Abstract
We establish a bijection between the set of rigged configurations and the set of tensor products of Kirillov–Reshetikhin crystals of type \(D^{(1)}_n\) in full generality. We prove the invariance of rigged configurations under the action of the combinatorial R-matrix on tensor products and show that the bijection preserves certain statistics (cocharge and energy). As a result, we establish the fermionic formula for type \(D_n^{(1)}\). In addition, we establish that the bijection is a classical crystal isomorphism.

Similar content being viewed by others
Notes
In general, if we consider \(\gamma \) for \(B^{r,s}\), the strings in \((\nu ,J)^{(r)}\) which are shorter than s become non-singular.
In general, if we consider \(\beta \) for \(B^{r,1}\), the next \(\delta \) removes length 1 singular strings of \((\nu ,J)^{(1)},(\nu ,J)^{(2)},\ldots ,(\nu ,J)^{(r-1)}\) added by \(\beta \).
References
Baxter, R.J.: Exactly Solved Models in Statistical Mechanics. Academic Press. [Harcourt Brace Jovanovich Publishers], London (1989). Reprint of the 1982 original
bin Mohammad, M.: Scattering rules in soliton cellular automata associated with \(U_q(D_n^{(1)})\)-crystal \(B^{n,1}\). J. Phys. A 45(7), 075208–0752022 (2012)
Date, E., Jimbo, M., Kuniba, A., Miwa, T., Okado, M.: One-dimensional configuration sums in vertex models and affine Lie algebra characters. Lett. Math. Phys. 17(1), 69–77 (1989)
Deka, L., Schilling, A.: New fermionic formula for unrestricted Kostka polynomials. J. Comb. Theory Ser. A 113(7), 1435–1461 (2006)
Di Francesco, P., Kedem, R.: Proof of the combinatorial Kirillov–Reshetikhin conjecture. Int. Math. Res. Not. (7) Art. ID rnn006, 57 (2008)
Fourier, G., Okado, M., Schilling, A.: Kirillov–Reshetikhin crystals for nonexceptional types. Adv. Math. 222(3), 1080–1116 (2009)
Hernandez, D.: The Kirillov–Reshetikhin conjecture and solutions of \(T\)-systems. J. Reine Angew. Math. 596, 63–87 (2006)
Hatayama, G., Kuniba, A., Okado, M., Takagi, T., Yamada, Y.: Remarks on fermionic formula. In: Recent Developments in Quantum Affine Algebras and Related Topics (Raleigh, NC, 1998), Contemp. Math., vol. 248. Am. Math. Soc., Providence, RI, pp. 243–291 (1999)
Hatayama, G., Kuniba, A., Okado, M., Takagi, T., Tsuboi, Z.: Paths, crystals and fermionic formulae. In: MathPhys Odyssey, 2001, Prog. Math. Phys., vol. 23. Birkhäuser Boston, Boston, MA, pp. 205–272 (2002)
Kashiwara, M.: On crystal bases of the \(q\)-analogue of universal enveloping algebras. Duke Math. J. 63(2), 465–516 (1991)
Kashiwara, M.: Similarity of crystal bases. In: Lie Algebras and Their Representations (Seoul, 1995), Contemp. Math., vol. 194. Am. Math. Soc., Providence, RI, pp. 177–186 (1996)
Kang, S.-J., Kashiwara, M., Misra, K.C., Miwa, T., Nakashima, T., Nakayashiki, A.: Affine crystals and vertex models. In: Infinite Analysis, Part A, B (Kyoto, 1991), Adv. Ser. Math. Phys., vol. 16. World Sci. Publ., River Edge, NJ, pp. 449–484 (1992)
Kang, S.-J., Kashiwara, M., Misra, K.C., Miwa, T., Nakashima, Toshiki, Nakayashiki, Atsushi: Perfect crystals of quantum affine Lie algebras. Duke Math. J. 68(3), 499–607 (1992)
Kerov, S.V., Kirillov, A.N., Yu, N.: Reshetikhin. Combinatorics, the Bethe ansatz and representations of the symmetric group. Zap. Nauchn. Sem. Leningrad. Otdel. Mat. Inst. Steklov. (LOMI) 155(Differentsialnaya Geometriya, Gruppy Li i Mekh. VIII), 50–64, 193 (1986)
Kleber, M.S.: Finite Dimensional Representations of Quantum Affine Algebras. ProQuest LLC, Ann Arbor, MI. Thesis (Ph.D.)—University of California, Berkeley (1998)
Kashiwara, M., Nakashima, T.: Crystal graphs for representations of the \(q\)-analogue of classical Lie algebras. J. Algebra 165(2), 295–345 (1994)
Kuniba, A., Nakanishi, T., Tsuboi, Z.: The canonical solutions of the \(Q\)-systems and the Kirillov–Reshetikhin conjecture. Commun. Math. Phys. 227(1), 155–190 (2002)
Kuniba, A., Okado, M., Sakamoto, R., Takagi, T., Yamada, Yasuhiko: Crystal interpretation of Kerov–Kirillov–Reshetikhin bijection. Nuclear Phys. B 740(3), 299–327 (2006)
Kirillov, A.N., Yu, N.: Reshetikhin. The Bethe ansatz and the combinatorics of Young tableaux. Zap. Nauchn. Sem. Leningrad. Otdel. Mat. Inst. Steklov. (LOMI) 155(Differentsialnaya Geometriya, Gruppy Li i Mekh. VIII), 65–115, 194 (1986)
Kirillov, A.N., Reshetikhin, N.Y.: Representations of Yangians and multiplicities of the inclusion of the irreducible components of the tensor product of representations of simple Lie algebras. J. Sov. Math. 52, 3156–3164 (1990)
Kirillov, A.N., Schilling, A., Shimozono, M.: A bijection between Littlewood–Richardson tableaux and rigged configurations. Sel. Math. (N.S.) 8(1), 67–135 (2002)
Littelmann, P.: A Littlewood–Richardson rule for symmetrizable Kac–Moody algebras. Invent. Math. 116(1–3), 329–346 (1994)
Lecouvey, C., Okado, M., Shimozono, M.: \(X=K\) under review. In: Infinite Analysis 2010—Developments in Quantum Integrable Systems, RIMS Kôkyûroku Bessatsu, B28. Res. Inst. Math. Sci. (RIMS), Kyoto, pp. 155–164 (2011)
Lecouvey, C., Okado, M., Shimozono, M.: Affine crystals, one-dimensional sums and parabolic Lusztig \(q\)-analogues. Math. Z. 271(3–4), 819–865 (2012)
Lascoux, A., Schützenberger, M.-P.: Sur une conjecture de H. O. Foulkes. C. R. Acad. Sci. Paris Sér. A-B 286(7), A323–A324 (1978)
Nakajima, H.: \(t\)-analogs of \(q\)-characters of Kirillov–Reshetikhin modules of quantum affine algebras. Represent. Theory 7, 259–274 (2003). (electronic)
Naoi, K.: Fusion products of Kirillov–Reshetikhin modules and the \(X=M\) conjecture. Adv. Math. 231(3–4), 1546–1571 (2012)
Okado, M.: Existence of crystal bases for Kirillov–Reshetikhin modules of type \(D\). Publ. Res. Inst. Math. Sci. 43(4), 977–1004 (2007)
Okado, M.: Similarity and Kirillov-Schilling-Shimozono bijection. Algebr. Represent. Theor. 19(4), 975–989 (2016)
Okado, M., Schilling, A.: Existence of Kirillov–Reshetikhin crystals for nonexceptional types. Represent. Theory 12, 186–207 (2008)
Okado, M., Sano, N.: KKR type bijection for the exceptional affine algebra \(E_6^{(1)}\). In: Algebraic Groups and Quantum Groups. Contemp. Math., vol 565. Am. Math. Soc., Providence, RI, pp. 227–242 (2012)
Okado, M., Schilling, A., Shimozono, M.: A crystal to rigged configuration bijection for nonexceptional affine algebras. In: Algebraic Combinatorics and Quantum Groups. World Sci. Publ., River Edge, NJ, pp. 85–124 (2003)
Okado, M., Schilling, A., Shimozono, M.: Virtual crystals and fermionic formulas of type \(D^{(2)}_{n+1},A^{(2)}_{2n}\), and \(C^{(1)}_n\). Represent. Theory 7, 101–163 (2003). (electronic)
Okado, M., Schilling, A., Shimozono, M.: Virtual crystals and Kleber’s algorithm. Commun. Math. Phys. 238(1–2), 187–209 (2003)
Okado, M., Sakamoto, R., Schilling, A.: Affine crystal structure on rigged configurations of type \(D_n^{(1)}\). J. Algebraic Comb. 37(3), 571–599 (2013)
Sakamoto, R.: Mathematica implementation of rigged configurations. https://sites.google.com/site/affinecrystal/rigged-configurations
Sakamoto, R.: Rigged configurations and Kashiwara operators. SIGMA Symmetry Integra. Geom. Methods Appl. 10, Paper 028, 88 (2014)
Schilling, A.: A bijection between type \(D^{(1)}_n\) crystals and rigged configurations. J. Algebra 285(1), 292–334 (2005)
Schilling, A.: Crystal structure on rigged configurations. Int. Math. Res. Not., Art. ID 97376, 27 (2006)
Schilling, A.: Combinatorial structure of Kirillov–Reshetikhin crystals of type \(D^{(1)}_n, B^{(1)}_n, A^{(2)}_{2n-1}\). J. Algebra 319(7), 2938–2962 (2008)
Scrimshaw, T.: A crystal to rigged configuration bijection and the filling map for type \(D_4^{(3)}\). J. Algebra 448C, 294–349 (2016)
Schilling, A., Shimozono, M.: \(X=M\) for symmetric powers. J. Algebra 295(2), 562–610 (2006)
Schilling, A., Scrimshaw, T.: Crystal structure on rigged configurations and the filling map. Electron. J. Comb. 22(1), Paper 1.73, 56 (2015)
Takahashi, D., Satsuma, J.: A soliton cellular automaton. J. Phys. Soc. Jpn. 59(10), 3514–3519 (1990)
The Sage Developers. Sage Mathematics Software (Version 6.9) (2015). http://www.sagemath.org
The Sage-Combinat community. Sage-Combinat: enhancing Sage as a toolbox for computer exploration in algebraic combinatorics (2008). http://combinat.sagemath.org
Acknowledgements
This work benefited from computations in SageMath [45, 46] (using implementations of crystals and rigged configurations by Schilling and Scrimshaw) and Mathematica (using an implementation of rigged configurations by Sakamoto [36]). AS and TS would like to thank Osaka City University for kind hospitality during their stay in July 2015. Both authors were partially supported by the JSPS Program for Advancing Strategic International Networks to Accelerate the Circulation of Talented Researchers “Mathematical Science of Symmetry, Topology and Moduli, Evolution of International Research Network based on OCAMI.” MO was partially supported by the Grants-in-Aid for Scientific Research No. 23340007 and No. 15K13429 from JSPS. The work of RS was partially supported by Grants-in-Aid for Scientific Research No. 25800026 from JSPS. AS was partially supported by NSF grants OCI–1147247 and DMS–1500050. TS was partially supported by NSF Grant OCI–1147247 and RTG Grant NSF/DMS–1148634.
Author information
Authors and Affiliations
Corresponding author
Appendix: Example of the rigged configuration bijection
Appendix: Example of the rigged configuration bijection
In this section, we provide an example of the algorithm \(\Phi ^{-1}\). The reader may easily infer from the following example the meaning of the correspondence between the operators summarized in Table 1.
Example 7.1
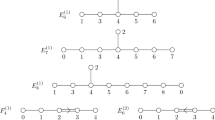
Consider the unrestricted rigged configuration \(r_1 \in {\text {RC}}(L(B))\) for \(B=B^{3,2}\otimes B^{3,3}\otimes B^{2,3}\) of type \(D^{(1)}_5\):

In the above diagram, we show the partition \(\mu ^{(a)}\) as defined in Sect. 3.1 over the corresponding rigged partition \((\nu ^{(a)},J^{(a)})\) in order to make it easier to see the operations \(\gamma \) and \(\beta \). In \(\Phi ^{-1}\), let us remove the \(B^{3,2}\) part first. We begin by applying \(\gamma \) and obtain \(r_2{:}{=}\gamma (r_1)\) which looks as follows:

The changes are the shape of \(\mu ^{(3)}\) and the resulting change of the vacancy numbers for \(P^{(3)}_1(\nu )\) which makes the length 1 strings of \((\nu ,J)^{(3)}\) non-singular.Footnote 1 This operation corresponds to
Then \(r_3{:}{=}\beta (r_2)\) looks as follows:

This corresponds to
Note that the vacancy numbers for \(\nu ^{(3)}\) do not change. Since \(\beta \) adds length 1 singular strings to \((\nu ,J)^{(1)}\) and \((\nu ,J)^{(2)}\), applying \(\delta \) removes the boxes with “\(\times \)” in the above diagram.Footnote 2 Then \(\delta \) gives the following rigged configuration \(r_4{:}{=}\delta (r_3)\) together with the output letter \(\overline{5}\) which fills the bottom left corner of \(B^{3,2}\) as

.

Since the above \(\delta \) determines \(B^{1,1}\) of (7.2), we start to apply \(\gamma \), \(\beta \), and \(\delta \) corresponding to \(B^{2,1}\) of (7.2). Since \(\gamma (r_4) = r_4\), the unrestricted rigged configuration \(r_5 {:}{=} \beta (r_4)\) looks as follows:

This corresponds to
Then \(\delta \) removes the boxes with “\(\times \)” in the above diagram which determines one of \(B^{1,1}\) in (7.3). As the result, we obtain the following unrestricted rigged configuration \(r_6{:}{=}\delta (r_5)\) and the output letter within \(B^{3,2}\) as

:

The next \(\delta \) removes the box with “\(\times \)” in the above diagram and determines the remaining \(B^{1,1}\) in (7.3). As the result, we obtain the following unrestricted rigged configuration \(r_7 {:}{=} \delta (r_6)\) and the output letter within \(B^{3,2}\) as

:

Next we determine the remaining \(B^{3,1}\) in (7.1). \(r_8 = (\delta \circ \beta )(r_7)\) is the following unrestricted rigged configuration with the output letter in \(B^{2,3}\) as

:

\(r_9 = (\delta \circ \beta )(r_8)\) is the following unrestricted rigged configuration with the output letter in \(B^{2,3}\) as

:

\(r_{10} = \delta (r_9)\) is the following unrestricted rigged configuration with the output letter in \(B^{2,3}\) as

:

For the KN tableau representation of the rectangular tableau, we need to apply the inverse of the filling map of Definition 2.5 to obtain

. If we further determine \(B^{3,3}\) and \(B^{2,3}\) in this order, we obtain the empty rigged configuration and the following path

Summary As we see in the above example, the algorithm \(\Phi ^{-1}\) is recursively defined as follows. Suppose that we consider the unrestricted rigged configuration \((\nu ,J)\) associated with the tensor product of type
Then we determine \(b\in B^{r,s}\) by the following procedure. In correspondence with the operation
we apply \(\gamma \) to the unrestricted rigged configuration. Then apply \({\text {lb}}\) on \(B^{r,1}\) in (7.4)
which on the rigged configuration side corresponds to \(\beta \). Finally we use \({\text {lh}}\) and \(\delta \) to remove \(B^{1,1}\) of (7.5). In order to process the remaining \(B^{r-1,1}\) of (7.5), we apply \(\beta \) and \(\delta \) repeatedly for \((r-1)\)-times. We fill the leftmost column of \(B^{r,s}\) from bottom to top by the letters obtained by \(\delta \) during this procedure. In order to determine the remaining \(B^{r,s-1}\) of (7.4), we repeat the same procedure for the first column and fill the remaining columns of \(B^{r,s}\) from left to right. Once \(B^{r,s}\) is fully determined, we proceed to the leftmost rectangle of \(B'\) and repeat the same procedure used for \(B^{r,s}\). In this manner, we obtain the filling of shape B, which we denote by \(b\in B\). Then we define
The inverse procedure \(\Phi \) is obtained by reversing all the steps of \(\Phi ^{-1}\).
Rights and permissions
About this article
Cite this article
Okado, M., Sakamoto, R., Schilling, A. et al. Type \({{\varvec{D}}}_{{\varvec{n}}}^\mathbf{(1)}\) rigged configuration bijection. J Algebr Comb 46, 341–401 (2017). https://doi.org/10.1007/s10801-017-0756-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10801-017-0756-4