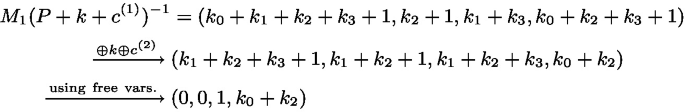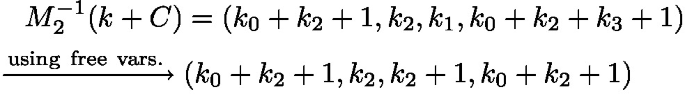Abstract
Picnic is a NIST PQC Round 3 Alternate signature candidate that builds upon symmetric primitives following the MPC-in-the-head paradigm. Recently, researchers have been exploring more secure/efficient signature schemes from conservative one-way functions based on AES, or new low-complexity one-way functions like Rain (CCS 2022) and AIM (CCS 2023 and Round 1 Additional Signatures announced by NIST PQC). The signature schemes based on Rain and AIM are currently the most efficient among MPC-in-the-head-based schemes, making them promising post-quantum digital signature candidates.
However, the exact hardness of these new one-way functions deserves further study and scrutiny. This work presents algebraic attacks on Rain and AIM for certain instances, where one-round Rain can be compromised in \(2^{n/2}\) for security parameter \(n\in \{128,192,256\}\), and two-round Rain can be broken in \(2^{120.3}\), \(2^{180.4}\), and \(2^{243.1}\) encryptions, respectively. Additionally, we demonstrate an attack on AIM-III (which aims at 192-bit security) with a complexity of \(2^{186.5}\) encryptions. These attacks exploit the algebraic structure of the power function over fields with characteristic 2, which provides potential insights into the algebraic structures of some symmetric primitives and thus might be of independent interest.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
- 2.
The one-wayness of \(H(k) = E_k(P)\) is equivalent to the key recovery security of E with a single plaintext/ciphertext pair: see [20] for a proof.
- 3.
- 4.
We refer interested readers to a faster implementation utilizing SIMD instructions for Rain (https://github.com/IAIK/rainier-signatures).
References
Albrecht, M.R., et al.: Algebraic cryptanalysis of STARK-friendly designs: application to MARVELlous and MiMC. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019, Part III. LNCS, vol. 11923, pp. 371–397. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-34618-8_13
Albrecht, M., Grassi, L., Rechberger, C., Roy, A., Tiessen, T.: MiMC: efficient encryption and cryptographic hashing with minimal multiplicative complexity. In: Cheon, J.H., Takagi, T. (eds.) ASIACRYPT 2016, Part I. LNCS, vol. 10031, pp. 191–219. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53887-6_7
Aly, A., Ashur, T., Ben-Sasson, E., Dhooghe, S., Szepieniec, A.: Design of symmetric-key primitives for advanced cryptographic protocols. IACR Trans. Symm. Cryptol. 2020(3), 1–45 (2020). https://doi.org/10.13154/tosc.v2020.i3.1-45
Ashur, T., Dhooghe, S.: MARVELlous: a STARK-friendly family of cryptographic primitives. Cryptology ePrint Archive, Report 2018/1098 (2018). https://eprint.iacr.org/2018/1098
Banik, S., Barooti, K., Vaudenay, S., Yan, H.: New attacks on LowMC instances with a single plaintext/ciphertext pair. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021, Part I. LNCS, vol. 13090, pp. 303–331. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92062-3_11
Baum, C., de Saint Guilhem, C.D., Kales, D., Orsini, E., Scholl, P., Zaverucha, G.: Banquet: short and fast signatures from AES. In: Garay, J.A. (ed.) PKC 2021, Part I. LNCS, vol. 12710, pp. 266–297. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-75245-3_11
Chase, M., et al.: Post-quantum zero-knowledge and signatures from symmetric-key primitives. In: Thuraisingham, B.M., Evans, D., Malkin, T., Xu, D. (eds.) ACM CCS 2017, pp. 1825–1842. ACM Press (2017). https://doi.org/10.1145/3133956.3133997
Cheon, J.H., Lee, D.H.: Resistance of S-boxes against algebraic attacks. In: Roy, B., Meier, W. (eds.) FSE 2004. LNCS, vol. 3017, pp. 83–93. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-25937-4_6
Coppersmith, D., Winograd, S.: Matrix multiplication via arithmetic progressions. In: Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, pp. 1–6 (1987)
Courtois, N., Debraize, B., Garrido, E.: On exact algebraic [non-]immunity of S-boxes based on power functions. In: Batten, L.M., Safavi-Naini, R. (eds.) ACISP 06. LNCS, vol. 4058, pp. 76–86. Springer, Heidelberg (Jul (2006)
Courtois, N., Klimov, A., Patarin, J., Shamir, A.: Efficient algorithms for solving overdefined systems of multivariate polynomial equations. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 392–407. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-45539-6_27
Courtois, N.T., Pieprzyk, J.: Cryptanalysis of block ciphers with overdefined systems of equations. In: Zheng, Y. (ed.) ASIACRYPT 2002. LNCS, vol. 2501, pp. 267–287. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-36178-2_17
Daemen, J.: Limitations of the even-Mansour construction. In: Imai, H., Rivest, R.L., Matsumoto, T. (eds.) ASIACRYPT 1991. LNCS, vol. 739, pp. 495–498. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-57332-1_46
de Saint Guilhem, C.D., De Meyer, L., Orsini, E., Smart, N.P.: BBQ: using AES in picnic signatures. In: Paterson, K.G., Stebila, D. (eds.) SAC 2019. LNCS, vol. 11959, pp. 669–692. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-38471-5_27
de Saint Guilhem, C., Orsini, E., Tanguy, T.: Limbo: efficient zero-knowledge MPCitH-based arguments. In: Vigna, G., Shi, E. (eds.) ACM CCS 2021, pp. 3022–3036. ACM Press (2021). https://doi.org/10.1145/3460120.3484595
Dinur, I., Dunkelman, O., Keller, N., Shamir, A.: Key recovery attacks on 3-round Even-Mansour, 8-step LED-128, and full AES2. In: Sako, K., Sarkar, P. (eds.) ASIACRYPT 2013, Part I. LNCS, vol. 8269, pp. 337–356. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-42033-7_18
Dinur, I., Dunkelman, O., Keller, N., Shamir, A.: Cryptanalysis of iterated even-Mansour schemes with two keys. In: Sarkar, P., Iwata, T. (eds.) ASIACRYPT 2014, Part I. LNCS, vol. 8873, pp. 439–457. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-45611-8_23
Dinur, I., Liu, Y., Meier, W., Wang, Q.: Optimized interpolation attacks on LowMC. In: Iwata, T., Cheon, J.H. (eds.) ASIACRYPT 2015, Part II. LNCS, vol. 9453, pp. 535–560. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48800-3_22
Dobraunig, C., Eichlseder, M., Mendel, F.: Higher-order cryptanalysis of LowMC. In: Kwon, S., Yun, A. (eds.) ICISC 2015. LNCS, vol. 9558, pp. 87–101. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-30840-1_6
Dobraunig, C., Kales, D., Rechberger, C., Schofnegger, M., Zaverucha, G.: Shorter signatures based on tailor-made minimalist symmetric-key crypto. In: Yin, H., Stavrou, A., Cremers, C., Shi, E. (eds.) ACM CCS 2022, pp. 843–857. ACM Press (2022). https://doi.org/10.1145/3548606.3559353
Dunkelman, O., Keller, N., Shamir, A.: Slidex attacks on the Even-Mansour encryption scheme. J. Cryptol. 28(1), 1–28 (2015). https://doi.org/10.1007/s00145-013-9164-7
Gupta, K.C., Ray, I.G.: Finding biaffine and quadratic equations for s-boxes based on power mappings. IEEE Trans. Inf. Theory 61(4), 2200–2209 (2015). https://doi.org/10.1109/TIT.2014.2387052
Hülsing, A., et al.: SPHINCS+. Technical report, National Institute of Standards and Technology (2022). https://csrc.nist.gov/Projects/post-quantum-cryptography/selected-algorithms-2022
Ishai, Y., Kushilevitz, E., Ostrovsky, R., Sahai, A.: Zero-knowledge from secure multiparty computation. In: Johnson, D.S., Feige, U. (eds.) 39th ACM STOC, pp. 21–30. ACM Press (2007). https://doi.org/10.1145/1250790.1250794
Katz, J., Kolesnikov, V., Wang, X.: Improved non-interactive zero knowledge with applications to post-quantum signatures. In: Lie, D., Mannan, M., Backes, M., Wang, X. (eds.) ACM CCS 2018, pp. 525–537. ACM Press (2018). https://doi.org/10.1145/3243734.3243805
Kim, S., et al.: AIM: symmetric primitive for shorter signatures with stronger security. Cryptology ePrint Archive, Report 2022/1387 (2022). https://eprint.iacr.org/2022/1387
Kipnis, A., Shamir, A.: Cryptanalysis of the HFE public key cryptosystem by relinearization. In: Wiener, M. (ed.) CRYPTO 1999. LNCS, vol. 1666, pp. 19–30. Springer, Heidelberg (1999). https://doi.org/10.1007/3-540-48405-1_2
Liu, F., Isobe, T., Meier, W.: Cryptanalysis of full LowMC and LowMC-M with algebraic techniques. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12827, pp. 368–401. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84252-9_13
Liu, F., Mahzoun, M.: Algebraic attacks on RAIN and AIM using equivalent representations. IACR Cryptol. ePrint Arch. p. 1133 (2023). https://eprint.iacr.org/2023/1133
Liu, F., Meier, W., Sarkar, S., Isobe, T.: New low-memory algebraic attacks on LowMC in the Picnic setting. IACR Trans. Symm. Cryptol. 2022(3), 102–122 (2022). https://doi.org/10.46586/tosc.v2022.i3.102-122
Liu, F., Sarkar, S., Meier, W., Isobe, T.: Algebraic attacks on rasta and dasta using low-degree equations. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021, Part I. LNCS, vol. 13090, pp. 214–240. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92062-3_8
Liu, F., Sarkar, S., Wang, G., Meier, W., Isobe, T.: Algebraic meet-in-the-middle attack on LowMC. In: Agrawal, S., Lin, D. (eds.) ASIACRYPT 2022, Part I. LNCS, vol. 13791, pp. 225–255. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-22963-3_8
Lyubashevsky, V., et al.: CRYSTALS-DILITHIUM. Technical report, National Institute of Standards and Technology (2022). https://csrc.nist.gov/Projects/post-quantum-cryptography/selected-algorithms-2022
Mullen, G.L., Panario, D.: Handbook of Finite Fields. CRC Press, Boca Raton (2013)
Nawaz, Y., Gupta, K.C., Gong, G.: Algebraic immunity of s-boxes based on power mappings: analysis and construction. IEEE Trans. Inf. Theory 55(9), 4263–4273 (2009). https://doi.org/10.1109/TIT.2009.2025534
Nikolić, Ivica, Wang, Lei, Wu, Shuang: Cryptanalysis of round-reduced LED. In: Moriai, Shiho (ed.) FSE 2013. LNCS, vol. 8424, pp. 112–129. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-43933-3_7
Prest, T., et al.: FALCON. Technical report, National Institute of Standards and Technology (2022), available at https://csrc.nist.gov/Projects/post-quantum-cryptography/selected-algorithms-2022
Rechberger, C., Soleimany, H., Tiessen, T.: Cryptanalysis of low-data instances of full LowMCv2. IACR Trans. Symm. Cryptol. 2018(3), 163–181 (2018). https://doi.org/10.13154/tosc.v2018.i3.163-181
Srivastava, V., Baksi, A., Debnath, S.K.: An overview of hash based signatures. IACR Cryptol. ePrint Arch. p. 411 (2023). https://eprint.iacr.org/2023/411
Strassen, V., et al.: Gaussian elimination is not optimal. Numer. Math. 13(4), 354–356 (1969)
Acknowledgments
Yu Yu was supported by the National Key Research and Development Program of China (Grant No. 2020YFA0309705) and the National Natural Science Foundation of China (Grant Nos. 62125204 and 92270201). This work was also supported in part by the National Key Research and Development Program of China (Grant No. 2018YFA0704701) and the Major Program of Guangdong Basic and Applied Research (Grant No. 2019B030302008). This work has been supported by the New Cornerstone Science Foundation through the XPLORER PRIZE.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Toy Examples of Attacks on Reduced-Round Rain
A Toy Examples of Attacks on Reduced-Round Rain
In this section, we concretely present toy examples for one-round Rain and two-round Rain, which would help the readers understand our attacks via examples. We choose the field \(\mathbb F _{2^4}\) with irreducible polynomial \(f(x)=x^4+x+1\).
Notation. For an element \(a_0+a_1x+a_2x^2+a_3x^3\) of field \(\mathbb F _{2^4}\), \(a_i\in \mathbb F _2\), we may express it in several equivalent forms:
-
1.
Polynomial representation, i.e. \(a_0+a_1x+a_2x^2+a_3x^3\).
-
2.
Binary representation, i.e. \(a_0a_1a_2a_3\).
-
3.
Vector of \(\mathbb F _2\), i.e. \((a_0,a_1,a_2,a_3)\)
Concretely, \(1+x+x^3\) is equivalent to 1101 or (1, 1, 0, 1). And 1 is equivalent to 1000 or (1, 0, 0, 0). We also use the notation \((1,1,0,1)^2=(1+x+x^3)^2=1+x^3=(1,0,0,1)\)
Power Function. We first show the square function over \(\mathbb F _{2^4}\) is linear.
So we can use the notation \((a_0,a_1,a_2,a_3)^2=(a_0+a_2,a_2,a_1+a_3,a_3)\). Similarly, we can have \((a_0,a_1,a_2,a_3)^4=(a_0+a_1+a_2+a_3,a_1+a_3,a_2+a_3,a_3)\).
Parameter Sets. We choose \(P=0000,c^{(1)}=0010,c^{(2)}=0001,k=0100\) and
For convenience, we precompute some values and list them on Table 6. Let \(d=3\). As you can see, \(x^d,x\ne 0\) takes only \(15/3=5\) possible choices.
1.1 A.1 One-Round Rain
The encryption of one-round Rain (Fig. 6) is :
We guess the value of \((P+k+c^{(1)})^3\) over \((2^4-1)/3=5\) possible choices. Suppose we guess \((P+k+c^{(1)})^3=1\). The following steps will be repeated for each guess, here we only show the execution for the correct guess which is \((P+k+c^{(1)})^3=1\). So we have
By solving the linear equations, we can obtain two candidate keys \(k^*=0100\) and \(k^{**}=0010\). Given the public input P and output C, it is easy to check by executing the one-round encryption in Eq. (6) that \(k^*\) is the correct key.
1.2 A.2 Two-Round Rain
We follow the notations and the parameter choices as in the attack on one-round Rain. The encryption of two-round Rain (Fig. 7) is :

-
We linearize the first S-box by guessing \((P+k+c^{(1)})^3=1\) as in the previous attack on one-round. Then we have the following linear equations:
$$\begin{aligned} 0 & =(P+k+c^{(1)})^4 + (P+k+c^{(1)}) \\ & = (k_0,k_1,k_2+1,k_3)^4 + (k_0,k_1,k_2+1,k_3) \\ & = (k_0+k_1+k_2+k_3+1,k_1+k_3,k_2+k_3+1,k_3) + (k_0,k_1,k_2+1,k_3) \\ & = (k_1+k_2+k_3+1,k_3,k_3,0) \end{aligned}$$This gives us two linearly independent equations:
$$ \left\{ \begin{array}{rl} k_1+k_2&{}=1\\ k_3&{}=0\\ \end{array} \right. $$Consequently, we can decide on two free variables \(k_0,k_2\) and two basic variables \(k_1=k_2+1,k_3=0\).
-
Next, we compute the input of the second S-box \(M_1(P+k+c^{(1)})^{-1}\). Substituting \(M_1\) as we choose and substituting the expression of \((P+k+c^{(1)})^{-1}\) as in Eq. (7), we get the following
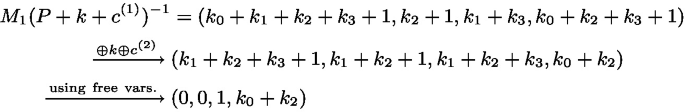
Backward, represent the output of the second S-box and we have
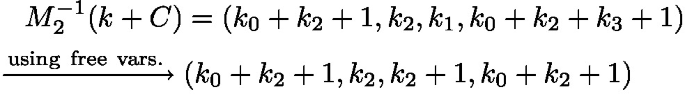
Because the multiplication of the input and the output of the second S-box equals 1, thus we can write down the following quadratic equations:
$$\begin{aligned} (0,0,1,k_0+k_2)\cdot (k_0+k_2+1,k_2,k_2+1,k_0+k_2+1) &= 1\\ \rightarrow (k_0k_2+1,k_2,k_0k_2+k_0,k_2)&= 1 \end{aligned}$$By solving the linear equation, we can obtain a candidate key \(k^*=0100\). Given the public input P and the output C, it is easy to check that \(k^*\) is the correct key by executing two-round Rain encryption.
Rights and permissions
Copyright information
© 2023 International Association for Cryptologic Research
About this paper
Cite this paper
Zhang, K., Wang, Q., Yu, Y., Guo, C., Cui, H. (2023). Algebraic Attacks on Round-Reduced Rain and Full AIM-III. In: Guo, J., Steinfeld, R. (eds) Advances in Cryptology – ASIACRYPT 2023. ASIACRYPT 2023. Lecture Notes in Computer Science, vol 14440. Springer, Singapore. https://doi.org/10.1007/978-981-99-8727-6_10
Download citation
DOI: https://doi.org/10.1007/978-981-99-8727-6_10
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-8726-9
Online ISBN: 978-981-99-8727-6
eBook Packages: Computer ScienceComputer Science (R0)