Abstract
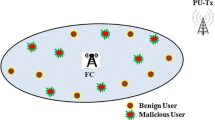
Cognitive radio has emerged as a promising technology aimed at improving allocated spectrum utilization and alleviating spectrum shortage through opportunistic spectrum usage, which has been widely studied due to its strong robustness and high reliability. However, its vulnerability to potential attacks raises security issues. Extensive researches have focused on how to alleviate the negative effect of the malicious attack on cooperative spectrum sensing. This paper first briefly discusses the models of cooperative spectrum sensing, fading channel, and malicious attack, then further illustrates the influence of fading and malicious users on cooperative spectrum sensing in detail. Motivated by the above analysis, we propose a robust modified outlier removal (MOR) spectrum sensing scheme. Before data fusion, the fusion center conditionally removes outlier which is most likely tampered by the malicious user. Through several simulations, we compare and analyze the proposed scheme with the traditional scheme to verify its correctness and feasibility. Simulation results show that the proposed scheme has a high defense under various sensing environments and different attack strengths. The proposed scheme can resist malicious users and improve detection performance more effectively than the traditional scheme.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Akyildiz, I., Lo, B.F., Balakrishnan, R.: Cooperative spectrum sensing in cognitive radio networks: a survey. Phys. Commun. 4(1), 40–62 (2011)
Ali, A., Hamouda, W.: Advances on spectrum sensing for cognitive radio networks: theory and applications. IEEE Commun. Surv. Tutorials 19(2), 1277–1304 (2017). https://doi.org/10.1109/COMST.2016.2631080
Banerjee, A., Maity, S.P.: Jamming in eavesdropping on throughput maximization in green cognitive radio networks. IEEE Trans. Mob. Comput. 22(1), 299–310 (2023). https://doi.org/10.1109/TMC.2021.3068797
Bera, D., Chakrabarti, I., Pathak, S.S., Karagiannidis, G.K.: Another look in the analysis of cooperative spectrum sensing over nakagami- \(m\) fading channels. IEEE Trans. Wireless Commun. 16(2), 856–871 (2017). https://doi.org/10.1109/TWC.2016.2633259
Gao, R., Zhang, Z., Zhang, M., Yang, J., Qi, P.: A cooperative spectrum sensing scheme in malicious cognitive radio networks. In: 2019 IEEE Globecom Workshops (GC Wkshps), pp. 1–5 (2019). https://doi.org/10.1109/GCWkshps45667.2019.9024531
Godugu, K.K., Vappangi, S.: Performance analysis of Wideband Spectrum Sensing (WSS) in Cognitive Radio Networks (CRN) over erroneous sensing and reporting channels, pp. 1–6 (2022). https://doi.org/10.1109/ASIANCON55314.2022.9908624
López-Benítez, M., Casadevall, F.: Improved energy detection spectrum sensing for cognitive radio. IET Commun. 6(8), 785–796 (2012)
Pei, Q., Li, H., Liu, X.: Neighbor detection-based spectrum sensing algorithm in distributed cognitive radio networks. Chin. J. Electron. 26(2), 399–406 (2017)
Rahaman, M.F., Khan, M.Z.A.: Low-complexity optimal hard decision fusion under the Neyman-Pearson criterion. IEEE Signal Process. Lett. 25(3), 353–357 (2018). https://doi.org/10.1109/LSP.2017.2766245
Rathee, G., Jaglan, N., Garg, S., Choi, B.J., Choo, K.K.R.: A secure spectrum handoff mechanism in cognitive radio networks. IEEE Trans. Cognitive Commun. Networking 6(3), 959–969 (2020). https://doi.org/10.1109/TCCN.2020.2971703
Rawat, A.S., Anand, P., Chen, H., Varshney, P.K.: Collaborative spectrum sensing in the presence of byzantine attacks in cognitive radio networks. IEEE Trans. Signal Process. 59(2), 774–786 (2011). https://doi.org/10.1109/TSP.2010.2091277
Umar, R., Sheikh, A.U.H., Deriche, M.: Unveiling the hidden assumptions of energy detector based spectrum sensing for cognitive radios. IEEE Commun. Surv. Tutorials 16(2), 713–728 (2014). https://doi.org/10.1109/SURV.2013.081313.00054
Wu, J., et al.: Analysis of byzantine attack strategy for cooperative spectrum sensing. IEEE Commun. Lett. 24(8), 1631–1635 (2020). https://doi.org/10.1109/LCOMM.2020.2990869
Xu, M., et al.: Early warning of lithium battery progressive fault based on box plot. In: 2019 3rd International Conference on Electronic Information Technology and Computer Engineering (EITCE), pp. 1072–1075 (2019)
Ye, F., Zhang, X., Li, Y., rui Tang, C.: Faithworthy collaborative spectrum sensing based on credibility and evidence theory for cognitive radio networks. Symmetry 9(3), 36 (2017)
Zhang, L., Ding, G., Wu, Q., Zou, Y., Han, Z., Wang, J.: Byzantine attack and defense in cognitive radio networks: a survey. IEEE Commun. Surv. Tutorials 17(3), 1342–1363 (2015). https://doi.org/10.1109/COMST.2015.2422735
Zhang, L., Nie, G., Ding, G., Wu, Q., Zhang, Z., Han, Z.: Byzantine attacker identification in collaborative spectrum sensing: a robust defense framework. IEEE Trans. Mob. Comput. 18(9), 1992–2004 (2019). https://doi.org/10.1109/TMC.2018.2869390
Zhang, L., Wu, Q., Ding, G., Feng, S., Wang, J.: Performance analysis of probabilistic soft SSDF attack in cooperative spectrum sensing. EURASIP J. Adv. Signal Process. 2014(1), 1–9 (2014)
Acknowledgments
This work was supported by the National Natural Science Foundation of China under Grant 201011348.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Guo, L., Chen, W., Cong, Y., Yan, X. (2023). A Robust MOR-Based Secure Fusion Strategy Against Byzantine Attack in Cooperative Spectrum Sensing. In: Chen, H., Fan, P., Wang, L. (eds) Communications, Networking, and Information Systems. CNIS 2023. Communications in Computer and Information Science, vol 1839. Springer, Singapore. https://doi.org/10.1007/978-981-99-3581-9_6
Download citation
DOI: https://doi.org/10.1007/978-981-99-3581-9_6
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-3580-2
Online ISBN: 978-981-99-3581-9
eBook Packages: Computer ScienceComputer Science (R0)