request.
Code availability
The authors declare that the code will be made available on reasonable request.
References
Zhang, Y., Wang, P., Huang, H., Zhu, Y., Xiao, D., Xiang, Y.: Privacy-assured FogCS: chaotic compressive sensing for secure industrial big image data processing in fog computing. IEEE Trans. Ind. Inf. 17(5), 3401–3411 (2021)
Xian, Y., Wang, X., Teng, L.: Double parameters fractal sorting matrix and its application in image encryption. IEEE Trans. Circuits Syst. Video Technol. 32(6), 4028–4037 (2021)
Man, Z., Li, J., Di, X., Sheng, Y., Liu, Z.: Double image encryption algorithm based on neural network and chaos. Chaos Solitons Fractals 152, 111318 (2021)
He, Y., Zhang, Y., He, X., Wang, X.: A new image encryption algorithm based on the OFLSTMS and chaotic sequences. Sci. Rep. 11, 6398 (2021)
Su, Y., Wang, X.: A robust visual image encryption scheme based on controlled quantum walks. Physica A Stat. Mech. Appl.. 587, 126529 (2022)
Dong, Y., Huang, X., Mei, Q., Gan, Y.: Self-adaptive image encryption algorithm based on quantum logistic map. Secur. Commun. Netw. 2021, 6674948 (2021)
Wang, X., Gao, S.: A chaotic image encryption algorithm based on a counting system and the semi-tensor product. Multimed. Tools Appl. 80, 10301–10322 (2021)
Khan, J., Kayhan, S.: Chaos and compressive sensing based novel image encryption scheme. J. Inf. Secur. Appl. 58, 102711 (2021)
Huang, W., Jiang, D., An, Y., Liu, L., Wang, X.: A novel double-image encryption algorithm based on Rossler hyper-chaotic system and compressive sensing. IEEE Access 9, 41704–41716 (2021)
Luo, Y., Lin, J., Liu, J., Wei, D., Cao, L., Zhou, R., Cao, Y., Ding, X.: A robust image encryption algorithm based on Chua’s circuit and compressive sensing. Signal Process. 161, 227–247 (2019)
Yang, Y., Tian, J., Lei, H., Zhou, Y., Shi, W.: Novel quantum image encryption using one-dimensional quantum cellular automata. Inf. Sci. 345, 257–270 (2016)
Xu, X., Chen, S.: A remote sensing image encryption method combining chaotic neuron and Tent map. J. Comput. Taipei 32(2), 108–123 (2021)
Zhang, Y., Zhao, R., Xiao, X., Lan, R., Liu, Z., Zhang, X.: HF-TPE: high-fidelity thumbnail- preserving encryption. IEEE Trans. Circuits Syst. Video Technol. 32, 947–961 (2022)
Ding, Y., Tan, F., Qin, Z., Cao, M., Choo, K.R., Qin, Z.: DeepKeyGen: a deep learning-based stream cipher generator for medical image encryption and decryption. IEEE Trans. Neural Netw. Learn. Syst. 33(9), 4915–4929 (2022)
Bao, L., Zhou, Y.: Image encryption: generating visually meaningful encrypted images. Inf. Sci. 324, 197–207 (2015)
Chai, X., Wu, H., Gan, Z., Zhang, Y., Chen, Y.: Hiding cipher-images generated by 2-D compressive sensing with a multi-embedding strategy. Signal Process. 171, 107525 (2020)
Chai, X., Wu, H., Gan, Z., Zhang, Y., Chen, Y., Nixon, K.: An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic LSB embedding. Opt. Lasers Eng. 124, 105837 (2020)
Wang, H., Xiao, D., Li, M., Xiang, Y., Li, X.: A visually secure image encryption scheme based on parallel compressive sensing. Signal Process. 155, 218–232 (2019)
Fay, R.: Introducing the counter mode of operation to compressive sensing based encryption. Inf. Process. Lett. 116, 279–283 (2016)
Artiles, J.A.P., Chaves, D.P.B., Plimentel, C.: Image encryption using block cipher and chaotic sequences. Signal Process. Image Commun. 79, 24–31 (2019)
Zhu, L., Song, H., Zhang, X., Yan, M., Zhang, T., Wang, X., Xu, J.: A robust meaningful image encryption scheme based on block compressive sensing and SVD embedding. Signal Process. 175, 107629 (2020)
Ye, G., Jiao, K., Huang, X.: Quantum logistic image encryption algorithm based on SHA-3 and RSA. Nonlinear Dyn. 104, 2807–2827 (2021)
Wang, X.Y., Chen, S.N., Zhang, Y.Q.: A chaotic image encryption algorithm based on random dynamic mixing. Opt. Laser Technol. 138, 106837 (2021)
Cheng, D.: Semi-tensor product of matrices and its application to morgen’s problem. Sci. China Series Info. Sci. 44, 195–212 (2001)
Li, Z., Men, X., Li, H.: 3D model retrieval based on U system rotation invariant moments. In: 2nd international conference on pervasive computing and applications birmingham. 25, 749–761 (2007)
Ma, H., Song, R., Qi, D.: Orthogonal complete U-system and its application in CAGD. In: The Proc of 1st Korea-China Joint Conference on Geometric and Visual Computing. Busan, Korea, 31–36 (2005)
Zhou, W., Yan, W., Xu, Q.: Digital watermarking based on the U system technique. Chin. J. Image Graph. 6, 552–557 (2001)
Wolf, A., Swift, J.B., Swinney, H.L., Vastano, J.A.: Determining lyapunov exponents from a time series. Physica D Nonlinear Phenom. 16, 285–317 (1985)
Talhaoui, M.Z., Wang, X. and Midoun, M.A.: A new one-dimensional cosine polynomial chaotic map and its use in image encryption. The Visual Computer, 1–11 (2020)
Mansouri, A., Wang, X.: A novel one-dimensional sine powered chaotic map and its application in a new image encryption scheme. Inf. Sci. 520, 46–62 (2020)
Mansouri, A., Wang, X.: A sensitive dynamic mutual encryption system based on a new 1D chaotic map. Opt. Lasers Eng. 139, 106485 (2021)
Richman, J.S., Moorman, J.R.: Physiological time-series analysis using approximate entropy and sample entropy. Am. J. Physiol. Heart Circ. Physiol. 278, 2039–2049 (2000)
Hua, Z., Zhou, Y., Huang, H.: Cosine-transform-based chaotic system for image encryption. Inf. Sci. 480, 403–419 (2019)
Iwasaki, A.: Analysis of NIST SP800–22 focusing on randomness of each sequence. JSIAM Lett. 10, 1–4 (2018)
Valandar, M.Y., Barani, M.J., Ayubi, P.: A fast color image encryption technique based on three-dimensional chaotic map. Optik (Stuttg). 193, 162921 (2019)
Zhu, L., Jiang, H.: A stable meaningful image encryption scheme using the newly-designed 2D discrete fractional-order chaotic map and Bayesian compressive sensing. Signal Process. 195, 108489 (2022)
Khan, S., Han, L., Lu, H., Butt, K.K., Bachira, G., Khan, N.U.: A new hybrid image encryption algorithm based on 2D-CA, FSM-DNA rule generator, and FSBI. IEEE Access. 7(81333), 81350 (2019)
Chai, X., Yang, K., Gan, Z.: A new chaos-based image encryption algorithm with dynamic key selection mechanisms. Multimed. Tools Appl. 76(7), 9907–9927 (2017)
Zhu, C., Xu, S., Hu, Y., Sun, K.: Breaking a novel image encryption scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dyn. 79(2), 1511–1518 (2014)
Chai, X., Gan, Z., Yang, K., Chen, Y., Liu, X.: An image encryption algorithm based on the memristive hyperchaotic system cellular automata and DNA sequence operations. Signal Process. Image Commun. 52, 6–19 (2017)
Chai, X., Gan, Z., Chen, Y., Zhang, Y.: A visually secure image encryption scheme based on compressive sensing. Signal Process. 134, 35–51 (2017)
Plincus, S.: Approximate entropy (ApEn) as a complexity measure. Chaos 5, 110–117 (1995)
Jiang, D., Liu, L., Wang, X., Rong, X.: Image encryption algorithm for crowd data based on a new hyperchaotic system and Bernstein polynomial. IET Image Process. 15, 3698–3717 (2021)
Farah, M., Farah, A., Farah, T.: An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 99, 3041–3064 (2020)
Toktas, A., Ustun, U.: An image encryption scheme based on an optimal chaotic map derived by multi-objective optimization using ABC algorithm. Nonlinear Dyn. 105, 1885–1909 (2021)
Njitacke, Z.T., Feudjio, C., Signing, V.F., et al.: Circuit and microcontroller validation of the extreme multistable dynamics of a memristive Jerk system: application to image encryption. Eur. Phys. J. Plus. 137, 619 (2022)
Xiong, L., Yang, F., Mou, J., et al.: A memristive system and its applications in red–blue 3D glasses and image encryption algorithm with DNA variation. Nonlinear Dyn. 107, 2911–2933 (2022)
Wang, X., Yang, J., Guan, N.: High-sensitivity image encryption algorithm with random cross diffusion based on dynamically random coupled map lattice model. Chaos Solitons Fractals 143, 110582 (2021)
Wang, X., Guan, N., Yang, J.: Image encryption algorithm with random scrambling based on one-dimensional logistic self-embedding chaotic map. Chaos Soliton Fractals. 150, 111117 (2021)
Wang, X., Su, Y., Xu, M., et al.: A new image encryption algorithm based on Latin square matrix. Nonlinear Dyn. 107, 1277–1293 (2022)
Acknowledgements
All the authors are deeply grateful to the editors for smooth and fast handling of the manuscript. The authors would also like to thank Ang Li for his good advice and the anonymous referees for their valuable suggestions to improve the quality of this paper.
Funding
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61802111, 61872125), the Science and Technology Project of Henan Province (Grant Nos. 232102210109, 232102210096), Key Scientific Research Projects of Colleges and Universities of Henan Province (Grant No. 24A520003), Pre-research Project of SongShan Laboratory (Grant No. YYJC012022011) and the Graduate Talent Program of Henan University (Grant Nos. SYLYC2022193 and SYLAL2023020).
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection and analysis were performed by ZG, BX, ZP, XC, DJ, and XH. The first draft of the manuscript was written by ZG, BX, and ZP. All authors commented on this version of the manuscript. All authors read and approved the final manuscript.
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
Our research is not involved in human participants and animals.
Consent to participate
All the listed authors have participated actively in the study.
Consent for publication
All the listed authors have agreed to publish our article in Nonlinear Dynamics.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gan, Z., Xiong, B., Pang, Z. et al. A visually secure image encryption scheme using newly designed 1D sinusoidal chaotic map and P-tensor product compressive sensing. Nonlinear Dyn 112, 2979–3001 (2024). https://doi.org/10.1007/s11071-023-09203-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-023-09203-1