Abstract
We propose a novel upconversion (sum frequency generation)-based quantum-optical system design that can be employed as a receiver (Bob) in practical quantum key distribution systems. The pump governing the upconversion process is produced and utilized inside the physical receiver, making its access or control unrealistic for an external adversary (Eve). This pump facilitates several properties which permit Bob to define and control the modes that can participate in the quantum measurement. Furthermore, by manipulating and monitoring the characteristics of the pump pulses, Bob can detect a wide range of quantum hacking attacks launched by Eve.





Similar content being viewed by others
Notes
Security concerns arising from nonlinear interactions in the waveguide, especially the conversion of photons injected by Eve at the signal wavelength after interacting with Bob’s pump, will be examined in the next subsections.
Alternatively, an appropriate filter can be used, but a coiled fiber offers a lower loss and cost-effective solution.
We assume that the optical fibers in front of the receiver would readily fuse, disconnecting the receiver from the quantum channel, for \(\gtrsim \)10 W average input powers [43].
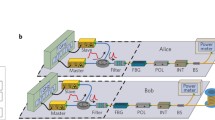
In Fig. 3, the basis choice is implemented by a phase modulator (PM) in the pump arm. An optical path that allows reflection(s), carrying an imprint of the modulation, to propagate out of the system at least physically exists if we assume a fiber-optical wavelength division multiplexer (WDM) instead of the free-space dichroic mirror (DM).
The detector is in linear mode after the gate and displays superlinear characteristics at the falling edge, i.e., when it is making a transition from the Geiger mode to the linear mode.
References
Midwinter, J., Warner, J.: Up-conversion of near infrared to visible radiation in lithium-meta-niobate. J. Appl. Phys. 38(2), 519–523 (1967)
Tucker, J., Walls, D.F.: Quantum theory of parametric frequency conversion. Ann. Phys. 52(1), 1–15 (1969)
Kumar, P.: Quantum frequency conversion. Opt. Lett. 15(24), 1476–1478 (1990)
Huang, J., Kumar, P.: Observation of quantum frequency conversion. Phys. Rev. Lett. 68, 2153–2156 (1992)
Kim, Y.H., Kulik, S.P., Shih, Y.: Quantum teleportation of a polarization state with a complete bell state measurement. Phys. Rev. Lett. 86, 1370–1373 (2001)
Vandevender, A.P., Kwiat, P.G.: High efficiency single photon detection via frequency up-conversion. J. Mod. Opt. 51(9–10), 1433–1445 (2004)
Diamanti, E., Takesue, H., Honjo, T., Inoue, K., Yamamoto, Y.: Performance of various quantum-key-distribution systems using \(1.55-\mu \)m up-conversion single-photon detectors. Phys. Rev. A 72, 052311 (2005)
Ma, L., Slattery, O., Tang, X.: Single photon frequency up-conversion and its applications. Phys. Rep. 521(2), 69–94 (2012)
Thew, R.T., Tanzilli, S., Krainer, L., Zeller, S.C., Rochas, A., Rech, I., Cova, S., Zbinden, H., Gisin, N.: Low jitter up-conversion detectors for telecom wavelength GHz QKD. New J. Phys. 8(3), 32 (2006)
Pelc, J.S., Ma, L., Phillips, C.R., Zhang, Q., Langrock, C., Slattery, O., Tang, X., Fejer, M.M.: Long-wavelength-pumped upconversion single-photon detector at 1550 nm: performance and noise analysis. Opt. Express 19(22), 21445–21456 (2011)
Pelc, J.S., Zhang, Q., Phillips, C.R., Yu, L., Yamamoto, Y., Fejer, M.M.: Cascaded frequency upconversion for high-speed single-photon detection at 1550 nm. Opt. Lett. 37(4), 476–478 (2012)
Eckstein, A., Brecht, B., Silberhorn, C.: A quantum pulse gate based on spectrally engineered sum frequency generation. Opt. Express 19(15), 13770–13778 (2011)
Huang, Y.P., Kumar, P.: Mode-resolved photon counting via cascaded quantum frequency conversion. Opt. Lett. 38(4), 468–470 (2013)
Kowligy, A.S., Manurkar, P., Corzo, N.V., Velev, V.G., Silver, M., Scott, R.P., Yoo, S.J.B., Kumar, P., Kanter, G.S., Huang, Y.P.: Quantum optical arbitrary waveform manipulation and measurement in real time. Opt. Express 22(23), 27942–27957 (2014)
Tanzilli, S., Tittel, W., Halder, M., Alibart, O., Baldi, P., Gisin, N., Zbinden, H.: A photonic quantum information interface. Nature 437(7055), 116–120 (2005)
Gisin, N., Thew, R.: Quantum communication. Nat. Photonics 1, 165–171 (2007)
Kimble, H.J.: The quantum internet. Nature 453(7198), 1023–1030 (2008)
Bennett, C.H., Brassard, G.: In: Proceedings of IEEE International Conference on Computers Systems and Signal Processing, Bangalore, India, pp. 175–179 (1984)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–196 (2002)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81(3), 1301–1350 (2009)
Inoue, K., Waks, E., Yamamoto, Y.: Differential phase shift quantum key distribution. Phys. Rev. Lett. 89(3), 37902 (2002)
Zhang, Q., Takesue, H., Honjo, T., Wen, K., Hirohata, T., Suyama, M., Takiguchi, Y., Kamada, H., Tokura, Y., Tadanaga, O., Nishida, Y., Asobe, M., Yamamoto, Y.: Megabits secure key rate quantum key distribution. New J. Phys. 11(4), 045010 (2009)
Lo, H.K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108(13), 130503 (2012)
Liu, Y., Chen, T.Y., Wang, L.J., Liang, H., Shentu, G.L., Wang, J., Cui, K., Yin, H.L., Liu, N.L., Li, L., Ma, X., Pelc, J.S., Fejer, M.M., Peng, C.Z., Zhang, Q., Pan, J.W.: Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111(13), 130502 (2013)
Xu, H., Ma, L., Mink, A., Hershman, B., Tang, X.: 1310-nm quantum key distribution system with up-conversion pump wavelength at 1550 nm. Opt. Express 15(12), 7247–7260 (2007)
Scarani, V., Kurtsiefer, C.: The black paper of quantum cryptography: real implementation problems. Theor. Comput. Sci. 560, 27–32 (2014)
Lo, H.K., Curty, M., Tamaki, K.: Secure quantum key distribution. Nat. Photonics 8(8), 595–604 (2014)
Jain, N., Stiller, B., Khan, I., Elser, D., Marquardt, C., Leuchs, G.: Attacks on practical quantum key distribution systems (and how to prevent them). arXiv:1512.07990
Website, Vadim Makarov. http://www.vad1.com
Wiechers, C., Lydersen, L., Wittmann, C., Elser, D., Skaar, J., Marquardt, C., Makarov, V., Leuchs, G.: After-gate attack on a quantum cryptosystem. New J. Phys. 13(1), 013043 (2011)
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Thermal blinding of gated detectors in quantum cryptography. Opt. Express 18(26), 27938–27954 (2010)
Gerhardt, I., Liu, Q., Lamas-Linares, A., Skaar, J., Kurtsiefer, C., Makarov, V.: Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat. Commun. 2, 349 (2011)
Sauge, S., Lydersen, L., Anisimov, A., Skaar, J., Makarov, V.: Controlling an actively-quenched single photon detector with bright light. Opt. Express 19(23), 23590–23600 (2011)
Jain, N., Wittmann, C., Lydersen, L., Wiechers, C., Elser, D., Marquardt, C., Makarov, V., Leuchs, G.: Device calibration impacts security of quantum key distribution. Phys. Rev. Lett. 107(11), 5 (2011)
Lydersen, L., Jain, N., Wittmann, C., Maroy, O., Skaar, J., Marquardt, C., Makarov, V., Leuchs, G.: Superlinear threshold detectors in quantum cryptography. Phys. Rev. A 84(3), 032320 (2011)
Weier, H., Krauss, H., Rau, M., Fürst, M., Nauerth, S., Weinfurter, H.: Quantum eavesdropping without interception: an attack exploiting the dead time of single-photon detectors. New J. Phys. 13(7), 073024 (2011)
Bugge, A.N., Sauge, S., Ghazali, A.M.M., Skaar, J., Lydersen, L., Makarov, V.: Laser damage helps the eavesdropper in quantum cryptography. Phys. Rev. Lett. 112(7), 70503 (2014)
Li, H.W., Wang, S., Huang, J.Z., Chen, W., Yin, Z.Q., Li, F.Y., Zhou, Z., Liu, D., Zhang, Y., Guo, G.C., Bao, W.S., Han, Z.F.: Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A 84(6), 062308 (2011)
Jain, N., Anisimova, E., Khan, I., Makarov, V., Marquardt, C., Leuchs, G.: Trojan-horse attacks threaten the security of practical quantum cryptography. New J. Phys. 16(12), 123030 (2014)
Jain, N., Stiller, B., Khan, I., Makarov, V., Marquardt, C., Leuchs, G.: Risk analysis of Trojan-horse attacks on practical quantum key distribution systems. IEEE J. Sel. Top. Quantum Electron. 21(3), 1–10 (2015)
Kanter, G.S.: In: CLEO: 2015, p. JW2A.7. Optical Society of America (2015)
Ferreira da Silva, T., Xavier, G.B., Temporão, G.P., von der Weid, J.P.: Real-time monitoring of single-photon detectors against eavesdropping in quantum key distribution systems. Opt. Express 20(17), 18911–18924 (2012)
Lucamarini, M., Choi, I., Ward, M.B., Dynes, J.F., Yuan, Z.L., Shields, A.J.: Practical security bounds against the Trojan-horse attack in quantum key distribution. Phys. Rev. X 5(3), 031030 (2015)
Bennett, C.H.: Let Eve do the Heavy Lifting, While John and Won-Young Keep Her Honest. http://dabacon.org/pontiff/?p=5340
Dong, H., Pan, H., Li, Y., Wu, E., Zeng, H.: Efficient single-photon frequency upconversion at 1.06 \(\mu \)m with ultralow background counts. Appl. Phys. Lett. 93(7), 071101 (2008)
Itzler, M.A., Jiang, X., Entwistle, M., Slomkowski, K., Tosi, A., Acerbi, F., Zappa, F., Cova, S.: Advances in InGaAsP-based avalanche diode single photon detectors. J. Mod. Opt. 58(3–4), 174–200 (2011)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121–3124 (1992)
Hughes, R.J., Morgan, G.L., Peterson, C.G.: Quantum key distribution over a 48 km optical fibre network. J. Mod. Opt. 47(2–3), 533–547 (2000)
Ekert, A., Rarity, J.G., Tapster, P., Massimo, G.: Palma, practical quantum cryptography based on two-photon interferometry. Phys. Rev. Lett. 69(9), 1293–1295 (1992)
Marcikic, I., de Riedmatten, H., Tittel, W., Zbinden, H., Legré, M., Gisin, N.: Distribution of time-bin entangled qubits over 50 km of optical fiber. Phys. Rev. Lett. 93, 180502 (2004)
Yuan, Z., Shields, A.: Continuous operation of a one-way quantum key distribution system over installed telecom fibre. Opt. Express 13(2), 660–665 (2005)
Boyd, R.W.: Nonlinear Optics, 3rd edn. Academic Press, London (2008)
Gisin, N., Fasel, S., Kraus, B., Zbinden, H., Ribordy, G.: Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A 73(2), 1–6 (2006)
Dichroic Mirrors/Beamsplitters: 1180 nm Cutoff Wavelength. www.thorlabs.com
Dichroic filter 1400BS. www.omegafilters.com
Tanzilli, S., Martin, A., Kaiser, F., De Micheli, M., Alibart, O., Ostrowsky, D.: On the genesis and evolution of integrated quantum optics. Laser Photonics Rev. 6(1), 115–143 (2012)
Harris, N.C., Grassani, D., Simbula, A., Pant, M., Galli, M., Baehr-Jones, T., Hochberg, M., Englund, D., Bajoni, D., Galland, C.: Integrated source of spectrally filtered correlated photons for large-scale quantum photonic systems. Phys. Rev. X 4, 041047 (2014)
\(1\times 2\) 1310/1550 nm High Isolation Filter WDM. www.opneti.com
1550 nm CWL, 12.5 mm Dia. Hard Coated OD 4 50 nm Bandpass Filter. www.edmundoptics.com
830 nm MaxLine Laser Clean-Up Filter. www.semrock.com
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 4, 686–689 (2010)
Zhao, Y., Fung, C.H., Qi, B., Chen, C., Lo, H.K.: Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78(4), 042333 (2008)
Vakhitov, A., Makarov, V., Hjelme, D.: Large pulse attack as a method of conventional optical eavesdropping in quantum cryptography. J. Mod. Opt. 48(13), 2023–2038 (2001)
Kurtsiefer, C., Zarda, P., Mayer, S., Weinfurter, H.: The breakdown flash of silicon avalanche photodiodes-back door for eavesdropper attacks? J. Mod. Opt. 48(13), 2039–2047 (2001)
Makarov, V., Anisimov, A., Skaar, J.: Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74(2), 1–12 (2006)
Acknowledgments
This research was supported in part by the DARPA Quiness program (Grant Number: W31P4Q-13-1-0004).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Jain, N., Kanter, G.S. Upconversion-based receivers for quantum hacking-resistant quantum key distribution. Quantum Inf Process 15, 2863–2879 (2016). https://doi.org/10.1007/s11128-016-1315-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-016-1315-y