Abstract
Recent revelations on manipulations and back-doors in modern ECC have initiated the revision of existing schemes and led to the selection of two new solutions for next-generation TLS proposed in RFC 7748: Curve25519 and Curve448. Unfortunately, both curves were designed and optimized primarily for software implementations; their implementation in hardware and physical protection against SCA has been neglected during the design phase. In this work, we demonstrate that both curves can indeed be efficiently and securely mapped to hardware structures of modern FPGAs while including advanced protection mechanisms against physical attacks and still providing high performance and throughput. In particular, our Curve25519 architecture provides more than 1 700 point multiplications per second, using only 1 006 logic slices (LSs) and 20 digital signal processors (DSPs) of a mid-range Xilinx XC7Z020 FPGA. Furthermore, our Curve448 architecture still achieves more than 600 operations per second at a significantly higher security level of 224 bits, using not more than 1 985 LSs and 33 DSPs on the same device. In addition, we performed a practical, test-based leakage assessment for both architectures. More precisely, we investigated the detection of scalar- and base-point-dependable leakage individually while our designs were incorporated scalar blinding and point randomization countermeasures. Eventually, our findings prove with high confidence, that we cannot detect any scalar- and base-point-dependable leakage even after evaluating 1 000 000 power measurements.








Similar content being viewed by others
Notes
According to RFC 7748, Curve448 represents a Montgomery curve and the untwisted Edwards curve actually is called Edwards448. However, since both curves are birationally equivalent, we use the term Curve448 synonymously throughout this work.
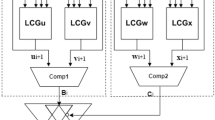
We have chosen this set of countermeasures since it provides us with the opportunity to randomize and protect all input parameters of a single point multiplication.
References
Agrawal D, Archambeault B, Rao JR, Rohatgi P (2002) The EM side-channel(s). In: 4th International workshop on cryptographic hardware and embedded systems - CHES 2002. Redwood Shores, CA, USA, Revised Papers, pp 29–45
Alrimeih H, Rakhmatov DN (2014) Fast and flexible hardware support for ECC over multiple standard prime fields. IEEE Trans VLSI Syst 22(12):2661–2674
Bernstein DJ (2006) Curve25519: new Diffie-Hellman speed records. In: 9th International Conference on theory and practice of public-key cryptography on public key cryptography - PKC 2006. New York, NY, USA, April 24-26, 2006, proceedings, volume 3958 of lecture notes in computer science. Springer, pp 207–228
Coron J-S (1999) Resistance against differential power analysis for elliptic curve cryptosystems. In: 1st International workshop on cryptographic hardware and embedded systems - CHES 1999. Worcester, MA, USA, August 12-13, 1999, proceedings, volume 1717 of lecture notes in computer science. Springer, pp 292–302
de Dormale GM, Quisquater J-J (2007) High-speed hardware implementations of elliptic curve cryptography: a survey. Journal of Systems Architecture
Dugardin M, Papachristodoulou L, Najm Z, Batina L, Danger J-L, Guilley S (2016) Dismantling real-world ECC with horizontal and vertical template attacks. In: Constructive side-channel analysis and secure design - 7th international workshop, COSADE 2016, Graz, Austria, April 14-15, 2016, revised selected papers, volume 9689 of lecture notes in computer science. Springer, pp 88–108
Fan J, Xu G, De Mulder E, Schaumont P, Preneel B, Verbauwhede I (2010) State-of-the-art of secure ECC implementations: a survey on known side-channel attacks and countermeasures. In: IEEE International symposium on hardware oriented security and trust - HOST 2010, Anaheim Convention Center, CA, USA, June 13-14, 2010, proceedings. IEEE Computer Society, pp 76–87
Fan J, Verbauwhede I (2012) An updated survey on secure ECC implementations attacks, countermeasures and cost. In: Cryptography and security: from theory to applications - essays dedicated to Jean-Jacques Quisquater on the occasion of his 65th birthday, volume 6805 of lecture notes in computer science. Springer, pp 265–282
Güneysu T, Paar C (2008) Ultra high performance ECC over NIST primes on commercial FPGAs. In: 10th International workshop on cryptographic hardware and embedded systems - CHES 2008. Washington, D.C., USA, August 10-13, 2008, proceedings, volume 5154 of lecture notes in computer science. Springer, pp 62–78
Hamburg M (2015) Ed448-Goldilocks, a new elliptic curve. IACR Cryptology ePrint Archive, 2015:625. http://eprint.iacr.org/2015/625
Jȧrvinen K, Miele A, Azarderakhsh R, Patrick L (2016) Four\(\mathbb {Q}\) on FPGA: new hardware speed records for elliptic curve cryptography over large prime characteristic fields. In: 18th International conference on cryptographic hardware and embedded systems - CHES 2016. Santa Barbara, CA, USA, August 17-19, 2016, proceedings, volume 9813 of lecture notes in computer science. Springer, pp 517–537
Kocher PC (1996) Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In: 16th Annual international cryptology conference on advances in cryptology - CRYPTO ’96. Santa Barbara, California, USA, proceedings, pp 104–113
Kocher PC, Jaffe J, Jun B (1999) Differential power analysis. In: 19th Annual international cryptology conference on advances in cryptology - CRYPTO ’99. Santa Barbara, California, USA, Proceedings, pp 388–397
UEC Satoh Lab. Side-channel attack user reference architecture. http://satoh.cs.uec.ac.jp/SAKURA/index.html
Montgomery PL (1987) Speeding the Pollard and elliptic curve methods of factorization. Math Comput 48 (177):243–264
De Mulder Elke, Ȯrs SB, Preneel B, Verbauwhede I (2007) Differential power and electromagnetic attacks on a FPGA implementation of elliptic curve cryptosystems. Comput Electric Eng 33(5–6):367–382
Orlando G, Paar C (2001) A scalable GF(p) elliptic curve processor architecture for programmable hardware. In: 3rd International workshop on cryptographic hardware and embedded systems - CHES 2001. Paris, France, May 14-16, 2001, Proceedings, volume 2162 of lecture notes in computer science. Springer, pp 348–363
Örs SB, Batina L, Preneel B, Vandewalle J (2003) Hardware implementation of an elliptic curve processor over GF(p). In: 14th IEEE International conference on application-specific systems, architectures, and processors - ASAP 2003. The Hague, The Netherlands, June 24-26, 2003, Proceedings. IEEE Computer Society, pp 433–443
Poussier R, Zhou Y, Standaert F-X (2017) A systematic approach to the side-channel analysis of ECC implementations with worst-case horizontal attacks. In: 19th International conference on cryptographic hardware and embedded systems - CHES 2017. Taipei, Taiwan, September 25-28, 2017, Proceedings, volume 10529 of lecture notes in computer science. Springer, pp 534–554
Roy DB, Mukhopadhyay D, Izumi M, Takahashi J (2014) Tile before multiplication: an efficient strategy to optimize DSP multiplier for accelerating prime field ECC for NIST curves. In: The 51st Annual design automation conference 2014, DAC ’14. San Francisco, CA, USA, June 1-5, 2014, pp 177:1–177:6
Sakiyama K, Mentens N, Batina L, Preneel B, Verbauwhede I (2006) Reconfigurable modular arithmetic logic unit for high-performance public-key cryptosystems. In: 2nd International Symposium on reconfigurable computing: architectures, tools and applications - ARC 2006. Delft, The Netherlands, March 1-3, 2006, proceedings, volume 3985 of lecture notes in computer science. Springer, pp 347–357
Sasdrich P, Güneysu T (2014) Efficient elliptic-curve cryptography using Curve25519 on reconfigurable devices. In: 10th International Symposium on reconfigurable computing: architectures, tools and applications - ARC 2014. Vilamoura, Portugal, April 14-16, 2014, proceedings, volume 8405 of lecture notes in computer science. Springer, pp 25–36
Sasdrich P, Güneysu T (2015) Implementing Curve25519 for side-channel-protected elliptic curve cryptography. ACM Trans Reconfig Technol Syst - TRETS 9(1):3
Sasdrich P, Güneysu T (2017) Cryptography for next generation TLS - implementing the RFC 7748 elliptic Curve448 cryptosystem in hardware. In: Proceedings of the 54th design automation conference - DAC 2017. Austin, TX, USA, June 18-22, 2017. ACM, pp 1–6
Schindler W, Wiemers A (2015) Efficient side-channel attacks on scalar blinding on elliptic curves with special structure. In: NIST Workshop on ECC standards
Tunstall M, Goodwill G (2016) Applying TVLA to public key cryptographic algorithms. IACR Cryptology ePrint Archive, 2016:513. http://eprint.iacr.org/2016/513
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sasdrich, P., Güneysu, T. Exploring RFC 7748 for Hardware Implementation: Curve25519 and Curve448 with Side-Channel Protection. J Hardw Syst Secur 2, 297–313 (2018). https://doi.org/10.1007/s41635-018-0048-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41635-018-0048-z