Abstract
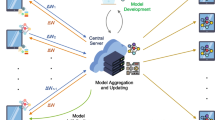
Building a reliable and accurate machine learning (ML) model is challenging in optical networks when training datasets are business-sensitive. We propose a framework of secure collaborative ML learning for predictive maintenance on cross-vendor datasets. Our framework is based on federated learning and multi-party computation technologies. Each vendor builds a local ML model based on its own private data. A server builds a global ML model by aggregating multiple local ML models in a private-preserving way. The server computes only the sum of the local models but cannot see any local model individually by the multi-party computation technique. The vendor-confidential dataset is never exposed to the server or other vendors. Moreover, after the global ML model is deployed in optical networks, the measured data compared to the prediction are privately distributed to the local model owners, which is beneficial to vendors. We applied our framework to the remaining useful life (RUL) prediction of laser device. Our experiments show that an accurate ML model can be built using sensitive datasets in a federated learning setting.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Abdelli, K., Griesser, H., Pachnicke, S.: Machine learning based data driven diagnostic and prognostic approach for laser reliability enhancement, pp. 1–4 (2020)
A hybrid CNN-LSTM approach for laser remaining useful life prediction (2021)
Bell, J., Bonawitz, K.A., Gascón, A., Lepoint, T., Raykova, M.: Secure single-server aggregation with (poly)logarithmic overhead, Cryptology ePrint Archive, Report 2020/704 (2020). https://ia.cr/2020/704
Bonawitz, K.A., et al.: Practical secure aggregation for federated learning on user-held data. CoRR abs/1611.04482 (2016)
Bonawitz, K., et al.: Practical secure aggregation for privacy-preserving machine learning. In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS 2017, pp. 1175–1191 (2017)
Bonawitz, K., et al.: Practical secure aggregation for privacy preserving machine learning, Cryptology ePrint Archive, Report 2017/281 (2017). https://ia.cr/2017/281
Burkhart, M., Strasser, M., Many, D., Dimitropoulos, X.: SEPIA: Privacy-preserving aggregation of multi-domain network events and statistics. In: 19th USENIX Security Symposium (USENIX Security 10) (Washington, DC), August 2010
Celaya, J.R., Saxena, A., Saha, S., Goebel, K.F.: Prognostics of power mosfets under thermal stress accelerated aging using data-driven and model-based methodologies, September 2011
Cho, K., et al.: Learning phrase representations using RNN encoder-decoder for statistical machine translation (2014)
Corrigan-Gibbs, H., Boneh, D.: PRIO: private, robust, and scalable computation of aggregate statistics. In: Proceedings of the 14th USENIX Conference on Networked Systems Design and Implementation, NSDI 2017, pp. 259–282 (2017)
Fredrikson, M., Jha, S., Ristenpart, T.: Model inversion attacks that exploit confidence information and basic countermeasures. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, CCS 2015, pp. 1322–1333 (2015)
Halevi, S., Lindell, Y., Pinkas, B.: Secure computation on the web: computing without simultaneous interaction. In: Rogaway, P. (ed.) CRYPTO 2011. LNCS, vol. 6841, pp. 132–150. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-22792-9_8
Lie, D., Maniatis, P.: Glimmers: Resolving the privacy/trust quagmire. CoRR abs/1702.07436 (2017)
Liu, Z., Wang, Q., Song, C., Cheng, Y.: Similarity-based difference analysis approach for remaining useful life prediction of GAAS-based semiconductor lasers. IEEE Access 5, 21508–21523 (2017)
Brendan McMahan, H., Moore, E., Ramage, D., Hampson, S., Agüera y Arcas, B.: Communication-efficient learning of deep networks from decentralized data (2017)
Mohr, M., Becker, C., Möller, R., Richter, M.: Towards collaborative predictive maintenance leveraging private cross-company data. In: Reussner, R.H., Koziolek, A., Heinrich, R. (eds.) INFORMATIK 2020, Gesellschaft für Informatik, Bonn, pp. 427–432 (2021)
Prakash, S., Hashemi, H., Wang, Y., Annavaram, M., Avestimehr, S.: Byzantine-resilient federated learning with heterogeneous data distribution (2021)
Rabin, T., Ben-Or, M.: Verifiable secret sharing and multiparty protocols with honest majority, STOC 1989, pp. 73–85 (1989)
Saxena, A., Goebel, K.: Phm08 challenge data set (2008)
Shamir, A.: How to share a secret. CACM 22(11), 612–613 (1979)
So, J., Ali, R.E., Guler, B., Jiao, J., Avestimehr, S.: Securing secure aggregation: Mitigating multi-round privacy leakage in federated learning. CoRR abs/2106.03328 (2021)
van der Maaten, L., Hinton, G.: Viualizing data using t-sne 9, 2579–2605 (2008)
Yao, A.C.-C.: How to generate and exchange secrets (extended abstract). In: 27th Annual Symposium on Foundations of Computer Science, Toronto, Canada, vol. 1986, pp. 162–167. IEEE Computer Society (1986)
Acknowledgment
This work has been performed in the framework of the CELTIC-NEXT project AI-NET-PROTECT (Project ID C2019/3-4), and it is partly funded by the German Federal Ministry of Education and Research (FKZ16KIS1279K).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Abdelli, K., Cho, J.Y., Pachnicke, S. (2021). Secure Collaborative Learning for Predictive Maintenance in Optical Networks. In: Tuveri, N., Michalas, A., Brumley, B.B. (eds) Secure IT Systems. NordSec 2021. Lecture Notes in Computer Science(), vol 13115. Springer, Cham. https://doi.org/10.1007/978-3-030-91625-1_7
Download citation
DOI: https://doi.org/10.1007/978-3-030-91625-1_7
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-91624-4
Online ISBN: 978-3-030-91625-1
eBook Packages: Computer ScienceComputer Science (R0)