Abstract
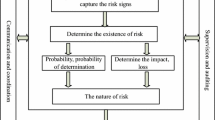
In the context of big data, data acquisition methods are more diverse, the amount of data is larger, and the types of data are more diverse. At the same time, the speed of data processing by big data technology will also be greatly improved. Therefore, using big data technology and data mining methods to conduct early warning research on my country's systemic financial risks will eventually become a trend. Based on the analytic hierarchy model and artificial intelligence technology, this paper constructs a systemic financial risk identification model and establishes a practical analytic hierarchy model. Moreover, this paper organically combines the more prominent influencing factors such as swing curve, network structure and unit parameters, and determines the main parameters of the model according to the strength of the influence of each factor on coherence. In addition, this paper proposes a practical coherence recognition method that takes the network topology and unit parameters as considerations and uses the programming program to realize the reading of BPA data, and based on this, analyzes the topology similarity and parameter similarity of the unit. Finally, this paper deeply analyzes the specificity of the equivalence process of the main grid. Through experimental research, we can see that the model constructed in this paper has certain effects.









Similar content being viewed by others
References
Ahmad K, Mohammad O, Atieh M et al (2018) Iot: architecture, challenges, and solutions using fog network and application classification. In: 2018 international Arab conference on information technology (ACIT). IEEE, pp 1–7
Bull P, Austin R, Popov E et al (2016) Flow based security for IoT devices using an SDN gateway. In: 2016 IEEE 4th international conference on future internet of things and cloud (FiCloud). IEEE, pp 157–163
Chen J, Tian Z, Cui X, Yin L, Wang X (2019) Trust architecture and reputation evaluation for internet of things. J Ambient Intell Humaniz Comput 10(8):3099–3107. https://doi.org/10.1007/s12652-018-0887-z
El Jaouhari S (2018) A secure design of WoT services for smart cities. Ph.D. Thesis, Ecole nationale supérieure Mines-Télécom Atlantique
Ferraiolo D, Kuhn DR, Chandramouli R (2003) Role-based access control. Artech House
Goyal M, Oakley A, Bansal P et al (2019) Automatic lesion boundary segmentation in dermoscopic images with ensemble deep learning methods. arXiv:1902.00809
Hassija V, Chamola V, Saxena V, Jain D, Goyal P, Sikdar B (2019) A survey on IoT security: application areas, security threats, and solution architectures. IEEE Access 7:82721–82743. https://doi.org/10.1109/ACCESS.2019.2924045 ((ISSN:2169-3536))
Huang GB, Zhou H, Ding X, Zhang R (2011) Extreme learning machine for regression and multiclass classification. IEEE Trans Syst Man Cybern B 42(2):513–529
ITU (2012) Y.2060: overview of the Internet of things. https://www.itu.int/rec/T-REC-Y.2060-201206-I. Accessed 16 Oct 2020
Jararweh Y, Al-Ayyoub M, Darabseh A, Benkhelifa E, Vouk MA, Rindos A (2015) SDIoT: a software defined based internet of things framework. J Ambient Intell Humaniz Comput 6(4):453–461. https://doi.org/10.1007/s12652-015-0290-y
Kaur R, Kaur G (2013) Skin cancer–melanoma detection in skin images using local binary pattern (LBP) and GLCM. Int J Sci Res IJSR) 4(7):134–139
Khan R, Khan SU, Zaheer R et al (2012) Future internet: the internet of things architecture, possible applications and key challenges. In: 2012 10th international conference on frontiers of information technology. IEEE, pp 257–260
Li XL, Li Y, Wang ZF (2016) Research on remote sensing image matching based on sift algorithm. Telev Technol 40(9):108
Lim KLA (2012) Computer security event management system. US Patent 8,245,297
Mendonça T, Ferreira PM, Marques JS et al (2013) PH 2-A dermoscopic image database for research and benchmarking. In: 2013 35th annual international conference of the IEEE engineering in medicine and biology society (EMBC). IEEE, pp 5437–5440
OneM2M (2020) OneM2M: standards for m2m and the internet of things. http://www.onem2m.org/. Accessed 16 Oct 2020
Pathan S, Prabhu KG, Siddalingaswamy PC (2018) A methodological approach to classify typical and atypical pigment network patterns for melanoma diagnosis. Biomed Signal Process 44:25–37
Razmjooy N, Mousavi BS, Soleymani F (2012) A real-time mathematical computer method for potato inspection using machine vision. Comput Math Appl 63:268–279
Siegel RL, Miller KD, Jemal A (2019) Cancer statistics. CA Cancer J Clin 66:7–30
Waheed Z, Waheed A, Zafar M et al (2017) An efficient machine learning approach for the detection of melanoma using dermoscopic images. In: 2017 international conference on communication, computing and digital systems (C-CODE). IEEE, pp 316–319
Yu P, Qin AK, Clausi DA (2011) Unsupervised polarimetric SAR image segmentation and classification using region growing with edge penalty. IEEE Trans Geosci Remote Sens 50(4):1302–1317
Zahia S, Sierra-Sosa D, Garcia-Zapirain B, Elmaghraby A (2018) Tissue classification and segmentation of pressure injuries using convolutional neural networks. Comput Method Program Biomed 159:51–58
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations
Rights and permissions
About this article
Cite this article
Zhou, W. Systemic financial risk based on analytic hierarchy model and artificial intelligence system. J Ambient Intell Human Comput (2021). https://doi.org/10.1007/s12652-021-03037-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12652-021-03037-8